
February 14, 2026
Protect Your Business with Network Security Edmonton: A Practical GuideDiscover network security Edmonton strategies to protect your business from cyber threats. Practical tips, expert insights, and proven defenses.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
December 31, 2025

For any business in Edmonton, solid cybersecurity is more than just a technology issue—it’s a fundamental business strategy for protecting your data, ensuring operational continuity, and earning client trust. It acts as a multi-layered shield, defending your organization from threats like ransomware and data breaches through 24/7 monitoring, active threat detection, and an expert response team. Investing in robust security is a strategic move that builds resilience and enables confident growth.
Running a business in Edmonton means managing numerous complexities. Whether you’re handling intricate supply chains in the oil and gas sector or safeguarding sensitive patient data in a healthcare clinic, the threat of a cyberattack is a constant reality. This makes cybersecurity a core business function, not just an IT afterthought. For a medium-sized organization, a single breach can lead to devastating financial losses, damage to your reputation, and a complete halt to your operations.

The simplest way to view professional cybersecurity services is as your dedicated digital security team. Their sole focus is to protect your online assets with the same diligence you apply to your physical office or equipment. This guide is designed to cut through technical jargon and provide a clear, practical playbook for making informed security decisions for your business.
Effective cybersecurity extends far beyond installing basic antivirus software. It’s about building an organization that can withstand an attack and recover quickly. For businesses here in Edmonton, this means focusing on several key areas:
When you treat cybersecurity as a strategic investment rather than an expense, you empower your team to focus on their core responsibilities. A strong security posture enables innovation and growth, confident that your digital foundation is secure.
This guide will walk you through the specific threats facing Alberta's key industries and the core services that create a powerful defence. A foundational step for any organization is having a solid IT framework in place; our IT checklist for businesses in Edmonton can help you assess your current standing. From there, we’ll provide a clear roadmap for selecting the right security partner to protect your future.
Cybersecurity is no longer about lone hackers in basements. Today, your business faces organized, well-funded criminal enterprises that operate with professional efficiency.
Imagine your company as a digital fortress. These attackers are constantly scouting for weaknesses—an unlocked gate like a convincing phishing email, a poorly guarded tower like unsecured remote access, or even a compromised supply convoy in a supply chain attack.
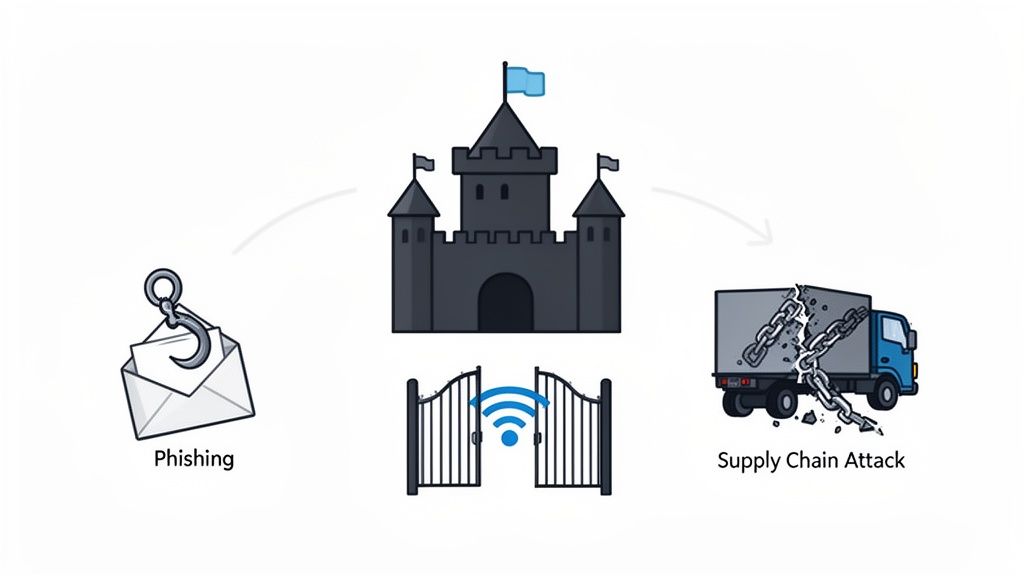
For businesses right here in Edmonton, these threats are not abstract. A local construction firm could have its project data held for ransom, bringing a multi-million dollar development to a halt. A financial services company on Jasper Avenue could be targeted by a phishing scam designed to siphon client funds. These scenarios are happening now, in our city.
The widespread shift to cloud computing and remote work has expanded every business's attack surface. Each employee working from home, every connected device, and every cloud application is a new potential entry point for attackers. In this environment, a proactive defence is not just advisable—it's essential for survival.
Attackers continually refine their methods, moving beyond simple viruses to far more sophisticated strategies. Edmonton SMBs are often viewed as ideal targets because they hold valuable data but may lack the enterprise-grade defences of a large corporation. The goal for these criminals is always to achieve maximum impact with minimum effort.
Here are the primary threats your organization is facing:
These are not threats you can counter with basic antivirus software. A multi-layered defence strategy managed by experts who understand the local landscape is required. You can dive deeper into our breakdown of the top cybersecurity threats facing SMBs to learn how to fight back.
Edmonton's growing reputation as a tech hub is a double-edged sword, attracting both innovation and cybercrime. This growth is part of a broader Canadian trend; the national cybersecurity solutions market is projected to reach USD $10.3 billion by 2034.
This expansion is fuelled by escalating cyber threats, ongoing digital transformation, and stricter regulations—all of which particularly affect Alberta's SMBs in healthcare, oil and gas, and manufacturing. While Ontario has historically led this space, Edmonton's job market growth indicates Alberta is rapidly catching up, making our city a key hub for both business and cyber risk.
The crucial takeaway for any Edmonton business leader is that your risk profile grows in tandem with your success. As your operations become more digital and interconnected, so do the opportunities for attackers to strike.
This new reality makes professional cybersecurity services in Edmonton a non-negotiable part of your business strategy. Proactive monitoring, continuous vulnerability assessments, and robust employee training are the cornerstones of a resilient organization prepared for future challenges.
Building a strong digital defence is like fortifying a castle—it requires more than a single wall to keep threats out. Real security comes from layers of specialized protection working in unison to cover every possible entry point. For any Edmonton business, understanding these core services is the first step toward building a truly resilient operation.
Let's break down the essentials, avoiding dense technical jargon to show exactly how each service shields your business.

