
January 31, 2026
Finding the Right Edmonton IT Company for Your BusinessDiscover how to choose the right Edmonton IT company. Our guide covers strategic IT services, cybersecurity, and cloud solutions to fuel your business growth.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
February 1, 2026

For private career colleges in Alberta, the regulatory landscape has changed. Your IT compliance is no longer just a back-office task—it's now directly tied to your provincial licence and your students' success.
Solid IT systems are the only way to securely collect, manage, and report the auditable data on graduation and employment rates that Alberta's regulators now demand. If you can't prove these outcomes through reliable tech, you’re putting your college’s reputation and its very licence to operate on the line.

What was once a manageable set of operational guidelines has quickly become a high-stakes environment where your institution's future depends on data. The government has tightened its oversight, now asking for clear, verifiable proof of student success before it will even consider renewing a college's licence.
This significant shift means IT compliance is no longer a technical chore handled solely by the IT department. It’s now a core business function. It’s about more than just protecting student data; it's about using your technology to prove your college delivers real value.
The biggest hurdle you're facing is proving your worth through numbers. Alberta's regulators are now laser-focused on key performance metrics—specifically graduation rates and post-graduation employment rates. Your IT systems are the tools you must use to collect, secure, and present this critical information.
Think of your IT infrastructure as the bedrock of your compliance strategy. Without a solid, secure, and auditable system, you cannot produce the reliable data needed to satisfy government mandates. This reality connects every piece of your technology, from your Student Information System (SIS) to your network security, directly to your ability to keep your doors open.
The new regulatory framework isn't just asking for reports; it's demanding a culture of accountability. Your IT systems must be capable of telling a clear, data-backed story of student success from enrolment to employment.
Viewing compliance as just another legal box to tick is a significant mistake. In this new era, it’s a fundamental part of your commitment to students and the long-term health of your institution. A strong IT compliance program does more than just keep regulators happy. It also:
The stakes have never been higher. Public compliance orders are a real threat for institutions that fall short, putting your college’s future at risk. Navigating these IT compliance needs as an Alberta private career college requires a smart, strategic approach where your technology is perfectly aligned with both regulatory demands and your own goals. This guide will walk you through the essential steps to build that resilient framework.
For any private career college in Alberta, your IT compliance boils down to two key pieces of legislation. These are not suggestions; they are the rulebooks that dictate how you handle every piece of student information, from the moment they apply to long after they graduate. Understanding how they interact is the first step toward building an IT operation that’s both effective and audit-proof.
The two pillars supporting your compliance structure are Alberta’s Private Vocational Training (PVT) Act and the Personal Information Protection Act (PIPA). While one tells you what to do and the other tells you how to do it securely, they are deeply interconnected. A misstep in one area almost always means you’re out of sync with the other.
Think of the PVT Act as the core operating manual for your college. It covers everything from program licensing to student contracts, but it truly impacts your IT with record-keeping. The Act is clear: you must meticulously track, secure, and report very specific student data for their entire journey with your institution.
This isn't just about grades. Your systems need to be set up to produce verifiable, auditable records for:
The government's recent push for accountability has put a huge spotlight on that last point. Your IT systems are no longer just for administration; they are now the primary tool you'll use to prove your college delivers on its promises.
In fact, the regulatory framework now has specific reporting metrics that hinge entirely on your data management. Colleges must report both graduation rates and employment rates, with a hard minimum of 70% for both metrics in back-to-back reporting periods. To achieve this, you need rock-solid systems capable of tracking graduates and confirming their employment is related to the training they received. You can find the full compliance standards on the Government of Alberta's website.
If the PVT Act tells you what data to collect, PIPA is all about how you protect it. PIPA governs how every private organization in Alberta collects, uses, and secures personal information. For a college, that’s a mountain of sensitive data—student contact info, financial aid details, academic transcripts, and even health records provided for accommodations.
At its core, PIPA demands you have "reasonable security arrangements" to shield this information from unauthorized access. The word "reasonable" isn't a suggestion—it's a legal standard that means you have an active duty to defend the data you hold.
