
January 26, 2026
Canada's Top 7 Managed IT Services Companies for 2024Searching for managed IT services companies? Explore our 2026 roundup of Canada's top 7 providers for SMBs in Toronto, Calgary, and Edmonton.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
January 29, 2026

A Privacy Impact Assessment (PIA) in Alberta is a vital process for identifying, assessing, and mitigating privacy risks before launching a new project, technology, or system. More than just a best practice, it is a mandatory requirement under provincial laws like PIPA, HIA, and FOIP whenever an initiative involves handling personal information in a way that could significantly impact an individual's privacy.
Think of it as a proactive blueprint for data protection, not simply a compliance task performed after the fact.
If your organization operates in Alberta, managing personal information is a legal and ethical duty. Understanding the province's privacy laws is the first step toward building trust with your customers, protecting your reputation, and avoiding significant penalties. The Privacy Impact Assessment (PIA) is your most effective tool for addressing these obligations directly.
While it might be tempting to view a PIA as just another bureaucratic hurdle, it is better understood as a strategic business process. It compels your team to ask critical questions early in a new initiative’s lifecycle. By identifying potential privacy issues at the outset, you can integrate data protection into your projects from the ground up.
Alberta’s privacy landscape is built on three key statutes. Each one targets different types of organizations, but they all share the common goal of ensuring personal information is handled with respect and security.
Determining which act applies to your organization is the first step. A crucial part of meeting your privacy obligations is clearly defining and communicating your organization's internal rules for data handling. For a great example of how this is structured, review this guide on understanding your privacy policy for valuable context.
A well-executed PIA is more than a document; it's your organization's best defense against data breaches and reputational damage. It demonstrates due diligence and a commitment to protecting the individuals whose data you hold.
When you fully embrace the PIA process, you transform a legal requirement into a powerful tool for your IT and business strategy. It provides the confidence to adopt new technologies and processes, knowing you have a clear map to guide your data governance. For more on navigating these complex rules, take a look at our overview of compliance solutions. This forward-thinking approach is essential for any modern business in Alberta.
So, what exactly is a Privacy Impact Assessment (PIA)?
Think of it as a blueprint for privacy. Before an architect designs a building, they conduct a structural analysis to identify weak points. A PIA performs a similar function for your data. It is a formal process that allows you to analyze a new project or system and identify potential weaknesses in how you handle personal information—before they can escalate into a privacy breach.
Its primary purpose is to ensure you are meeting your legal obligations under Alberta's privacy laws by proactively addressing risks. This isn’t about finding fault; it's about building a stronger, more trustworthy foundation for your entire operation and demonstrating your commitment to protecting the personal information entrusted to you.
This forward-thinking approach makes a PIA so valuable. It forces you to map out exactly how personal data will move through your new system, from collection to secure destruction. This complete lifecycle view helps you detect potential issues early, long before they become costly problems to remediate.
It’s easy to confuse a PIA with a security audit, but they serve two distinct functions. A security audit typically focuses on the technical side—identifying vulnerabilities and protecting your IT infrastructure from external threats like hackers or malware. It asks, "Are our systems secure?"
A privacy impact assessment in Alberta, on the other hand, goes much deeper. It asks a different set of questions, all centred on the individual whose data you hold.
A PIA specifically examines:
While a security audit protects the container (your systems), a PIA protects the contents (the personal information). Both are necessary, but they are not interchangeable. You can have a highly secure system, but if the data inside is collected or used improperly, you are still non-compliant.
Ultimately, the goal of a PIA is to embed a "privacy by design" philosophy into your organization's culture. This means data protection is not an afterthought or a feature added at the end of a project. It is a core consideration from the moment a new idea is conceived.
By making the PIA a standard part of your project planning, you shift your organization's mindset from reactive compliance to proactive privacy management. This not only helps you meet legal requirements but also builds significant trust with your clients and stakeholders.
When you integrate privacy into the blueprint of your projects, you build systems that are more robust, resilient, and respected. It sends a clear signal to everyone—customers, employees, and regulators—that you take your data protection responsibilities seriously. This approach doesn't just prevent breaches; it builds a stronger, more trustworthy brand for the long term.
