
February 3, 2026
Proactive IT Maintenance Calgary: Prevent Downtime and Secure Your BusinessUnlock uptime with proactive it maintenance calgary, delivering secure IT systems and practical strategies for Calgary businesses.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
December 18, 2025

Effective cybersecurity for Alberta private career colleges is not just about installing the latest software; it is about building a layered defence to protect your institution’s most valuable assets. We are talking about sensitive student data, financial records, and the intellectual property that makes your college unique. With threats like ransomware and phishing constantly lurking, you need a smart, proactive strategy that aligns with Alberta's PIPA regulations and goes beyond simple IT fixes to create a truly resilient campus.

In Alberta's competitive education sector, private career colleges are standing at a crossroads. The rising tide of cyber threats means an attack is no longer a question of if, but when. For an institution entrusted with vast amounts of personal information, a passive approach to security is a direct risk to your operations, your reputation, and even your licence.
This guide provides a clear, actionable framework to protect your college. We will skip the jargon and get straight to practical strategies for defending against the real-world threats you face today.
Cybercriminals see educational institutions as high-value targets, and for good reason. Your college is a central hub for the exact kind of information they want to steal and exploit. Understanding why you are in their crosshairs is the first step toward building a defence that works.
Here is why your college is so attractive to them:
The real threat is not just about stolen data; it is about operational paralysis. A successful ransomware attack can lock down your entire student information system (SIS) during peak enrolment or block access to your learning management system (LMS) during final exams, creating absolute chaos.
Picture this: a well-crafted phishing email lands in an admissions officer's inbox. One click is all it takes to unleash ransomware that encrypts every single student record, grinding your operations to a halt. Suddenly, you cannot process applications, retrieve transcripts, or meet your government reporting deadlines. This is not just a frightening scenario; it is a tangible risk that demands a serious, structured response.
This guide will walk you through everything from understanding your legal obligations under Alberta's PIPA to implementing a layered defence system. We will also explore how to turn your staff and students into your strongest security assets, building a resilient, cyber-aware campus culture. The goal is to give you the knowledge to build a robust cybersecurity for Alberta private career colleges strategy that truly protects your institution.
For private career colleges in Alberta, navigating privacy legislation can feel like a maze. The legal jargon in Alberta’s Personal Information Protection Act (PIPA) is dense, and it is easy to get lost. However, understanding these rules is not just a box-ticking exercise; it is the absolute foundation of your entire cybersecurity plan.
Think of it this way: you are the guardian of your students' data, much like a trustee managing a physical trust fund. You have been entrusted with protecting its contents, and that duty is a serious legal requirement, not just a friendly suggestion. Breaching that trust has real consequences.
At its core, PIPA demands that you safeguard the personal information you collect, use, and store. This is about more than just stopping hackers; it is about earning and keeping the trust of your students and fulfilling your legal role as a data custodian.
PIPA revolves around a single, powerful idea: reasonableness. The law requires you to have "reasonable security arrangements" in place to protect personal information. But what does "reasonable" mean for a busy college juggling admissions, classes, and student services?
It simply means your security measures must match the sensitivity of the data. For example, a student’s financial aid application or academic transcript is far more sensitive than a simple contact form from your website. Those high-stakes records demand stronger protections, like robust encryption and tightly controlled access.
PIPA also sets clear rules for how you obtain permission to handle data. You must:
A critical piece of the PIPA puzzle is accountability. Your college must officially designate someone to be responsible for meeting these privacy obligations. This creates a clear line of ownership and ensures someone is steering the ship.
Following this framework is not just about dodging fines; it is about building a culture that respects privacy. Proper data security management covers the entire lifecycle of information, from the moment you collect it to when you securely dispose of it.
While PIPA is your go-to legislation in Alberta, it does not exist in a bubble. The federal Personal Information Protection and Electronic Documents Act (PIPEDA) can also come into play, especially as your college’s reach grows.
PIPEDA typically applies when personal information crosses provincial or international borders for commercial activities. So, if you offer online programs to students living in British Columbia or Saskatchewan, you will likely need to comply with PIPEDA for those specific interactions.
