
February 3, 2026
Proactive IT Maintenance Calgary: Prevent Downtime and Secure Your BusinessUnlock uptime with proactive it maintenance calgary, delivering secure IT systems and practical strategies for Calgary businesses.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
February 4, 2026

Fighting back against ransomware in Edmonton requires a proactive, multi-layered strategy. It's about moving beyond basic antivirus software. For local businesses like yours, this means blending advanced threat detection, rock-solid backup and recovery systems, and ongoing employee training to stand a chance against today's sophisticated cyber threats.

Ransomware isn't a distant headline anymore; it's a direct and growing threat right here in Edmonton. Cybercriminals are deliberately targeting the industries that are the lifeblood of our city — healthcare clinics with sensitive patient records, manufacturing plants, and legal firms holding confidential client files.
These are not random attacks. These sectors are prime targets because their daily operations are critical. Any amount of downtime translates directly into massive financial hits and a serious blow to their reputation.
The game has changed. This isn't just about locking up your files. Modern cybercriminals use multi-extortion tactics, creating a two-front war for business owners. They don't just encrypt your data—they steal a copy first and then threaten to leak it publicly.
This approach doubles the pressure. Suddenly, you're not just dealing with getting your business back online. You're also facing the nightmare of a public data breach, complete with potential regulatory fines and a total loss of your clients' trust.
It’s a dangerous myth that cybercriminals only hunt for large corporations. The truth is that small and medium-sized organizations in Edmonton are often seen as easier, more attractive targets precisely because they usually have fewer cybersecurity resources. Attackers know this, and they exploit it mercilessly.
Canada has seen a significant jump in these kinds of incidents. The Canadian Centre for Cyber Security has reported a 26% average year-over-year increase in ransomware events. That's not a blip; it's a trend, and it's expected to continue.
With Canada experiencing 30 significant cyber incidents in the last two years—making up 6.7% of the global total—the risk for businesses in our community is impossible to ignore. The rise of Ransomware-as-a-Service (RaaS) has made it shockingly easy for even unskilled criminals to launch devastating attacks. You can dive deeper into the ransomware threat outlook from the Government of Canada to see just how serious the situation is.
The fallout from an attack goes far beyond the ransom payment. You must consider the full scope of the damage:
Consider this guide your playbook for building a truly resilient defence. It's designed to give Edmonton's business and IT leaders the clear, actionable steps needed to protect your operations, data, and reputation. By treating ransomware as the critical business risk it is, you can shift from a position of vulnerability to one of strength and preparedness.
When it comes to ransomware, a proactive defence is your only winning move. An attack already in progress means you're on the back foot, trying to salvage what you can. An effective protection strategy for any Edmonton business is built on stopping threats before they gain a foothold.
It’s all about closing the digital doors and windows that cybercriminals are constantly rattling. Waiting for a security alert is too late; the goal is to neutralize threats so early that you never even knew they were there. This isn't just about damage control—it's about building a fortress that attackers cannot breach in the first place.
For years, we all relied on traditional antivirus software. It was simple enough: it checked files against a list of known viruses. The problem is, modern ransomware is designed to be a complete stranger, easily walking past those outdated checks.
This is why next-generation security tools are no longer optional. Think of them less like a bouncer with a list and more like a seasoned security team that watches for suspicious behaviour, not just known faces.
Imagine an Edmonton-based manufacturing firm. An attack starts on a compromised laptop on the shop floor. EDR can stop it right there, before it ever reaches the central server running the production schedules. Without it, the initial breach could remain a mystery, leaving them vulnerable to the same attack next week.
To give you a clearer picture, here’s a breakdown of the core technologies that form a modern defensive line.
These layers work together. Relying on just one is like locking your front door but leaving all the windows wide open.
For all the sophisticated hacking tools out there, the most common way ransomware gets in is through a simple phishing email. Attackers have become masters of social engineering, crafting messages that look identical to real communications from suppliers, clients, or even the CEO.
Basic email filters no longer suffice. You need advanced email security that does more than check a sender's address. Modern systems inspect links to see where they truly lead, analyze attachments in a safe "sandbox" environment, and use AI to spot the subtle grammar mistakes or phrasing that signals an impersonation attempt.
A convincing fake invoice sent to your accounts payable team is all it takes to cripple your entire operation. One click can unleash ransomware that tears through your network in minutes, locking up financial records, client data—everything.
The spike in ransomware incidents across Canada is alarming, with confirmed cases nearly tripling in just one year. Attackers are all-in on double extortion tactics, where they not only encrypt your data but also steal it and threaten to leak it online. This puts Edmonton's healthcare providers and professional service firms in a terrible position, where a data breach is just as damaging as the operational shutdown. You can learn more about the trends in ransomware from recent industry reports.