A simple request for a student transcript becomes a PIPA compliance test. Your IT processes must verify the student's identity and deliver the information securely without accidentally exposing anyone else's data.
This obligation touches every part of your IT infrastructure. It must be built to stop breaches, whether they come from a sophisticated cyberattack or a simple internal mistake. Getting this wrong can lead to massive fines and the kind of reputational damage that’s hard to recover from. To dive deeper into how these privacy rules work, check out our guide on conducting a Privacy Impact Assessment in Alberta.
Let's break down how these two acts work together.
Here’s a quick comparison to see how the PVT Act’s demands for data collection intersect with PIPA’s rules for data protection.
Ultimately, every piece of technology you bring into your college—from your Student Information System (SIS) to cloud storage—must be evaluated through the lens of both PIPA and the PVT Act. Your responsibility to protect student data is absolute, making strong IT security a foundational, non-negotiable part of your operation.
Let's move from the theory of regulations to the practical, hands-on work of building a digital fortress around your student data. This is where we implement the essential technical security controls—the actual, tangible safeguards that form the backbone of your IT compliance strategy.
Think of these as the non-negotiable tools that protect your college from data breaches, show auditors you're serious, and ultimately, build trust with your students. These aren't just isolated pieces of software; they're an interconnected security system. Each control has a specific job, from verifying who is logging in to ensuring you can get back online after a server failure. For an Alberta private career college, getting these technical details right is a direct reflection of your commitment to PIPA and the PVT Act.
This flow chart breaks down your basic regulatory duties, starting from when you first collect data, moving through the protection phase, and ending with reporting.
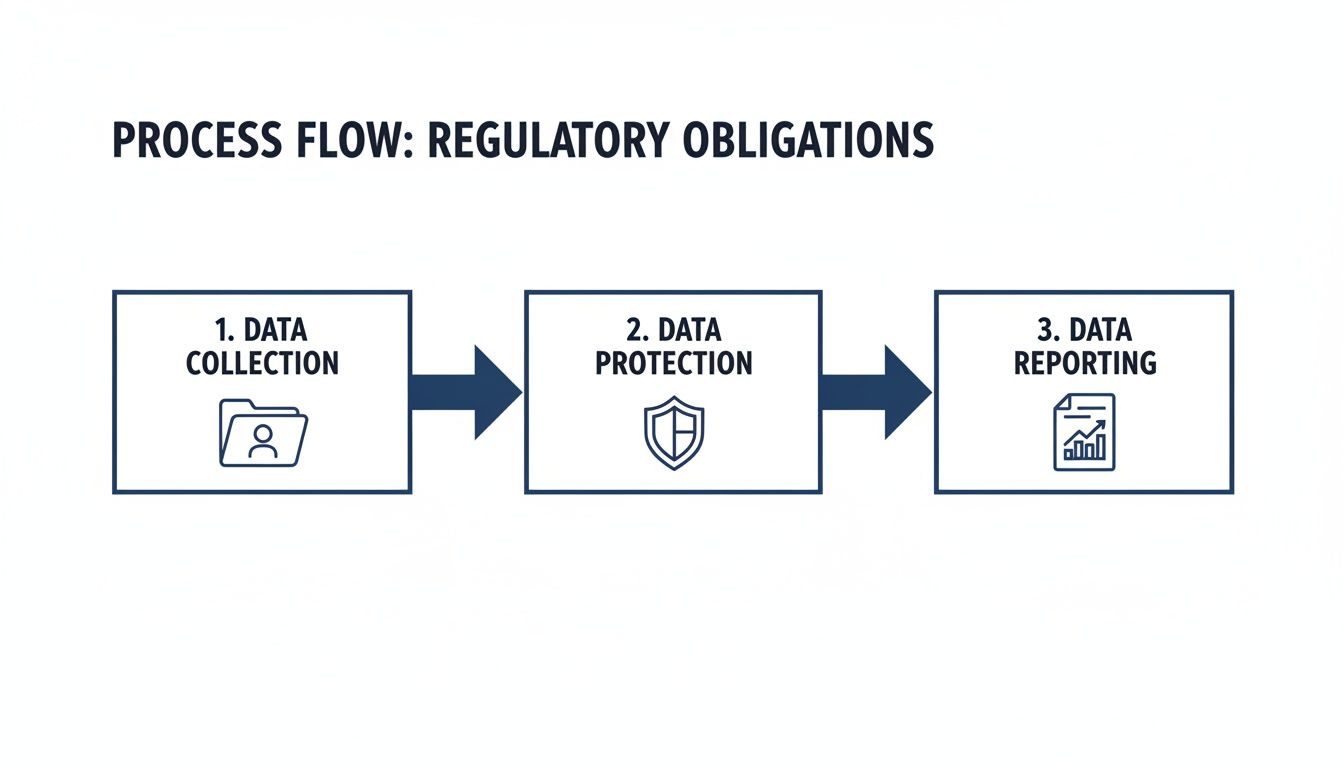
As you can see, your technical controls are the star of the show during the 'Data Protection' stage. This is where you actively safeguard all the sensitive information you're required to handle.