This might sound complicated, but there is good news. Alberta's PIPA is considered "substantially similar" to PIPEDA. This means their core principles—consent, accountability, and safeguarding data—are closely aligned. The key is to know which law applies to which student and ensure your policies are robust enough to cover all your bases.
To help clarify the overlap and distinctions, here is a straightforward comparison of how these two laws might apply to your college's activities.
Ultimately, while PIPA governs your day-to-day local operations, understanding PIPEDA is essential for any college with students outside Alberta, ensuring you meet privacy standards no matter where your students are learning from.
To build an effective defence, you first need to know what you are up against. Cyber threats are not just abstract concepts; they are specific, targeted attacks designed to exploit the unique vulnerabilities of educational institutions. For Alberta’s private career colleges, this means getting real about the tactics criminals use to disrupt operations, steal data, and extort money.
Now that we have covered the legal side, let's explore the operational reality. We will break down the most common and damaging threats your college is likely to face. This is not about fearmongering; it is about building situational awareness so you can put your resources into the right protections.
Ransomware is one of the most destructive threats out there, and it is especially crippling for a college. In this scenario, attackers infiltrate your network and encrypt everything critical—from student records in your SIS to course materials on shared drives—making them completely useless.
They then demand a hefty ransom, usually in cryptocurrency, to provide the decryption key. However, paying is a huge gamble. There is no guarantee you will get your data back, and it essentially paints a target on your back for future attacks.
Real-World Example: Imagine it is the week before final exams. A ransomware attack hits, locking down your Learning Management System (LMS). Suddenly, no one can access course materials, submit assignments, or take their finals. The attack brings learning to a dead stop, creating chaos and putting the entire academic calendar at risk.
Phishing remains a top threat because it targets your most unpredictable asset: your people. These attacks use deceptive emails, texts, or messages that appear to be from a legitimate source—a bank, a government agency, or even your college's president. The goal is simple: trick a staff member or student into giving up their login credentials or clicking a malicious link.
Spear-phishing is the more dangerous, targeted version of this. Attackers research your college to craft highly personalized emails. They might impersonate a senior administrator and instruct the finance department to make an "urgent" wire transfer. Because the request seems legitimate and time-sensitive, a busy staff member can easily fall for the trap.
A Distributed Denial-of-Service (DDoS) attack is not about theft; it is about pure disruption. Attackers flood your college’s website, online application portal, or LMS with a massive wave of junk traffic from thousands of compromised computers.
This digital traffic jam makes your online services grind to a halt, blocking students, staff, and prospective applicants from getting in. For a career college, a DDoS attack during peak enrolment season can mean a huge loss in revenue and a seriously damaged reputation.
Not all threats come from outside your walls. An insider threat can come from current or former employees, contractors, or even students who have authorized access to your systems. These threats can be malicious, but often, they are accidental.
In Alberta's vibrant educational landscape, private career colleges are stepping up to meet the surging demand for cybersecurity experts, especially as the province grapples with a shortage of skilled professionals. By focusing on practical skills amid rising cyber incidents—such as phishing attacks that spiked 20% in Canadian education sectors in recent years—these programs help ensure institutions remain resilient. It is also worth understanding cryptographic flaws and authentication bypass risks to get a fuller picture of the threat landscape.

Effective cybersecurity for Alberta private career colleges is not about having a bottomless budget. It is about building a smart, layered defence. Think of it like securing your physical campus. You would not just rely on a front gate. You would also have locked doors, secure offices for sensitive records, and perhaps security cameras. Your digital security needs that same layered mindset.
Building this digital fortress means putting the right security controls in place—ones that work together to protect your students, staff, and institutional data. Each layer has a specific job, making it progressively more difficult for an attacker to get through. Let's walk through the absolute essentials.
Your network is your digital campus, and its edge—the perimeter—is your first line of defence. This is where you control what comes in and what goes out. The most critical tool for this job is a modern firewall, which acts like a security guard at the main gate, inspecting all traffic and turning away anything that looks suspicious.
A properly configured firewall is non-negotiable. It works best alongside secure Wi-Fi networks. This means segmenting your network into different zones—one for students, another for staff, and a separate, more secure one for critical admin systems. That way, if a student's laptop gets compromised on the student network, the infection cannot easily spread to your financial records.
