
February 13, 2026
Azure Migration Edmonton: An Expert Guide to a Seamless Cloud TransitionAzure migration Edmonton: Plan, secure, and optimize your cloud move with practical steps, cost control, and security best practices.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
February 14, 2026

For Edmonton businesses, effective network security isn't about buying a generic, off-the-shelf product. It's about building a defence strategy that understands the real-world threats targeting our local industries—from manufacturing and healthcare to the energy sector right here in Alberta.
Trying to get your head around cybersecurity can feel like a massive task. It’s complex, constantly changing, and the stakes for your business are incredibly high. Many Edmonton businesses operate in a unique economic climate, facing threats designed specifically for local industries.
Think of your network security as the digital blueprint for your business's fortress. A physical building in Edmonton needs extra protection to stand up to our harsh winters. In the same way, your digital infrastructure requires a defence strategy built for its specific environment, not a one-size-fits-all solution from somewhere else.
This guide cuts through the generic advice to focus on the real cyber risks local businesses face. We'll lay out a clear, practical path to building a security posture that truly protects your assets, reputation, and future.
Today’s cyberattacks aren't random; they're sophisticated, profit-driven operations. Attackers deliberately target small and medium-sized businesses (SMBs), betting they have fewer resources dedicated to security.
For an Edmonton-based company, this might look like a phishing email cleverly disguised as an invoice from a familiar local supplier. Or it could be a ransomware attack targeting the operational technology common in our manufacturing sector.
The fallout from a breach goes far beyond financial loss. A successful attack can cripple your business in multiple ways:
A proactive security strategy isn't just about defence—it's about ensuring business continuity. When you anticipate threats and build smart defences, security stops being a cost centre and becomes a competitive advantage that builds client trust and keeps you running smoothly.
So, why is a local focus so critical for network security in Edmonton? A provider who understands the regional business landscape simply gets it. They know the specific compliance headaches you face, recognize common local threats, and can respond much faster when something goes wrong.
This localized expertise is key to creating a security plan that’s both effective and relevant to how you do business.
A generic solution often misses the critical nuances of local industry regulations and business practices. For a closer look at getting your IT fundamentals right, this comprehensive IT checklist for businesses in Edmonton is a great starting point for building a strong foundation.
Ultimately, building a rock-solid security posture is a marathon, not a sprint. It demands a clear-eyed view of your specific risks and a real commitment to continuous improvement. In the sections ahead, we’ll break down the biggest threats and give you actionable steps to fortify your defences.
Of all the cyber threats facing local companies, ransomware is one of the most disruptive and financially devastating. Think of it as a digital saboteur who sneaks in overnight, changes the locks on your entire facility, and demands a massive payment for the new keys.
It’s a digital hostage situation. Criminals seize your most valuable asset—your data—and hold it captive with powerful encryption. For Edmonton's core industries, from oil and gas to legal and healthcare, the stakes couldn't be higher.
An attack on an oil firm's operational technology can grind production to a halt for days. A breach at a healthcare clinic could expose sensitive patient files, triggering massive fines and shattering patient trust forever. The damage goes far beyond the data; it freezes your entire operation.
Ransomware attacks are not random acts of vandalism; they are calculated, methodical operations. Cybercriminals typically slip in through common, often overlooked, weak spots in a company's defences.
The playbook usually looks something like this:
This entire nightmare can unfold in minutes, leaving your business paralyzed. Attackers bank on the intense pressure of downtime to force a quick payment, but handing over the money is no guarantee you will ever see your data again.
Why are Edmonton businesses squarely in the crosshairs? It’s simple: our city’s economic strengths are exactly what cybercriminals look for. Industries like manufacturing, legal services, and oil and gas depend on non-stop operations and handle highly sensitive data, making any disruption incredibly painful and costly.
The numbers tell a story that should concern every local business leader. As the network security Edmonton landscape grows more hostile, ransomware has become Alberta's most urgent threat.
The recent surge in cyber incidents across Alberta highlights a growing risk that local businesses can no longer afford to ignore. The data reveals a clear and troubling trend.
As these figures show, the threat is not just growing—it's accelerating. This makes proactive defence and a solid response plan more critical than ever.
The financial cost of a ransomware attack is just the beginning. The true damage lies in the loss of productivity, customer trust, and the long-term harm to your brand's reputation.