Every piece of software on your network—from the server's operating system to the web browser on a laptop—can have security weaknesses, or "vulnerabilities." Cybercriminals actively hunt for these unpatched flaws because they are an easy, unlocked door into your business.
A solid vulnerability management program is a non-negotiable part of modern cybersecurity. This isn’t a one-and-done task; it’s a continuous cycle.
Without this systematic process, your network is almost certainly full of security holes. A single unpatched server exposed to the internet is one of the most common ways major breaches begin. For businesses that want this handled expertly without dedicating internal staff, exploring how security managed services can automate this entire process is a smart move. Proactive security isn't just about the tools you buy; it's about the interlocking processes you build to create a formidable barrier.

You can have the best security technology money can buy, but it all means very little if a single, unintentional click from an employee can bring it all crashing down. Cybercriminals know this is their easiest way in, which is why a staggering 90% of data breaches involve some form of human error.
This is precisely why the most effective ransomware protection Edmonton businesses can build starts with their people. The goal isn't to point fingers; it's to empower your team, transforming them from a potential weak link into a vigilant "human firewall." A well-trained team becomes your most intelligent line of defence, often spotting sophisticated threats that automated filters might miss.
Simply telling employees to "be careful online" is no longer sufficient. Today’s threats are far too clever for that. An effective training program needs to be ongoing, engaging, and directly tied to the real-world dangers your team navigates every day.
A massive part of this is teaching them how to spot and avoid common entry points for malware, especially advanced Phishing and Smishing Scams. These attacks are, without a doubt, the number one way ransomware gets a foothold inside a business network.
Here are the key areas your training must cover:
When you foster a culture where employees feel comfortable raising their hand and saying, "This email looks strange," you create an environment of shared responsibility. That proactive mindset is priceless and can stop an attack dead in its tracks.
Theory is one thing; practice is another. One of the best ways to make security training stick is through controlled phishing simulations. We send harmless, simulated phishing emails to your team to see how they react in a real-world scenario. The goal is never to trick or shame employees but to provide a powerful, practical learning moment.
When someone clicks a simulated phishing link, they are not reprimanded. Instead, they're immediately directed to a bite-sized training module that shows them exactly what red flags they missed. This "just-in-time" learning is incredibly effective because the lesson is directly linked to their action.
This approach delivers significant benefits:
To learn more about the technical side of locking down your inbox, our guide on email security best practices offers a deeper look at the tools and tactics involved. Building a strong human firewall is a continuous cycle of training, testing, and reinforcement—an effort that pays massive dividends in protecting your Edmonton business from the devastating impact of ransomware.
Even with the best defences in the world, a sophisticated ransomware attack can sometimes find a way through. When that happens, your backup and recovery strategy becomes the last line of defence—your ultimate safety net that makes paying the ransom a non-issue.
A solid Backup and Disaster Recovery (BDR) plan isn't just about having copies of your files. It’s about having the right kind of copies, stored in the right places, and being able to restore them at a moment's notice. For any Edmonton business that’s serious about staying in business, this isn't just an IT task; it's a core operational pillar.
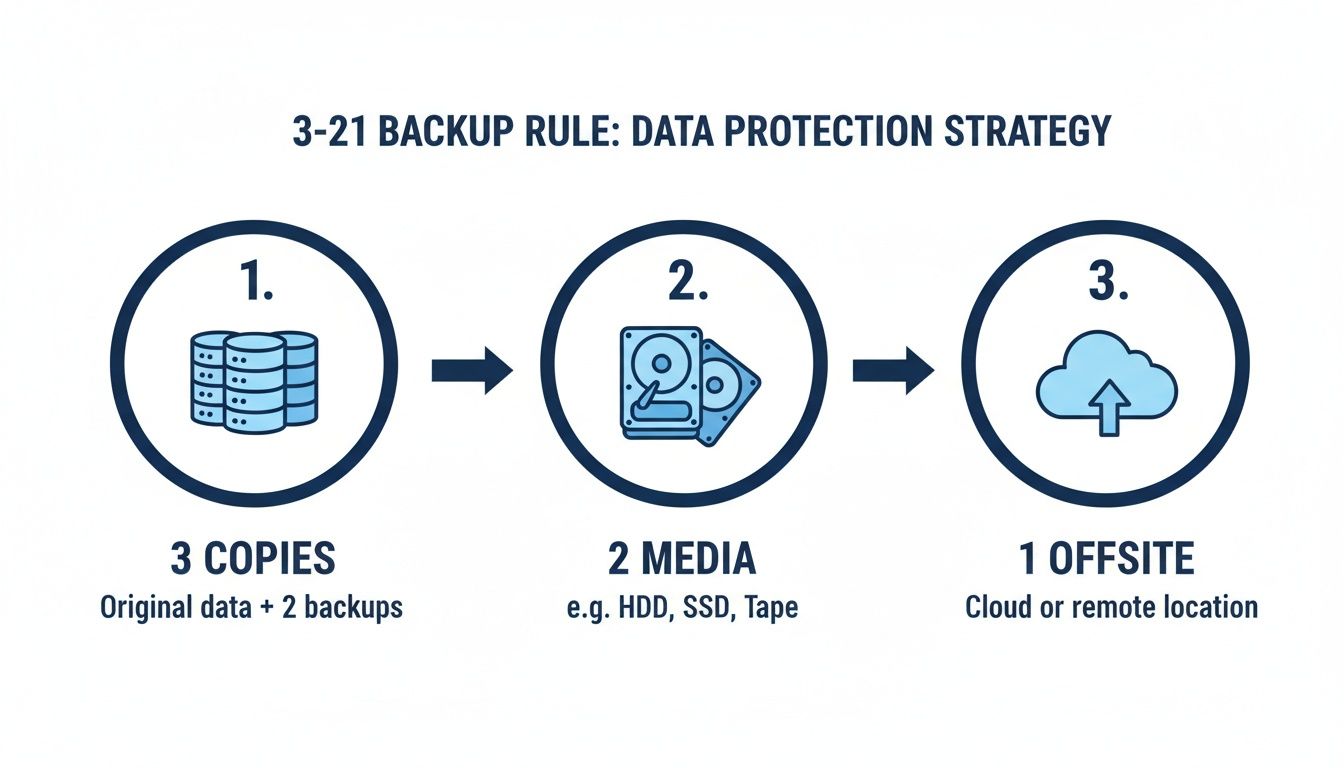
The foundation of any modern, effective backup plan is the 3-2-1 rule. It’s a simple concept that has stood the test of time because it directly counters the tactics ransomware attackers use to corner you.