Knowing when to conduct a Privacy Impact Assessment (PIA) can feel challenging. Fortunately, Alberta's privacy laws provide clear signals—or "triggers"—that indicate when a PIA is not just a good idea, but a legal requirement. While not every software update requires one, any new project that fundamentally changes how you handle personal information likely will.
The objective is to shift from being reactive to proactive. Instead of waiting for a privacy issue to arise, the law requires you to address risks before you launch. Let's explore the specific triggers under Alberta’s key privacy acts to help you determine your obligations for your next project.
To clarify, here is a brief overview of how the different pieces of legislation compare and what might trigger a PIA under each one.
Each of these acts has its own focus, but the underlying principle is the same: if you're making a significant change to how you collect, use, or disclose personal information, you need to stop and assess the privacy implications first.
For most private businesses in Alberta, the Personal Information Protection Act (PIPA) serves as the rulebook. While PIPA does not explicitly mandate submitting a PIA to the Privacy Commissioner for every new initiative, its core principle of accountability effectively necessitates it.
PIPA places the responsibility squarely on your organization to protect the personal information you control. A PIA is the best tool to demonstrate that you have performed your due diligence, especially when planning initiatives such as:
Although submission to the regulator is not always required, conducting a PIA under PIPA is a prudent business decision. It prepares you to answer any questions from the Office of the Information and Privacy Commissioner (OIPC) and, equally important, builds trust with your customers. This is particularly true in specialized fields—for example, our guide on IT compliance for private career colleges shows how unique data handling in that sector demands this kind of careful review.
In the healthcare sector, the rules are much stricter. The Health Information Act (HIA) governs how "custodians"—such as hospitals, medical clinics, and pharmacies—handle highly sensitive patient health data. Under the HIA, it is mandatory to complete a PIA and submit it to the OIPC before launching any new administrative practice or information system that involves health information.
This is a non-negotiable rule. The HIA demands a PIA to ensure any new system or process has robust safeguards to protect one of the most private types of information.
Common triggers for a mandatory PIA under the HIA include:
Failure to complete and submit a PIA in these cases can lead to significant fines and a major loss of public trust.
A PIA under the HIA isn’t just about checking a compliance box. It’s a vital part of patient safety and care. It ensures privacy is baked right into the foundation of the technologies Albertans depend on for their well-being.
The Freedom of Information and Protection of Privacy (FOIP) Act covers all public bodies in Alberta, including government ministries, municipalities, universities, and school boards. Similar to the HIA, the FOIP Act makes PIAs mandatory in several specific scenarios.
A public body must conduct a PIA whenever it is creating a new system or program, or making major changes to an existing one that involves personal information. This is essential for ensuring government and public-sector projects are transparent and accountable with citizen data. The OIPC reviewed 42 PIAs in the 2022-23 fiscal year alone, demonstrating the seriousness of this requirement. You can get more details by reading the OIPC's full annual report.
Key triggers under the FOIP Act include:
By understanding these legal triggers, your organization can make informed decisions, maintain compliance, and properly protect the personal information entrusted to you.
Initiating a Privacy Impact Assessment (PIA) can feel like a significant undertaking, particularly for a medium-sized organization without a dedicated legal department. The best approach is to use a structured framework that breaks the process into manageable steps.
Think of it less as a single, overwhelming task and more as a clear, defined path. Each stage is designed to guide you toward compliance. This practical framework translates the formal process into an actionable, step-by-step guide your team can follow to systematically identify and address privacy risks, ensuring your projects align with Alberta's privacy laws from day one.
This flow chart shows the different legal acts that can trigger a PIA requirement for businesses, healthcare providers, and public bodies in Alberta.
