
February 22, 2026
SharePoint Migration Calgary: A Practical Guide for Your BusinessExplore SharePoint migration Calgary with a step-by-step plan for governance, compliance, and a smooth cloud transition.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
November 23, 2025

When you hear "cyber security service," what comes to mind? It's more than just installing antivirus software and calling it a day. A proper cyber security service is a comprehensive offering that brings together expert teams, advanced technology, and around-the-clock monitoring to protect your company's digital assets from a sea of online threats.
For most medium-sized organizations, it’s like having an outsourced security department—one with specialized skills you likely couldn't build in-house. They’re the ones shielding your business from data breaches, ransomware, and all the other malicious attacks you read about in the news, allowing your business and IT leaders to focus on strategic growth.

Think of a cyber security service as a high-tech security firm for your digital world. It is not just an alarm system; it’s a dedicated team of experts managing your entire security operation 24/7. They are the ones who install the locks (firewalls), watch the surveillance cameras (threat detection), and act as your first responders in an emergency (incident response).
This service becomes a true extension of your team. It provides the constant vigilance and deep expertise needed to protect what matters most: your data, your reputation, and the trust your customers have in you. For business and IT leaders, this means you can finally shift the immense burden of security from your internal staff to a partner whose entire focus is staying one step ahead of attackers.
If you want to dig deeper into the basics, you can explore our detailed guide on what is cybersecurity.
To truly understand what a cyber security service does, it helps to break it down into its core functions. These are the primary roles a professional provider fulfills to keep your business safe.
A professional service is built on three critical pillars that work in harmony to create a rock-solid defence for your organization. Understanding how these functions operate shows the real value they bring to the table.
A comprehensive cyber security service integrates these three functions—protection, detection, and response—into a single, coordinated strategy. It’s this seamless integration that turns reactive measures into a proactive security posture, safeguarding your business against an ever-evolving threat landscape.
Ultimately, partnering with a cyber security service provider gives you access to enterprise-grade tools and a deep bench of talent that would otherwise be out of reach. This approach lets you secure your operations effectively, maintain compliance, and get back to focusing on your core business goals with peace of mind.
The ground has shifted. For Canadian businesses, digital threats are no longer a distant "what if"—they're a daily reality. Attackers have become more organized and their methods more calculated. For many medium-sized companies, proactive security is no longer just an IT line item; it’s a core requirement for survival.
This isn't simply about protecting data. It's about protecting your entire operation. A single breach can bring productivity to a grinding halt, shatter the customer trust you've spent years building, and lead to staggering financial penalties. Simply put, ignoring this reality is a gamble no business can afford to take.
Cyber attacks are becoming more frequent and far more sophisticated. Attackers now operate like well-oiled machines, deliberately targeting organizations they see as holding valuable data but having weaker defences. Unfortunately, medium-sized businesses often fit that description perfectly.
Many business leaders fall into the trap of thinking, "we're too small to be a target," but the truth is the exact opposite. Cybercriminals see smaller businesses as valuable entry points into larger supply chains or easy targets for a quick ransomware payday. You can get a full breakdown of the top cybersecurity threats SMBs face in our other guide.
Sectors like hospitality, which process a high volume of transactions and sensitive guest information, are especially vulnerable. High staff turnover and the use of seasonal workers can create security gaps that attackers are all too eager to exploit.
The global threat is accelerating at an alarming rate. As a stark example, organizations in the Caribbean are now weathering an average of 2,582 cyber-attacks per week—a figure 40% higher than the global average. This escalating aggression highlights just how critical it is for every business to reinforce its defences.
This data paints a clear picture: attackers are relentless and opportunistic. A passive or outdated security setup is an open invitation for a disaster.
One of the biggest mistakes a business can make is viewing a professional cyber security service as just another IT expense. It is time to reframe that thinking. This is a strategic investment in your company's future—one that protects revenue, guarantees operational continuity, and allows you to grow securely.