The most fundamental rule of security is ensuring only the right people can get to the right information at the right time. This is the heart of access control, and it's your main defence against both external hackers and internal snooping. If an unauthorized user gains access to your Student Information System (SIS), the fallout can be devastating.
The best way to manage this is with the principle of least privilege. In simple terms, every staff member—from admissions to instructors—should only have access to the absolute minimum of data needed to do their job. An instructor needs to see their students' grades, but they have no business looking at financial aid records.
Putting strong access control in place involves a few key actions:
Even with the best locks on the doors, you have to plan for someone getting through. Data encryption is your last line of defence. It scrambles your data into unreadable code, making it useless to anyone who doesn’t have the unique key to unlock it.
PIPA's demand for "reasonable security arrangements" essentially makes encryption a must-have. You need to encrypt data in two key states:
Think of end-to-end encryption like sending a message in a locked box. Only the intended recipient has the key to open it. Even if someone intercepts the box, the contents remain confidential.
What would happen if your main server went down tomorrow due to hardware failure or a ransomware attack? Without a solid backup and disaster recovery plan, you could lose years of essential student records. That’s a direct violation of the PVT Act's rules on record-keeping.
A reliable backup strategy isn't optional. The industry gold standard is the 3-2-1 rule:
But just having backups isn't enough—you have to know they work. Running a disaster recovery drill at least once a year is crucial. It ensures you can restore your data and get your systems back online in a reasonable amount of time, keeping disruption to a minimum.
You can't stop a threat you can't see. Security logging and monitoring act as the digital surveillance cameras for your entire IT environment. The goal is to systematically record what’s happening on your network, servers, and applications, and then actively look through those logs for anything suspicious.
These logs give you an invaluable, time-stamped record of who did what, and when. If a security incident happens, this information is vital for figuring out how the breach occurred and what data was compromised. It’s also a cornerstone of any incident response plan, helping you provide the clear evidence needed to meet PIPA’s mandatory breach notification rules. An effective logging system lets you answer the tough questions during an investigation, turning chaos into a manageable, documented process.
Your technical controls are the engine of your security, but a strong IT governance and policy framework is the steering wheel. Technology alone cannot create a culture of security—that requires clear rules, defined responsibilities, and consistent training. True compliance is built on this foundation of strong policies, ensuring everyone from administrative staff to instructors knows their role in protecting sensitive data.
This framework is what turns complex regulatory demands into practical, everyday actions. It takes the idea of IT compliance needs for an Alberta private career college from a vague concept and makes it a tangible set of expectations for your team. Without it, even the best security software can be defeated by a single human error.
To build a resilient governance structure, you need to start with three essential policies. These aren't just documents for auditors; they are living guides that shape behaviour and reduce risk across your college. They establish a clear baseline for how technology and data should be handled, leaving no room for guesswork.
The three cornerstone policies you must develop are:
Think of your AUP as the rulebook for digital citizenship at your college. It should be written in straightforward language, not technical jargon, so every user can understand their responsibilities. It sets clear boundaries on activities, which protects the institution from liability and reinforces a security-first mindset.