The consequences of a successful ransomware attack ripple through every part of a business. Beyond the ransom itself, companies face a tidal wave of hidden costs and long-term headaches. To better understand this growing menace, you can find helpful resources on the Rise of Ransomware Attacks.
The aftermath typically includes:
Building a robust defence is no longer optional; it’s essential for survival. For a deeper dive into specific defensive strategies, check out our guide on effective ransomware protection for Edmonton businesses. In this fight, being proactive is the only reliable way to protect your operations.
How do you build a security system that stands up to today's threats? It’s not about finding one magic solution. It's about building layers of protection that work together, much like fortifying a castle. This multi-layered approach, often handled by a dedicated partner, is the bedrock of a modern, resilient defence strategy.
Let's walk through the essential services that create this digital fortress. We will break down each piece in simple, practical terms to show how they strengthen your network security in Edmonton, making sure your business is covered from every angle.
Think of 24/7 network monitoring as a tireless digital watchtower for your business. Security experts remain on guard around the clock, scanning every corner of your network for suspicious activity, intruders, or early signs of trouble. This isn't a 9-to-5 job; threats appear at all hours, and constant vigilance is the only way to catch them before they do real damage.
This proactive oversight means potential issues are identified and shut down before they escalate into full-blown disasters like data theft or an operational shutdown. It’s the difference between spotting smoke and calling the fire department for a four-alarm blaze.
The infographic below shows just how quickly risks cascade from a single ransomware attack, which is why stopping that initial breach is so critical.
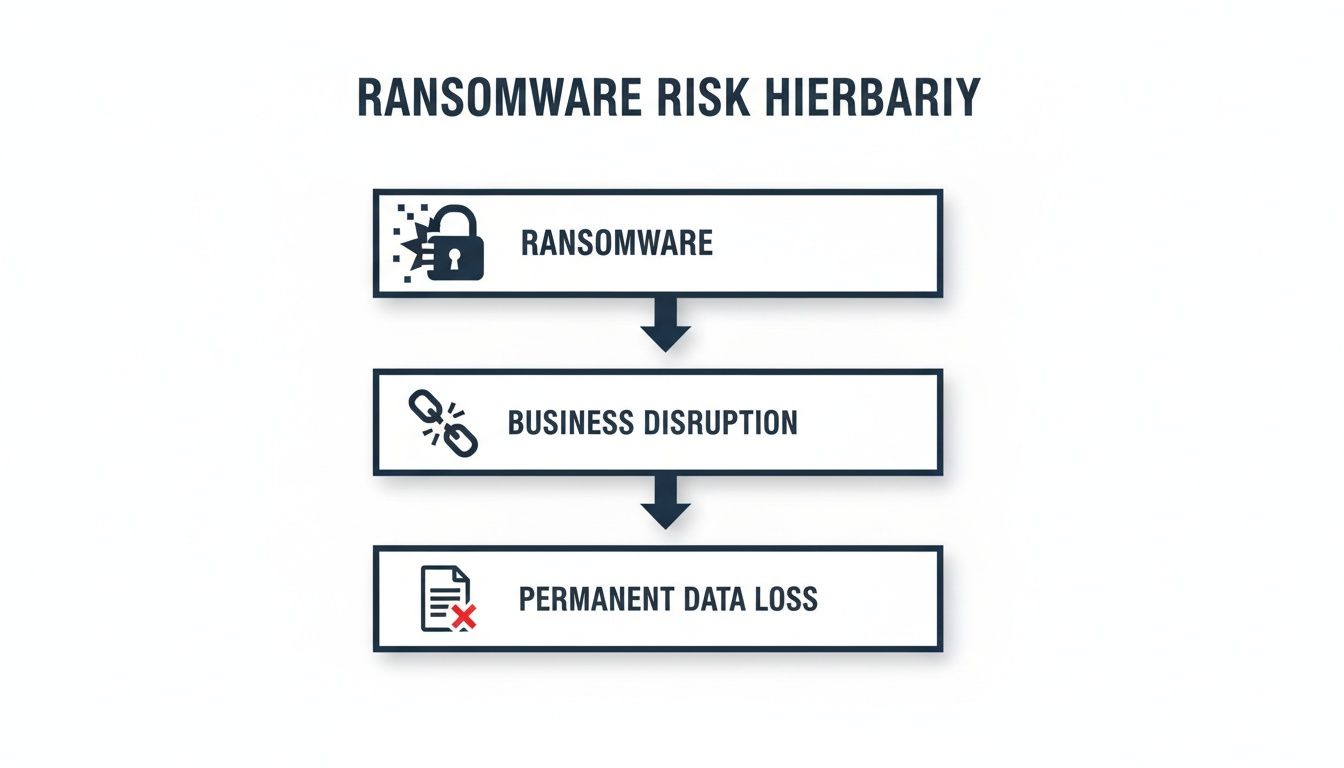
As you can see, a ransomware attack is never just about locked files. It spirals directly into business disruption and, too often, irreversible data loss that hits both your operations and your reputation.