Think about the real cost of a breach, which goes far beyond the initial financial hit:
Investing in a robust cyber security service is an investment in resilience. It gives you the freedom to focus on your core business, confident that a dedicated team is protecting your digital foundation 24/7. This proactive approach isn't just a good idea; it's essential for keeping your competitive edge and securing your company's future.
Navigating the world of cyber security services can feel like trying to read a map in a foreign language. With an alphabet soup of acronyms like MDR, VAPT, and SOC, it’s easy for business leaders to feel overwhelmed. But understanding what these services do is the first step toward making a smart decision that protects your business.
Each type of cyber security service is designed to solve a different problem. Some are built for proactive defence, like scouting for weaknesses before an attack happens, while others are all about real-time threat hunting. Choosing the right mix comes down to your company's specific risks, how you operate, and any compliance rules you need to follow.
One of the most foundational services is Vulnerability Assessment and Penetration Testing (VAPT). Think of this as hiring a team of ethical "burglars" to test the locks on your digital doors and windows before a real criminal does. Their entire job is to find and document every potential way into your network.
A vulnerability assessment is the first part—a systematic inspection using automated tools to scan for known weaknesses, like outdated software or misconfigured firewalls. A penetration test takes it a step further. Here, security experts actively try to exploit the weaknesses they find, showing you exactly how a real attacker could break in.
The goal is to provide a clear, actionable report detailing your security gaps so you can fix them long before they get exploited. This turns a potential disaster into a manageable to-do list.
While VAPT is a proactive check-up, Managed Detection and Response (MDR) is your 24/7 security guard on active patrol. MDR services operate on the assumption that some threats will inevitably get past your initial defences. Their focus is on finding and neutralizing those threats before they escalate into a full-blown crisis.
MDR providers deploy advanced tools across your network, servers, and endpoints (like employee laptops) to constantly hunt for signs of an attack. They blend sophisticated technology with sharp human expertise to analyze alerts, investigate suspicious activity, and respond to confirmed threats in minutes.
This service is a lifeline for businesses that cannot afford their own round-the-clock security team. It provides the constant vigilance needed to catch stealthy attacks that might otherwise go unnoticed for weeks, dramatically reducing the potential for damage. To see how this fits into a bigger picture, our guide on MSSP security services offers more context.
The core value of an MDR service is its speed and expertise. It shrinks the "dwell time"—the critical window between an attacker getting in and being discovered—from an industry average of several weeks down to just minutes or hours.
A Security Operations Centre (SOC) as a Service is the central command hub for your entire security operation. It brings together people, processes, and technology under one roof to give you a unified view of your security posture. A SOC team is responsible for monitoring all your security tools, analyzing threat intelligence, and coordinating the response to any incident.
For most medium-sized businesses, building an in-house SOC is simply out of reach due to the high cost of tools and the massive shortage of skilled security professionals. SOC as a Service gives you access to an enterprise-grade security hub for a predictable monthly cost.
This model ensures all your security efforts are working together effectively. For businesses using cloud platforms, understanding the options for mitigating cloud computing security risks is a key part of selecting services that a SOC can manage. By centralizing security management, you gain a powerful advantage in defending against today's complex threats.
To make things clearer, here’s a simple breakdown of these services. This table should help you quickly see the primary goal of each and determine which one might be the best fit for your business's current needs.
Ultimately, many businesses benefit from a combination of these services. A proactive VAPT assessment can uncover vulnerabilities, while MDR and a SOC provide the ongoing vigilance needed to protect your operations day in and day out.
Why the sudden explosion in cybersecurity spending? The way we do business has completely changed. Companies are flocking to the cloud, fully embracing e-commerce, and depending on digital tools for nearly everything. While this shift is great for efficiency and growth, it also massively expands the "attack surface"—all the potential entry points a cybercriminal could use.
Every new cloud server, employee laptop, and online payment portal is another potential weak spot. This growing digital footprint means a solid cyber security service is no longer just a defensive shield; it’s a core part of any modern business strategy. As everything becomes more connected, the financial and operational fallout from a breach gets bigger, pushing security from a backroom IT task to a top-of-mind boardroom issue.