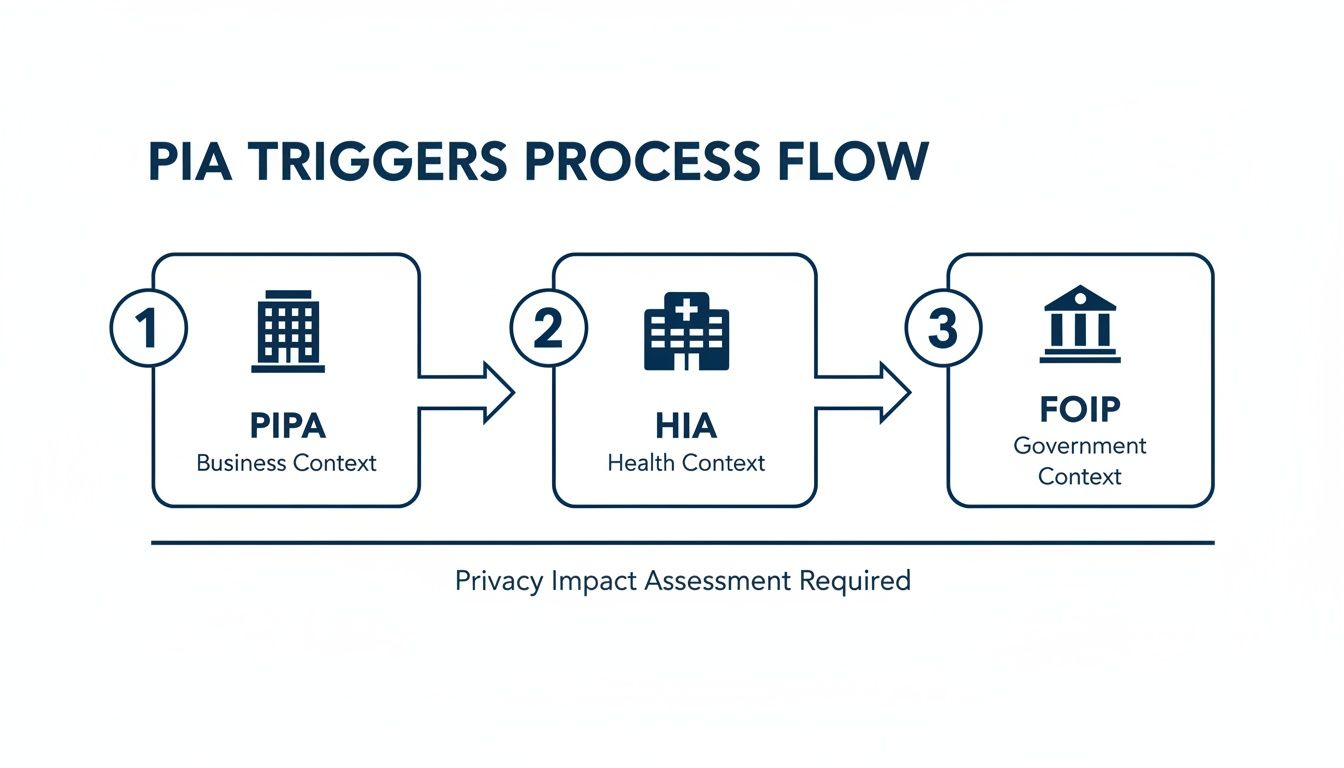
As you can see, different sectors face unique compliance paths, which is why a tailored approach to your PIA is so important.
This first step is foundational. Before delving into details, you must clearly define the project or system being assessed. Is it a new CRM, a cloud migration, or a new employee monitoring tool?
Once the project is defined, the next question is whether a privacy impact assessment in Alberta is legally required. You will need to review the triggers under PIPA, HIA, or FOIP to confirm. This is also the time to assemble a cross-functional team, including representatives from IT, project management, and any involved departments.
A word of caution: a poorly defined scope is a primary reason PIAs fail. If the boundaries are not clear from the start, you are likely to miss critical data flows or privacy risks.
Think of this stage as creating a detailed road map for every piece of personal information your project will touch. Your goal is to chart its entire journey, from collection to secure disposal.
You need to ask critical questions here:
This detailed map provides the visibility needed for the most critical phase of the assessment.
With your data map in hand, you can now begin to identify potential threats. A risk is any event that could lead to the unauthorized access, use, disclosure, or loss of personal information. The core of a PIA is this risk assessment, and a solid Security Risk Management Guide can offer a great framework for this process.
Consider risks from every angle:
For each risk you identify, evaluate its likelihood and potential impact. This helps you prioritize which issues require immediate attention.
Identifying risks is only half the battle; now you must address them. The goal is to develop specific controls to mitigate each identified threat. These mitigation strategies are the practical, real-world solutions that will reduce or eliminate privacy risks.