An endpoint is any device connected to your network: laptops, desktops, servers, and even tablets. Every single one is a potential doorway for an attacker. Protecting these endpoints is like putting a solid lock on every door and window across your entire campus.
This is not about old-school antivirus anymore. Today's endpoint protection is far more advanced, designed to spot and shut down sophisticated threats like ransomware before they can lock up your files. Every college-owned device must have this protection installed and kept current.
A single unprotected staff laptop can compromise your entire network. Endpoint security ensures that even if a threat slips past your firewall, it is stopped in its tracks before it can cause real damage.
Once someone is on your network, you still need to control what they can actually do. This is where Multi-Factor Authentication (MFA) becomes your best friend. Think of it like needing both a keycard (your password) and a unique PIN code sent to your phone to get into a high-security room.
MFA makes stolen passwords almost worthless to a hacker. It should be mandatory for accessing all your key systems, including:
Turning on MFA is one of the most powerful security moves you can make. It drastically cuts the risk of account takeovers, which are the starting point for many major data breaches. Many schools find that a partner providing security managed services can help roll out these controls efficiently across the entire institution.
Even with strong defences, you must plan for the worst-case scenario. That is why protecting your data directly is so important. The two pillars of data protection are encryption and backups.
Encryption scrambles your sensitive data, making it unreadable without the right key. All important student and financial information should be encrypted, both when it is stored on your servers ("at rest") and when it is being sent over the network ("in transit").
Backups are your ultimate safety net. If your data is ever lost, corrupted, or held for ransom, a reliable and automated backup system lets you restore it and get back to business. Just follow the 3-2-1 rule: keep three copies of your data on two different types of media, with one copy stored safely off-site.
Finally, you need eyes on your digital campus. Proactive monitoring tools like a Security Information and Event Management (SIEM) system act as your digital security cameras. They collect log data from all your systems, analyze it for unusual activity, and flag potential threats in real time.
This proactive approach is essential for catching threats early, long before they turn into a full-blown crisis. As educational institutions in Alberta grow, so does the need for these hands-on cybersecurity skills. Northern Lakes College, for instance, recently launched new cybersecurity courses with EC-Council, using cloud-based virtual labs to give students hands-on practice in threat detection and incident response, which you can read more about on their news page.
Your firewalls and endpoint protection are crucial, but they are only as strong as the people using them. All it takes is one well-meaning staff member clicking on a malicious link, and you could be facing a campus-wide crisis. That is why turning your people from potential weak spots into your first and best line of defence is likely the highest-return investment you can make.
Building a cyber-aware culture is about much more than a mandatory, once-a-year slideshow that everyone clicks through. It is about weaving security into the daily fabric of college life for every student and staff member. The goal is to make good security habits as automatic as locking the office door on your way out. For cybersecurity in Alberta private career colleges, a strong security culture is not just a "nice-to-have"—it is a core pillar of your entire strategy.
The first hurdle is a mental one. Most people see cybersecurity as "the IT department's problem," but that is a dangerous misconception. In reality, it is a shared responsibility. An effective awareness program does not just tell your community what to do; it explains why it matters in a way that connects with their day-to-day work.
Your training must be practical, engaging, and directly tied to the threats your college actually faces. Forget generic advice. Key topics should include:
The core message should be simple and powerful: "When in doubt, report it." A handful of false alarms is a small price to pay to catch a real threat before it brings your college's operations to a grinding halt.
Let's be honest—passive learning does not work for this subject. To build a genuinely vigilant campus culture, you must make the training interactive and ongoing. People learn best by doing, which is where running real-world simulations becomes so incredibly valuable.
One of the most effective tools in your arsenal is the simulated phishing campaign. These are safe, controlled tests where you send harmless phishing emails to your staff to see who takes the bait. The goal is not to punish anyone. It is to create a powerful, private "aha!" moment that reinforces the training and gives you hard data on where you need to focus your efforts. This hands-on experience hammers the lesson home far better than any manual ever could.
Ultimately, investing in your people's awareness is the single most powerful security control you can deploy.