The relentless push toward digital transformation is the main engine behind security spending. As businesses roll out more cloud-based applications and online platforms to serve their customers, they’re creating large stockpiles of sensitive data. This concentration of valuable information makes them an attractive target for attackers.
The market data tells the same story. In the Cyber Solutions market, 2025 revenue is expected to hit US$165.99 million, a surge driven by this digital rush in key sectors like finance and tourism. That number shows that businesses are finally recognizing the risks and investing to protect themselves. You can dig deeper into these numbers to understand the full scope of cybersecurity investment drivers.
It’s not just about stopping bad actors. Another huge driver is the ever-increasing weight of government regulations. Data privacy is no longer a suggestion—it's the law, and it comes with serious fines. If your business handles customer information, you must adhere to a strict set of rules.
Here in Canada, for instance, the Personal Information Protection and Electronic Documents Act (PIPEDA) lays down the law on how private companies can collect, use, and share personal data. A slip-up can lead to fines large enough to cripple a medium-sized business. We see the same trend globally, with regulations like the Jamaica Data Protection Act holding companies accountable for how they handle data.
Investing in a professional cyber security service is no longer just about preventing attacks. It is a critical step toward ensuring regulatory compliance, avoiding costly fines, and demonstrating to your customers that you are a trustworthy steward of their data.
This regulatory climate changes the game entirely. Security is not just an internal best practice anymore; it's a public promise to your customers. Proving you’re compliant often means you need sophisticated monitoring, regular vulnerability checks, and detailed reports—all things a specialized cyber security service is built to handle. For business leaders, partnering with a security expert has become an essential part of managing risk and staying on the right side of the law.
Choosing a cybersecurity provider is one of the most critical decisions you will make for your business. This is not like picking a software subscription; you are looking for a genuine partner who will become an extension of your own team. The right fit is someone who understands your business goals, your industry's specific pressures, and brings the deep expertise needed to protect you around the clock.
The selection process needs to be careful and deliberate. You are handing over the keys to your most critical digital assets, so a casual vendor relationship will not suffice. The goal is to find a team that will stand shoulder-to-shoulder with you, offering clear communication and a solid plan of action when a threat inevitably appears.
First and foremost, any potential partner must have serious technical capabilities. Their team should hold recognized industry certifications and have a proven track record of handling complex security situations for businesses like yours. Do not be shy—ask them tough questions about their experience with specific threats like ransomware or business email compromise.
A provider’s expertise also shines through in the tools they use. They should be working with top-tier security technologies and be able to explain exactly how that toolkit will shield your specific environment. This level of technical depth is the absolute foundation of any effective cyber security service.
A true security partner doesn't just sell you a product; they integrate into your operations. They should be able to articulate a clear incident response protocol, explaining exactly what happens—step-by-step—from the moment a threat is detected to its complete resolution.
Every industry has its own unique security challenges and regulatory hurdles. A provider that specializes in healthcare, for instance, will have a much stronger grasp of PIPEDA compliance than a generalist firm. Always ask for case studies or references from companies in your sector to see their experience in action.
This industry-specific knowledge ensures they understand your day-to-day operational reality. They will know which data is a prime target for attackers, what specific regulations you are bound by, and how to implement security measures without grinding your business to a halt. A tailored approach is always more effective than a generic, one-size-fits-all plan.
One of the biggest struggles for medium-sized businesses is the ongoing cybersecurity skills gap. Finding, hiring, and retaining top-tier security talent is incredibly difficult and expensive. This is where partnering with a managed service provider becomes a massive strategic advantage, giving you instant access to an elite team for a fraction of the cost. You can learn more about how this model works in our guide to choosing an IT outsourcing company.