Examples of mitigation strategies include:
These strategies become part of your operational playbook and form the core of your data security management approach.
Once your analysis is complete and your mitigation plan is solid, it's time to compile everything into a formal report. This document serves as the official record of your due diligence. It should clearly outline the project's scope, the data flows, the identified risks, and the controls you are implementing to manage them.
If your organization is governed by HIA or FOIP, you must submit this report to the Office of the Information and Privacy Commissioner (OIPC) for review before the project goes live. Even if it is not mandatory under PIPA, a well-documented PIA is an invaluable asset that demonstrates your commitment to privacy.
A PIA is not a one-time task. It is a living document that must be revisited and updated as circumstances change. After your project launches, it is critical to monitor how well your privacy controls are working.
Schedule periodic reviews, especially if there are significant changes to the project—such as adding new features or integrating with another system. This continuous oversight ensures your privacy protections remain robust and effective over the long term, adapting to new threats and evolving business needs.
A Privacy Impact Assessment is not a generic, one-size-fits-all template. Its true value comes from applying it to your specific industry context. The privacy risks facing a Calgary health clinic are vastly different from those of a logistics company in Edmonton.
To conduct a privacy impact assessment in Alberta effectively, you need a firm grasp of your sector’s unique data flows, customer expectations, and regulatory pressures. This transforms your PIA from a simple compliance exercise into a powerful, practical tool for managing real-world risk.
Let's explore the specific privacy challenges and considerations for some of Alberta's key industries, using common scenarios to illustrate how this plays out in practice.
For organizations in Alberta's healthcare sector, the Health Information Act (HIA) sets an exceptionally high standard for data protection. The information handled is deeply personal and sensitive, making the stakes for privacy monumental. Custodians like clinics, hospitals, and pharmacies must be exceptionally diligent.
A classic example is a medical clinic launching a new online patient portal. While the goal of giving patients easier access to test results is commendable, this initiative automatically triggers a mandatory PIA under the HIA.
The assessment would need to focus on several critical areas:
The PIA process here is vital for building trust. Patients will only use new digital health tools if they have complete confidence that their most private health details are secure.
A PIA in healthcare isn't just about avoiding fines; it's a fundamental component of patient safety and trust. It validates that the technology intended to improve care doesn't inadvertently expose sensitive health information to risk.
In the legal and financial sectors, confidentiality is paramount. It is the bedrock of the client relationship. Firms in these fields manage solicitor-client privileged information, sensitive financial records, and personal identity data—all of which are prime targets for cybercriminals.
Consider a mid-sized accounting firm in Red Deer migrating its client files to a new cloud-based practice management system. A PIA for this project is essential and would need to address several key points:
Manufacturing and logistics firms in Alberta manage vast amounts of information, including sensitive employee files, proprietary operational data, and a growing stream of data from Internet of Things (IoT) devices.
For instance, a logistics company that installs GPS trackers and telematics sensors in its vehicles must conduct a PIA. While the goal is to optimize routes, this technology also gathers data on driver behaviour and location. The PIA must carefully balance business benefits against the privacy rights of employees, focusing on transparency and ensuring data collection is necessary. Educational institutions also face unique challenges, as we cover in our guide on cybersecurity for Alberta private career colleges.
This scenario highlights a core PIA principle: ensure that the personal information you collect is limited to what is reasonable and necessary to achieve a legitimate business goal. This rule applies across every sector, including the public sector. In 2024, the Alberta government split the FOIP Act into two new laws, introducing mandatory PIAs for over 300 public bodies, from municipalities to universities. You can read more about these major privacy changes for Alberta's public sector.
For any business without a dedicated compliance department, conducting a thorough Privacy Impact Assessment (PIA) can seem daunting. The deep technical analysis, risk identification, and mitigation planning all require specialized expertise that may not be available in-house.
This is where a managed IT services partner becomes a strategic asset. They can transform a complex compliance challenge into a smooth, manageable process that supports your business growth.
Working with an IT expert simplifies every stage of the PIA. A good IT partner's process naturally includes the technical deep-dive required for a successful privacy impact assessment in Alberta, ensuring your new projects are not just technologically sound, but fully compliant from day one.