A vulnerability assessment is like hiring a professional inspector to check every door, window, and crack in your building’s foundation before a burglar gets the chance. Security specialists use advanced tools to methodically scan your entire IT environment, hunting for known weaknesses that cybercriminals love to exploit.
This isn't a one-time checkup. New vulnerabilities are discovered in common software and hardware almost daily. Performing these assessments regularly ensures you find and patch these security holes proactively—effectively locking the digital doors that attackers are constantly trying to open.
Your network isn’t just in your office anymore. Every laptop, server, and mobile phone that connects to your business data is an endpoint, and each one is a potential doorway for an attack. Endpoint protection goes far beyond old-school antivirus software, providing advanced threat defence for all these devices, no matter where they are.
This kind of service deploys sophisticated tools that can:
By locking down every endpoint, you create a powerful defensive perimeter that protects your data, whether your team is in the Edmonton office or working from a coffee shop.
Even with the best defences, you must plan for a worst-case scenario. That's exactly what network segmentation does. Imagine your business is a ship; segmentation is like dividing the hull into multiple watertight compartments. If one compartment is breached, the flood is contained, and the rest of the ship stays afloat.
In the same way, network segmentation divides your IT infrastructure into smaller, isolated sub-networks. This ensures that if a cyberattack compromises one part of your network—like the guest Wi-Fi—it cannot spread to critical areas, like your financial records or client databases.
By limiting an attacker's ability to move freely within your systems, segmentation dramatically reduces the potential damage of a breach. It’s a fundamental principle of modern security architecture that contains threats and protects your most valuable assets.
Finally, no security strategy is complete without a solid backup and disaster recovery (BDR) plan. This is your ultimate safety net. If a catastrophe hits—a ransomware attack, a server meltdown, or even a natural disaster—a BDR plan ensures you can get your operations back online quickly and with minimal data loss.
This is about more than just backing up files. It's about having a clear, tested process for recovering your entire IT environment, from servers to applications. With a reliable BDR solution in place, you can have peace of mind knowing your business can bounce back from almost anything. You can dive deeper into what makes these solutions so robust by exploring the essentials of security managed services.
For any business in a regulated field like healthcare, finance, or law, compliance isn't just a box to check off—it’s the foundation of client trust and business integrity. Navigating regulations like Alberta's Health Information Act (HIA) or the federal Personal Information Protection and Electronic Documents Act (PIPEDA) can feel like you’re lost in a legal maze without a map.
These rules aren’t just gentle suggestions. They are strict, legally binding frameworks built to protect sensitive personal and health information. If your Edmonton business handles this kind of data, getting compliance right isn't optional; it's a non-negotiable part of your operations.
At their core, these regulations are about one thing: accountability. They require you to implement specific, concrete security controls to protect data from being accessed, used, or shared without authorization. Think of them as a detailed blueprint for building a secure digital vault for your clients' most private information.
For example, the HIA outlines exactly how healthcare providers in Alberta must handle patient records, from creation to destruction. This covers everything from mandatory data encryption to performing regular risk assessments. Failing here can lead to serious penalties, including massive fines and reputational damage that can take years to repair.
Compliance is a competitive advantage that signals reliability and professionalism to your clients. It demonstrates a concrete commitment to protecting their information, which is a powerful way to build and maintain trust in a crowded market.
Achieving and maintaining compliance isn’t a one-time project. It demands a systematic approach that weaves strong security measures directly into your daily operations.