Knowing you need to improve your cybersecurity is one thing; actually doing it is another. A detailed strategy document can feel overwhelming, but a structured roadmap breaks that big plan into a series of smaller, manageable steps. For Alberta private career colleges, taking a phased approach is the key to avoiding burnout and building a strong security posture one layer at a time. This is not a race—it is about methodically building a resilient digital campus.
This roadmap splits the journey into four distinct phases. It is designed to guide your institution from its current state to a mature and defensible security framework, giving you a clear way to track progress and demonstrate due diligence to both stakeholders and regulators.
Before you can build, you need to understand the lay of the land. This initial phase is all about discovery and documentation. After all, you cannot protect what you do not know you have. The goal here is to get a completely honest picture of your current security posture—your strengths and, more importantly, your most critical vulnerabilities.
Key actions for this phase include:
This foundational work gives you the clarity you need to make smart, risk-based decisions in the phases to come.
With a solid understanding of your assets and risks, it is time to put your foundational security controls in place. These are the tools that deliver the biggest protective punch. Think of this phase as installing strong locks and reinforced doors on your digital campus. These are the non-negotiables that shut down the most common attack methods.
Your focus should be on:
Technology alone is never enough. This phase shifts the focus from tools to people and processes. A strong security culture, backed by clear policies, transforms your staff and students from potential targets into your first line of defence.
This simple process is the core of building a vigilant cyber culture: training people to spot threats, giving them a clear way to report them, and then reinforcing that knowledge over time.
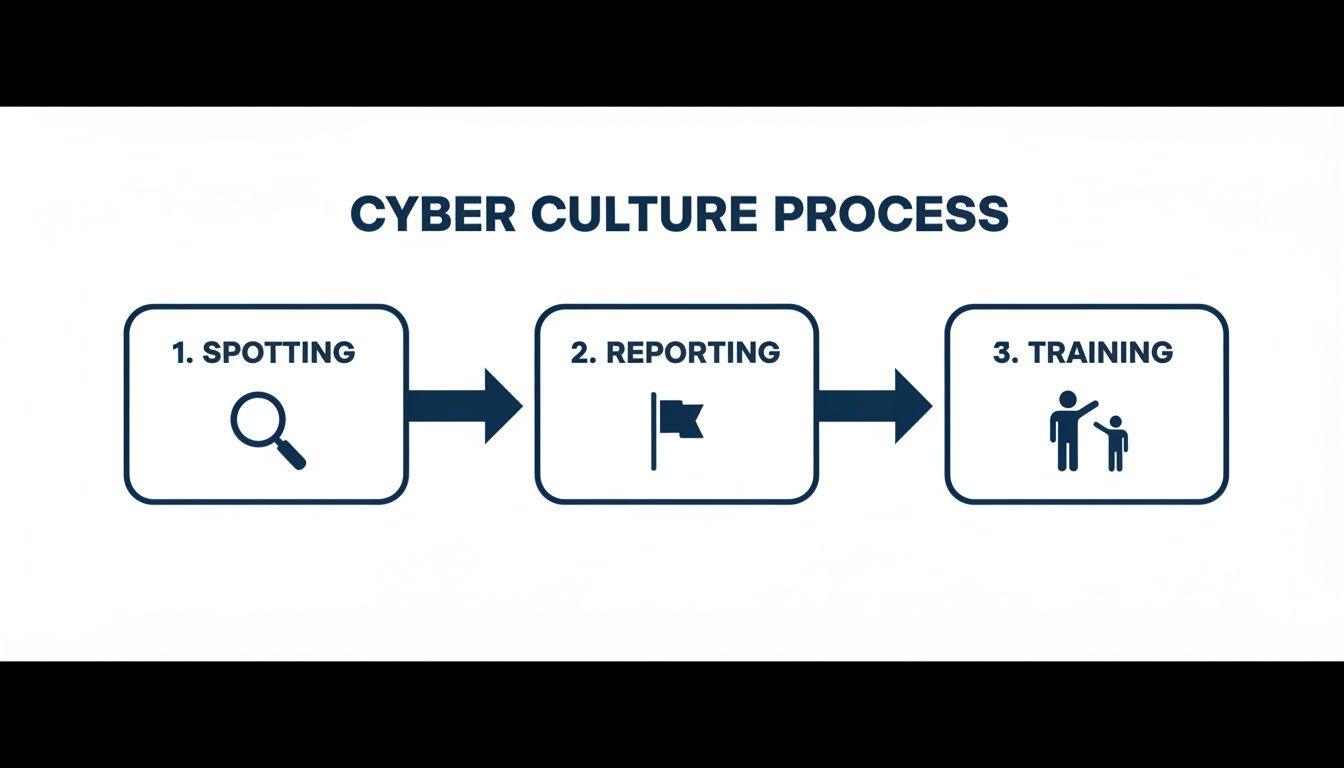
This visual drives home the point that a successful defence is not a one-time event; it is a continuous loop of awareness, action, and education.