The global shortage of skilled security professionals is a real problem. For instance, the Latin America and Caribbean region is struggling to find enough experts to manage rising cyber threats fueled by a growing reliance on digital platforms. This talent deficit means many organizations cannot fully implement necessary security measures, leaving them exposed. Read more about the global need for skilled cyber personnel on dawgen.global.
By partnering with a service provider, you solve this challenge overnight. You get a full team of specialists who are constantly training and staying on top of the latest threats, making sure your business has the brainpower it needs to stay safe. This lets you focus on your core business goals, confident that your security is in expert hands.
Choosing a cyber security service is a significant decision, and it’s about more than just technology. You are looking for a genuine partner who is committed to understanding how your business runs and is ready to provide the constant vigilance needed to protect it. The right provider delivers real peace of mind, not just tools.
At CloudOrbis, we believe this process should be clear, straightforward, and built on trust. We skip the sales pitch and focus on building a long-term security partnership. Our entire approach is designed to give you a precise roadmap, so you know exactly what to expect as we work together to strengthen your defences.
This simple workflow shows the core stages of finding the right security partner.
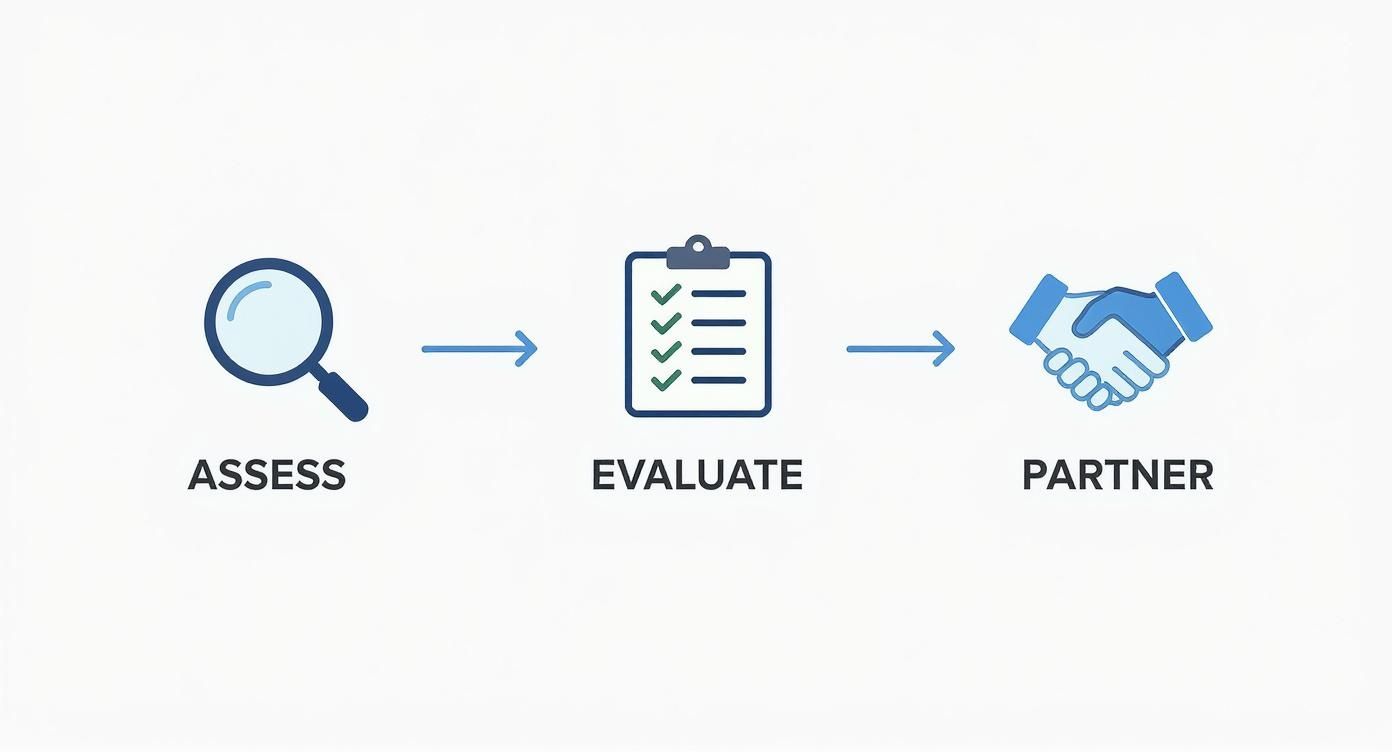
The journey starts with a deep dive into your current setup, moves to a careful evaluation of what you need, and ends in a strong partnership built for the long haul.