Here’s the breakdown:
Three Copies of Your Data: This means your original, primary data plus at least two backups. This redundancy immediately cuts down the risk of a single point of failure. If one backup is corrupted or unavailable, you have another waiting.
Two Different Media Types: Do not put all your eggs in one basket. Keep one backup on an internal network drive, for instance, and the other on a completely separate medium like an external hard drive or a different cloud service. This protects you if a specific type of device fails.
One Copy Offsite: This is the absolute game-changer for ransomware protection. At least one of your backups must be physically and digitally isolated from your primary office and network. This could be a secure cloud backup service or a physical drive stored at another location.
If ransomware encrypts your entire office network, that offsite copy remains completely untouched. It’s your clean slate, ready to get you back up and running.
While the 3-2-1 rule is a fantastic starting point, today’s cybercriminals are crafty. They know businesses have backups, so one of the first things they do after gaining access is hunt down and encrypt or delete them.
This is why a modern BDR strategy needs more than just copies; it needs layers designed to outsmart attackers.
An attacker’s main goal is to take away your ability to recover. If they can lock up your primary data and your backups, they know you'll have no choice but to consider paying. Immutable and air-gapped backups are designed to make that impossible.
Think of an immutable backup as a "write-once, read-many" snapshot of your data. Once that backup is created, it cannot be changed, overwritten, or deleted for a set period—not even by an administrator with the highest-level credentials. It creates a time-locked vault that ransomware cannot crack.
An air-gapped backup is one that is physically disconnected from your live network. In the past, this meant using tape drives that were physically removed and stored offline. Today, it can also refer to cloud storage that is logically isolated from the main network, requiring completely separate authentication to access. That physical or logical "air gap" means there's no live connection for ransomware to travel across.
To help you decide what's right for your business, it’s helpful to see how these different approaches stack up against a ransomware attack.
Comparing backup types shows a clear hierarchy of protection. A basic network backup is a sitting duck, while modern methods create nearly insurmountable barriers for attackers.
Ultimately, combining immutable and air-gapped strategies provides the strongest defence, ensuring that no matter what an attacker does on your live network, your recovery point is safe.
A backup you have not tested is not a plan, it's a prayer. It’s shocking how many businesses only discover their backups are corrupted, incomplete, or were never configured correctly in the first place after disaster strikes. By then, it's far too late.
Regular, automated testing is non-negotiable. This goes beyond just receiving a notification that a "backup job completed." Real testing means performing a trial restoration of files, applications, or even entire servers in an isolated environment to prove that everything works as it should.
Set a clear testing schedule, document the results, and make it part of your routine. This ensures your ransomware protection in Edmonton is built on proven reliability, not wishful thinking. A well-designed and thoroughly tested backup system gives you the confidence to restore your operations quickly, turning a potential catastrophe into a manageable inconvenience.
For a deeper dive into these concepts, check out our complete data backup and recovery guide to build an even more resilient strategy.
When a ransomware attack hits, the first few hours are a chaotic blur of panic and confusion. A clear, well-rehearsed Incident Response (IR) playbook is what transforms that chaos into a controlled, effective response. Think of it as your step-by-step guide to containing the damage, eradicating the threat, and getting your business back online as quickly—and safely—as possible.