Essential actions for Phase 3 are:
Cybersecurity is not a project you finish; it is a program you run. This final phase is all about maturing your defences and embracing a cycle of continuous improvement. The goal is to shift from a reactive stance ("we were hacked") to a proactive one ("we are hunting for threats").
You can mature your program by:
Successfully implementing a roadmap like this requires the right resources. It is worth exploring the best practices for securing technology grants for private schools to help fund these critical initiatives. This roadmap provides a clear path to a strong cybersecurity for Alberta private career colleges program, ensuring your institution stays resilient for the long term.
This checklist provides a high-level guide for private career colleges beginning their cybersecurity journey, outlining key actions and their primary goals for each phase of the implementation roadmap.
Using a structured checklist like this turns a complex program into a series of achievable milestones, helping your team stay focused and track progress effectively.
For most private career colleges in Alberta, building and maintaining an in-house cybersecurity team is not realistic. The expertise required is expensive, specialized, and incredibly hard to find. This is where a strategic partnership with a Managed Security Service Provider (MSSP) can make all the difference, shifting your security posture from reactive to proactive.
Choosing a partner is a critical decision that goes beyond technical skills. You need a provider who feels like a genuine extension of your team, not just another vendor on the payroll. The right partner understands the unique operational pressures and the specific regulatory landscape that define cybersecurity for Alberta private career colleges.
When you are evaluating potential MSSPs, you must look past the generic sales pitches and dig into their specific, verifiable expertise. A partner who can truly protect your college will have a few key characteristics.
Look for a provider with:
Finding the right provider means selecting a team that offers more than just tools; they should provide ongoing strategic guidance. They will help you navigate future threats and adapt your defences as your college grows and the threat landscape changes.
To find a partner who truly aligns with your college's needs, you need to ask targeted questions that reveal their real capabilities. For instance, the Southern Alberta Institute of Technology (SAIT) has a model that influences many private career colleges to prioritize industry-aligned training in areas like ethical hacking and digital forensics. This highlights the need for a partner who can support a secure and modern educational environment. You can learn more about their advanced programs to get a sense of the level of expertise needed today.
Your partner must understand the context behind your security needs. By asking detailed, insightful questions, you can ensure you find a provider who will protect your operations, your reputation, and your future. For more insights into what a specialized provider can offer, explore our detailed overview of a professional cyber security service.
At CloudOrbis, we deliver the specialized cybersecurity and managed IT services that Alberta's private career colleges need to stay secure, compliant, and focused on student success. Contact us today for a professional assessment to safeguard your institution's future. https://cloudorbis.com

February 3, 2026
Proactive IT Maintenance Calgary: Prevent Downtime and Secure Your BusinessUnlock uptime with proactive it maintenance calgary, delivering secure IT systems and practical strategies for Calgary businesses.
Read Full Post
February 2, 2026
A Guide to IT Compliance for the Alberta Oil & Gas IndustryMaster it compliance for alberta oil & gas industry with a practical, click-ready guide on AER/TIER, cybersecurity controls, and audit readiness.
Read Full Post
February 1, 2026
A Guide to IT Compliance Needs for Alberta Private Career CollegesExplore it compliance needs alberta private career college with practical guidance on PIPA, the PVT Act, and core security controls to protect student data.
Read Full Post