To make this journey tangible, we’ve refined a 10-step engagement process. This is not a generic checklist. It’s a structured methodology we’ve developed to build a security strategy that aligns perfectly with your business goals, ensuring a smooth transition with minimal disruption.
Here’s a glimpse of how it works:
What truly differentiates our service is our dedicated, 100% Canada-based team. Our security experts monitor your systems around the clock from our Security Operations Centre, giving you the constant oversight needed to spot and shut down threats in real time. This is about more than just software; it's about having a dedicated team of professionals protecting your business 24/7.
Partnering with CloudOrbis means you get an entire team of security specialists committed to your protection. We handle the complexities of cybersecurity so you can focus on what you do best—growing your business with confidence.
Ready to take the first step? Take a look at our comprehensive cybersecurity services to see how we can build a stronger, more resilient future for your organization. Let’s start a conversation about securing your business today.
When considering a professional cybersecurity service, many questions arise. This is understandable. Business leaders need straightforward, practical answers to see the real-world value and understand the logistics of outsourcing their digital defence. We will tackle the most common questions we hear.
Our goal here is to provide clear, concise information to help you get a handle on the big concerns: cost, implementation, and what you really get by partnering with a managed security expert.
There is no single price tag, as costs depend on your company's size, operational complexity, and the specific level of security required. Most providers, however, work on a predictable monthly subscription fee. This is almost always far more cost-effective than trying to hire, train, and retain an equivalent in-house security team.
More importantly, think of this proactive investment as a tiny fraction of what a data breach could cost. A single breach can result in regulatory fines, recovery expenses, and long-term damage to your brand's reputation. The only way to get a real number is to have a consultation; a proper risk assessment will provide a quote that fits your business.
While technically possible for large corporations with huge budgets, building an effective in-house security team is a monumental challenge for most medium-sized businesses. There's a global shortage of security talent, expert salaries are high, and the logistics of providing genuine 24/7 monitoring make it an impractical and expensive route.
Outsourcing to a managed security partner like CloudOrbis gives you immediate access to a dedicated team of specialists, advanced security tools, and round-the-clock protection for a predictable cost. This frees up your internal IT team to focus on projects that grow the business.
The first step is always a simple conversation to assess your unique situation. Any worthwhile provider will want to understand your business operations, your current IT setup, and your specific security concerns before recommending a solution.
At CloudOrbis, we kick things off with a discovery call to learn about your challenges and goals. This conversation is the start of our transparent 10-step engagement process, ensuring we build a security strategy that fits your business objectives perfectly. This structured approach guarantees a smooth and successful partnership from day one, giving you the robust protection you need to operate with confidence.
Ready to build a stronger, more resilient security posture? The team at CloudOrbis Inc. is here to help. Contact us today for a free consultation.

February 22, 2026
SharePoint Migration Calgary: A Practical Guide for Your BusinessExplore SharePoint migration Calgary with a step-by-step plan for governance, compliance, and a smooth cloud transition.
Read Full Post
February 21, 2026
Backup and Disaster Recovery in Calgary: A Guide to Business ResilienceLearn how backup and disaster recovery Calgary protects your business from threats, downtime, and financial loss with expert guidance.
Read Full Post
February 20, 2026
Microsoft 365 Security Calgary Businesses Can Depend OnIs your data secure? This guide to Microsoft 365 security Calgary businesses need covers key threats, compliance, and how to build a resilient defence.
Read Full Post