When you engage a managed IT services provider, you gain access to a team of specialists who can contribute to different parts of the PIA process. This collaborative approach ensures no technical detail is overlooked.
For instance, a Virtual CIO (vCIO) can offer high-level strategic direction at the outset, helping define the project's scope and map out technological risks. This leadership ensures the PIA aligns with your broader business goals.
Then, dedicated cybersecurity specialists can handle the technical details. These experts conduct vulnerability assessments for data storage, transmission, and processing systems. Their role is to identify potential weaknesses before they become problems, which forms the core of your risk analysis. You can learn more about this model in our guide on the benefits of managed IT services.
Identifying risks is only half the job. The true value of an IT partner is evident when it comes time to implement strong, practical controls to mitigate those risks.
A great managed IT partner doesn't just find problems; they provide practical, effective solutions. They translate the abstract risks identified in a PIA into concrete security measures that protect your data and your business.
Based on their findings, cybersecurity experts will recommend and implement specific, layered controls to keep personal information safe. These are not generic fixes; they are solutions tailored to the risks uncovered during the PIA. These could include:
By integrating these technical safeguards directly into your project's design, a managed IT partner ensures your new initiatives are both compliant and secure from the start.
Understanding the requirements for a privacy impact assessment in Alberta can be challenging. To provide clarity, here are straightforward answers to the questions we hear most often from business leaders.
The timeline for a PIA can range from a few weeks to several months, depending on the complexity of your project. A new software system handling a small amount of personal data might be completed relatively quickly.
Conversely, a major initiative—like launching a new patient portal under the Health Information Act (HIA)—demands a much deeper analysis. These projects involve detailed data mapping, vendor security vetting, and multiple rounds of feedback, which naturally extends the timeline. The key takeaway is to start the PIA process early to keep your project on schedule.
Failing to conduct a required PIA, especially when it's mandatory under HIA or FOIP, can lead to serious consequences. The Office of the Information and Privacy Commissioner (OIPC) of Alberta has the authority to investigate and can issue orders to halt your project until you are compliant.
Beyond regulatory action, the financial penalties for non-compliance can be substantial. More importantly, if a privacy breach occurs due to a failure to assess risks, the damage to your organization's reputation and the loss of customer trust can be irreversible.
Think of a PIA as more than just a legal checkbox; it's a fundamental risk management tool. Skipping it is like building a house without checking the foundation—you're risking a very expensive collapse down the road.
While you are not legally required to hire a lawyer for your PIA, their expertise can be incredibly valuable, especially for complex projects or those involving highly sensitive information. A privacy lawyer can help you navigate the nuances of PIPA, HIA, or FOIP and ensure your report meets OIPC standards.
However, many organizations successfully complete PIAs with an internal team. By bringing together key individuals from IT, operations, and management, you can cover all necessary bases. Partnering with a managed IT services provider is another effective way to fill technical gaps, helping you identify and mitigate risks without the expense of a full-time legal team.
Not always. A minor software update or a simple security patch typically does not require a new PIA. The critical question to ask is: does the upgrade significantly change how you collect, use, store, or share personal information?
For example, if a CRM upgrade adds new analytics features that profile customers in a new way, then a new PIA (or an addendum to the existing one) is advisable. However, if the update is limited to bug fixes with no changes to data handling, you are likely in the clear. Always evaluate what is changing before you proceed.
Navigating the complexities of a Privacy Impact Assessment doesn't have to be a burden. At CloudOrbis Inc., our team of IT and cybersecurity experts can guide you through every step, ensuring your projects are secure, compliant, and ready for success. Learn more about our managed IT and compliance solutions.

January 26, 2026
Canada's Top 7 Managed IT Services Companies for 2024Searching for managed IT services companies? Explore our 2026 roundup of Canada's top 7 providers for SMBs in Toronto, Calgary, and Edmonton.
Read Full Post
January 25, 2026
Choosing the Right IT Support Company in Edmonton for Your BusinessLooking for it support company edmonton? Compare providers, pricing, and cybersecurity essentials to choose the best IT partner for your Alberta business.
Read Full Post
January 24, 2026
Edmonton IT Support: A Guide for Local BusinessesDiscover how edmonton it support can fortify operations, boost efficiency, and unlock growth for your business with the right partner.
Read Full Post