Ignoring your compliance duties is a high-stakes gamble you cannot afford to take. The consequences go far beyond a simple slap on the wrist. A breach that exposes sensitive client information can trigger mandatory reporting, kicking off official investigations and leading to potentially business-crippling fines.
Beyond the fines, the operational chaos after a compliance failure can be overwhelming, often involving expensive forensic audits and complete system overhauls. Most importantly, the loss of client trust can be permanent, hitting your bottom line for years to come.
The risks are only getting bigger. Cybercriminals are increasingly targeting local businesses. In 2023, Alberta saw a shocking 12,124 cybercrimes reported to police, a sharp 24% jump from the previous year. This surge puts the spotlight on the escalating network security Edmonton challenges, with attackers actively looking for weaknesses in sectors like healthcare to access valuable data. You can find more details on regional cybercrime trends from CyberAlberta.
This is exactly where having a dedicated security partner becomes so critical. Instead of leaving you to decipher dense legal texts on your own, a managed security provider translates those requirements into a clear, actionable security plan. They work with you to implement the necessary technical and administrative controls, making sure you meet every single obligation.
A partner can provide:
By teaming up with an expert, you not only protect critical information but also free up your team to concentrate on what they do best—running your business. For those specifically navigating healthcare rules, understanding how to conduct a Privacy Impact Assessment in Alberta is a vital step, and a knowledgeable partner can guide you through that entire process.
Picking a partner for your network security in Edmonton is one of the most critical decisions you will make for your business. This isn't about hiring a vendor to install software; it’s about finding a strategic ally who truly understands your operations and is committed to your long-term resilience. So, how do you tell a real partner from just another service provider?
The right choice boils down to asking tough questions and looking for a few non-negotiable qualities. With a solid evaluation framework, you can cut through the sales pitches and find a provider who delivers real-world protection that fits your business here in Alberta.

When your systems go down, every minute feels like an hour. Having access to a 100% Canadian-based helpdesk is a massive differentiator. It means you get faster responses from technicians who are in your time zone and understand the local business climate.
Even more importantly, it's about data sovereignty. Keeping your sensitive business and client information right here in Canada ensures it’s protected under our privacy laws, like PIPEDA. This isn't just a nice-to-have—it's a foundational security and compliance must-have that keeps your data from falling under foreign laws and jurisdictions.
Generic, one-size-fits-all security solutions are a recipe for disaster. They almost always miss the unique challenges of specific industries. A provider with deep experience in your sector will already know the nuances of your operations, the value of your data, and the specific compliance hoops you must jump through.
When you're vetting a potential partner, don't be shy. Ask direct questions about their experience with businesses just like yours:
A partner who can answer these questions with confidence and back them up with real case studies is far more likely to build a security strategy that actually works.
A truly proactive security partner doesn't just react to alerts. They invest time in understanding your business goals and processes, then build a security framework that enables your growth while protecting you from threats. Their success should be measured by your uninterrupted operations, not just by how quickly they close a ticket.
The difference between a basic vendor and a strategic partner often comes down to their core philosophy. A reactive provider waits for something to break, then swoops in to fix it. A proactive partner, on the other hand, works tirelessly to stop issues from ever happening.
This proactive mindset is the cornerstone of modern network security in Edmonton. It involves continuous monitoring, regular vulnerability scans, and ongoing strategic advice to adapt your defences as new threats emerge. When choosing a provider, you are not just buying a service; you are investing in a partnership. To get a better sense of what this looks like, you can learn more about the benefits of a managed service provider (MSP) in Edmonton.
To figure out where they stand, ask how they handle threat intelligence, employee security training, and strategic IT planning. A genuinely proactive partner will have clear, structured programs for all three, showing a real commitment to your long-term security. Their goal should be to make your business so resilient that you rarely need to call them for an emergency.
To help you organize your thoughts and compare providers, we've put together a simple checklist. Use this to guide your conversations and make sure you are covering all the critical bases.
This checklist isn't exhaustive, but it provides a strong foundation for a meaningful evaluation. The right partner will welcome these questions and have clear, confident answers that align with your business goals. They will see it not as an interrogation, but as the start of a transparent, long-term partnership.
The cybersecurity world moves at a breakneck pace. A defensive strategy that works perfectly today could be a wide-open door for attackers tomorrow. As we look ahead at network security in Edmonton, it’s clear that the old playbook won’t cut it. The goal isn’t to predict the future with 100% accuracy but to build the resilience to handle whatever comes next.