This isn’t a document you can create in the middle of a crisis. An IR playbook is a proactive tool every Edmonton business needs before an attack ever happens. It clearly lays out roles, responsibilities, and the exact sequence of actions to take, ensuring no critical steps are missed when the pressure is on.
A solid incident response plan is built around three core phases. Each one has a distinct goal, designed to methodically move you from crisis to recovery. Think of it like this: first, stop the bleeding; then, remove the infection; and finally, heal the wound.
A common mistake is rushing to recover before the threat is fully eradicated. If you restore your clean data onto a network that's still compromised, you are just setting the stage for a second, and often more devastating, ransomware attack.
In the heat of an incident, it is easy to forget crucial steps. Your playbook needs a clear, concise checklist that your team can follow without having to think twice. This isn't just for IT staff; it's a coordinated business response.
For businesses looking to formalize their defence, using an effective IT disaster recovery plan template can provide a solid foundation for building out these crucial checklists and procedures.
Managing a ransomware incident goes far beyond the server room. Your playbook must also account for the business and legal fallout, especially when it comes to Alberta's privacy laws.
A critical part of your plan is knowing your obligations under the Personal Information Protection Act (PIPA). If any client or employee data was accessed, you have a legal duty to notify affected individuals and the Office of the Information and Privacy Commissioner of Alberta. Failing to do so can result in significant fines.
This is where having a robust backup strategy, like the classic 3-2-1 rule, becomes your ultimate safety net.
This simple concept—having an offsite, isolated copy of your data—is the fail-safe that makes recovery possible even if your entire office network is compromised. It’s exactly why a well-structured plan, like the one we detail in our IT disaster recovery plan template, is so vital. It ensures your ransomware protection in Edmonton is built on a foundation of preparedness, not just prevention.
Navigating the complexities of ransomware protection on your own is a monumental task. For most small and medium-sized businesses without a dedicated in-house cybersecurity team, it's completely overwhelming. This is where the right partnership isn't just helpful—it's a strategic advantage.
Think of it less as outsourcing a problem and more as gaining a dedicated ally whose sole focus is keeping your business resilient.
For any business in Edmonton, a local security partner brings an immediate and invaluable level of context. They are not just familiar with the threats targeting our region; they live and breathe Alberta's regulatory landscape, like PIPA. This local knowledge is crucial for building a security strategy that's not just effective, but fully compliant.
An expert partner provides the human intelligence that technology simply cannot replicate. They deliver 24/7 threat monitoring, which means a skilled team has eyes on your network long after your team has gone home for the day. This constant vigilance is critical, as attackers love to strike outside of business hours to maximize damage before anyone notices.
A partnership also brings a proven track record in incident response. If the worst happens, you need a team that has been through the fire before—one that can execute a response plan with precision and calm. That experience dramatically cuts down recovery time and minimizes both financial and reputational damage.
A true security partner doesn’t just sell you software. They integrate into your business, learn your operations, and build a security posture that aligns with your specific risks and goals. This relationship transforms cybersecurity from an expense into a business enabler.
Choosing the right partner means looking for a team that can implement every strategy we've discussed in this guide. From endpoint protection and vulnerability management to designing and testing a bulletproof backup strategy, they should handle the complexities so you can get back to running your business.
When you’re evaluating providers for ransomware protection in Edmonton, you need to prioritize those who offer a complete, proactive service. Here are the non-negotiables:
This proactive stance is what separates a basic IT provider from a genuine cybersecurity partner. Many businesses discover that partnering with an Edmonton IT company that specializes in security is the most effective and cost-efficient path forward.
Ultimately, a partnership pulls all the pieces of this playbook together into a single, cohesive, and managed strategy. It gives you the technology, the expertise, and—most importantly—the peace of mind that comes from knowing your business is protected by a team of dedicated professionals.
Ready to assess your current security posture and build a resilient defence against ransomware? CloudOrbis provides the expert guidance and managed security services Edmonton businesses trust. Contact us today for a free consultation.

February 3, 2026
Proactive IT Maintenance Calgary: Prevent Downtime and Secure Your BusinessUnlock uptime with proactive it maintenance calgary, delivering secure IT systems and practical strategies for Calgary businesses.
Read Full Post
February 2, 2026
A Guide to IT Compliance for the Alberta Oil & Gas IndustryMaster it compliance for alberta oil & gas industry with a practical, click-ready guide on AER/TIER, cybersecurity controls, and audit readiness.
Read Full Post
February 1, 2026
A Guide to IT Compliance Needs for Alberta Private Career CollegesExplore it compliance needs alberta private career college with practical guidance on PIPA, the PVT Act, and core security controls to protect student data.
Read Full Post