For instance, a well-written AUP will explicitly prohibit sharing passwords, using college devices for illegal activities, or installing unauthorized software. By having every user sign this policy, you create a documented agreement that is crucial for enforcement and proves due diligence to regulators.
A strong Acceptable Use Policy does more than list what people can't do. It educates users on why these rules are in place, connecting their daily actions directly to the protection of student data and the college’s reputation.
Holding onto data forever isn't just a storage headache; it's a massive compliance risk. Your data retention policy is a schedule that governs the entire lifecycle of your information. It ensures you keep records for as long as legally required by the PVT Act—like permanent student transcripts—while also making sure you securely dispose of data that has served its purpose, as PIPA demands.
This proactive approach minimizes your data footprint, which in turn reduces the amount of sensitive information that could be exposed in a breach. Crafting this policy often requires a strategic approach to balance various regulations. For help developing a comprehensive plan, you might explore expert guidance on IT strategy and consulting.
Ultimately, your employees are your first and last line of defence. Mandatory security awareness training is arguably the single most effective investment you can make in your compliance program. It transforms your staff from potential weak links into a vigilant human firewall.
This is especially critical right now. Alberta's private career college sector has faced intense scrutiny, with the government issuing compliance orders against 15 institutions since June 2024. This enforcement wave underscores the need for robust systems and processes to prove you're doing your due diligence.
For institutions in Alberta, knowing how to navigate these regulations is key. Comprehensive training from a relevant source, such as a Cyber Security Governance Risk And Compliance Professional course, can provide the knowledge needed to build a truly compliant and secure environment.
Realistically, most colleges today run on a mix of powerful tools. You are likely using cloud platforms like Microsoft 365 for your day-to-day operations and relying on various software vendors for everything from admissions to your student information system. These tools are fantastic for efficiency, but they also introduce new complexities for compliance.
Every time you use a third-party service, you're entrusting them with sensitive student data. But here’s the crucial part: under PIPA, the accountability still stops with you. The responsibility for that data never leaves your office.
This "shared responsibility" means your compliance efforts can't stop at your own front door. If you aren't actively managing the risk that comes with your vendors, you're overlooking a direct threat to your operations. It’s a core part of the it compliance needs alberta private career college administrators must get right.
When you're evaluating cloud services, one of the first and most critical questions you need to ask is about data residency. This simply means the physical, real-world location where your data is stored. For colleges in Alberta, this is a major compliance issue, not just a technical detail. The spirit of PIPA is clear: keep personal information inside Canada to shield it from foreign laws.
If your student records are sitting on servers in the United States, they could potentially be accessed under laws like the U.S. PATRIOT Act. That’s a serious compliance gap.
Ensuring your cloud provider guarantees Canadian data sovereignty isn’t just a “nice-to-have”—it’s non-negotiable. All your data, including every single backup, must reside exclusively in Canadian data centres. This is how you protect it from foreign legal reach and stay aligned with provincial privacy expectations.
When you're evaluating a new Student Information System (SIS) or even renewing your Microsoft 365 plan, your first question should always be, "Can you guarantee—in writing—that our data will never leave Canada?"
You wouldn’t hire a new instructor without a thorough background check. You need to apply that same level of rigour to your technology vendors. Before you sign a contract, you must do your homework on their security and compliance practices. You’re essentially auditing your suppliers to make sure they’re worthy of your students' trust.
Your vetting process should include these checks:
Never assume a vendor is compliant just because they're a big name. You need to verify everything and get their promises in writing. Navigating the world of cloud options can be tricky; our overview of managed cloud computing can help you learn more about making the right choice.
Ultimately, managing your vendors is about staying in control. When you carefully choose partners who share your commitment to security and lock in clear expectations contractually, you can use powerful modern tools without compromising your compliance.
Having solid security controls and policies is a great start, but in today’s regulatory world, it’s not enough to be compliant—you have to be able to prove it. For an Alberta private career college, this means being ready for a government audit at any moment.
That readiness comes down to having meticulous, organized, and accessible documentation. It's about telling a clear story of your due diligence. A proactive approach can turn a potentially stressful audit into a simple verification exercise. Instead of scrambling to find documents and answer tough questions, you can confidently present a complete picture of your compliance program.