Staying ahead means understanding the next wave of attacks. We are moving beyond familiar threats into an era where cybercriminals have more sophisticated tools than ever.
The threats looming on the horizon are smarter and sneakier than anything we've dealt with before. For Edmonton businesses, this means preparing for a new class of risks that target not just your data, but the very core of your operations.
Here’s a look at what’s coming:
Projections for 2026 paint a sobering picture for our region. Experts are bracing for 'very high' volumes of malicious activity, building on the 38 ransomware cases seen in 2024—a sharp jump from 15 in 2023. Beyond ransomware, the forecast for Alberta’s IT ecosystem points to a surge in AI-phishing, supply-chain attacks, and business interruptions designed to cause maximum chaos.
An adaptive security posture is your business's best defence against an uncertain future. It’s about creating a security framework that can evolve, learn, and respond to new threats as they appear, ensuring your business remains protected and resilient.
Getting ready for these challenges demands a real commitment to proactive, continuous improvement. It’s about moving past basic defences and fostering a security-first culture that runs through every part of your organization. Beyond your own efforts, getting involved in broader initiatives like the national Cyber Security Cooperation Program can give your business a serious boost in resilience.
Securing your company’s future starts with the foundational steps we’ve already discussed: understanding local risks, implementing essential managed security services, and choosing a local partner who truly understands the Edmonton landscape. This combination creates a powerful defensive foundation, ready to weather whatever storms are on the horizon.
When you're running a business, navigating the world of network security can feel complex. To cut through the noise, here are some straightforward answers to the questions we hear most often from Edmonton business leaders.
If we are talking about the single most damaging threat, it’s ransomware. We see it time and again, especially in Edmonton’s manufacturing, legal, and healthcare sectors. It has the power to bring your entire operation to a screeching halt, making it a massive financial risk.
But how does ransomware get in? The most common method is through a phishing attack. All it takes is one convincing but malicious email to trick an employee, and suddenly, an intruder has the keys to your kingdom.
That’s a fair question, and the honest answer is: it depends. The cost for professional network security in Edmonton isn't one-size-fits-all. It comes down to a few key factors:
Try to think of it less as a cost and more as an investment. The money spent on a proactive security plan is a fraction of what it costs to clean up after a major breach—which can easily run into tens of thousands of dollars from downtime, fines, and a damaged reputation.
Most managed security providers work on a fixed monthly fee. This gives you predictable budgeting with no surprise bills and almost always delivers a better return on investment than trying to hire, train, and equip an in-house security expert.
Yes, absolutely. In fact, you could argue that small businesses cannot afford not to have it. SMBs are often seen as easy targets and have the most to lose when an attack hits.
Professional managed security services are built to be scalable. They give you access to the kind of top-tier protection that large corporations use, but at a price point that makes sense for small and mid-sized businesses. You get a whole team of experts and advanced security tools for less than the salary of one full-time IT security specialist. It’s simply the most cost-effective way to get the job done right.
As a general rule, you should have a comprehensive security assessment done at least once a year.
However, you should plan for more frequent checks if your business goes through significant changes. This could be anything from rapid growth and hiring, adopting new software, or making a major shift to remote work. Regular assessments ensure your defences evolve alongside your business and the ever-changing threat landscape.
Ready to build a security strategy that protects your business today and prepares it for tomorrow? The team at CloudOrbis Inc. specializes in creating robust, compliant, and cost-effective security solutions for Edmonton businesses. Secure your free consultation today!

February 13, 2026
Azure Migration Edmonton: An Expert Guide to a Seamless Cloud TransitionAzure migration Edmonton: Plan, secure, and optimize your cloud move with practical steps, cost control, and security best practices.
Read Full Post
February 12, 2026
SharePoint Migration in Edmonton: A Guide to a Seamless Cloud MoveDiscover SharePoint migration Edmonton best practices: plan, execute, and optimize your cloud transition for faster ROI and minimal disruption.
Read Full Post
February 11, 2026
A Business Leader's Guide to Backup and Disaster Recovery in EdmontonProtect data and minimize downtime with proven backup and disaster recovery Edmonton strategies for a resilient business.
Read Full Post