Think of your documentation as your proof. It's the tangible evidence that your policies are not just sitting in a binder but are actively implemented, monitored, and enforced daily.
Auditors from the Ministry of Advanced Education or the Office of the Information and Privacy Commissioner (OIPC) work on a simple principle: if it isn’t written down, it didn’t happen. Effective documentation creates a clear, auditable trail of all your compliance activities, from high-level policies right down to detailed system logs.
Here are the key documents you must maintain:
The best way to pass an official audit is to audit yourself first. Proactive internal audits and regular vulnerability assessments are the cornerstones of any mature compliance program. They let you find and fix gaps before a regulator does, saving you from potential fines and reputational damage.
An internal audit is like a dress rehearsal for a real inspection. You methodically review your controls, policies, and documentation against the requirements of the PVT Act and PIPA. The goal isn't to find fault; it's to find opportunities for improvement in a low-stakes environment.
A proactive internal audit isn't about finding fault; it's about finding opportunities for improvement. It’s a dress rehearsal that ensures you’re prepared for the main event.
Alongside these internal reviews, vulnerability assessments are crucial. These are technical scans that actively search your network, servers, and applications for known security weaknesses that an attacker could exploit. By identifying and patching these vulnerabilities regularly, you’re not just strengthening your technical defences—you’re demonstrating a real commitment to proactive risk management.
If you want a deeper look at what this involves, you can explore our guide on what to expect during computer security audits. This proactive cycle of testing, identifying, and fixing turns compliance from a dreaded event into a continuous, manageable process.
Navigating IT compliance brings up many questions for administrators and IT leaders. The rules can feel complex, and figuring out where to focus your resources is a challenge. Here, we tackle some of the most common concerns we hear from Alberta's private career colleges.
When you’re a smaller institution, the scope of compliance can feel overwhelming. Don't try to tackle everything at once.
The single most effective first step is a practical IT risk assessment. You can't protect what you don't fully understand. This process involves mapping out where your sensitive student and operational data resides, identifying your biggest weak spots, and creating a straightforward, prioritized action plan. This lets you strategically focus your limited time and budget where it will have the greatest impact, ensuring your efforts directly address the most pressing IT compliance needs Alberta private career college operators face.
There’s no one-size-fits-all answer here. The cost of IT compliance depends on your college's size, the complexity of your current IT setup, and what security measures you already have in place. A smaller institution might start with a foundational package covering a risk assessment and policy development, while a larger college may need ongoing vCIO services and advanced security monitoring.
The best way to look at compliance spending is as an investment, not just an expense. The cost of building a proactive compliance program is consistently less than the financial and reputational fallout from a data breach or a licensing issue.
While Alberta’s Personal Information Protection Act (PIPA) is the cornerstone of data privacy, it’s not the only rulebook. The Private Vocational Training (PVT) Act carries its own significant IT implications that you can't afford to ignore.
The PVT Act has specific requirements for:
A solid compliance strategy must address the requirements of both frameworks. Overlooking one can leave you exposed, even if you’re fully compliant with the other. True security comes from an approach that covers all your regulatory bases.
At CloudOrbis Inc., we provide expert guidance and managed IT services to help Alberta's private career colleges navigate the regulatory landscape with confidence. Let's talk about building a resilient, audit-ready IT compliance framework for your college.
Learn more at https://cloudorbis.com

January 31, 2026
Finding the Right Edmonton IT Company for Your BusinessDiscover how to choose the right Edmonton IT company. Our guide covers strategic IT services, cybersecurity, and cloud solutions to fuel your business growth.
Read Full Post
January 30, 2026
Your Strategic Growth Partner for IT Support for Small Business in TorontoDiscover the best IT support for small business Toronto. Learn how managed services, security, and strategic partnerships drive growth in a competitive market.
Read Full Post
January 29, 2026
A Guide to Privacy Impact Assessment in Alberta Under PIPA, FOIP, and HIAYour essential guide to privacy impact assessment Alberta. Understand when PIAs are required under PIPA, FOIP, and HIA with a clear, step-by-step process.
Read Full Post