To clarify these concepts, let’s examine how each service functions and the specific problems they solve for Edmonton businesses in sectors like healthcare, manufacturing, and finance.
Understanding this layered approach is key. No single service can do it all, but together, they create a formidable defence that keeps your business secure and operational.
Think of Endpoint Protection as the guards stationed at every door and window of your business. These "endpoints" include all devices connected to your network—laptops, servers, workstations, and mobile phones. Each one represents a potential entry point for an attacker.
Traditional antivirus software is no longer sufficient. Today’s endpoint protection uses sophisticated technology to identify and block advanced threats like fileless malware and zero-day exploits before they can execute and cause damage.
This service is fundamental. Without it, your entire network is at risk every time an employee opens an email or connects to public Wi-Fi at a local coffee shop.
While endpoint protection guards the gates, Managed Detection and Response (MDR) is your 24/7 surveillance team, actively hunting for threats that may have slipped past. This is a team of security experts using powerful tools to monitor your network around the clock.
If they spot suspicious activity, they don’t just raise an alarm. They immediately investigate, contain the threat, and neutralize it. It’s the difference between a simple burglar alarm and having a dedicated security force ready to respond instantly. For Edmonton businesses in logistics or manufacturing that operate outside of standard 9-to-5 hours, this constant vigilance is critical.
The real power of MDR is its proactive nature. Instead of waiting for a breach to happen, this service actively finds hidden threats, drastically reducing the chance of a catastrophic data loss or costly downtime.
Even the strongest fortress can develop weaknesses over time. Vulnerability Assessments are like having skilled engineers who regularly inspect your walls, towers, and gates for any potential flaws.
These assessments methodically scan your entire IT environment for security gaps, such as unpatched software, misconfigured systems, or weak passwords. You receive a clear, prioritized report showing exactly where you’re exposed and what actions are needed to fix it.
This process helps you stay ahead of attackers by closing security holes before they can be exploited. For businesses seeking an even more aggressive defence, it's worth reading our guide on what to expect from penetration testing services, which simulates a real-world attack to stress-test your defences.
No matter how strong your defences are, you must be prepared for a worst-case scenario. Data Backup and Disaster Recovery (BDR) is your foolproof contingency plan.
Imagine a fire, flood, or a crippling ransomware attack that encrypts all your files. BDR ensures that an up-to-date copy of all your critical business data is stored securely in a separate location. If a disaster occurs, you can quickly restore your systems and resume work with minimal interruption.
This service transforms a potentially business-ending catastrophe into a manageable incident. Instead of facing weeks of lost revenue and reputational damage, you are looking at a few hours of downtime at most. For any business in Edmonton, a solid BDR strategy is the ultimate safety net.
For many Edmonton businesses, compliance is not just a regulatory hurdle—it’s a core component of operating legally and earning client trust. Adhering to data privacy and protection laws is non-negotiable, but the complex web of regulations can often feel overwhelming.
The key is to move beyond legal jargon and focus on the practical, day-to-day steps needed to protect sensitive information.
Think of compliance as the specific set of blueprints you must follow when building your company's digital fortress. Ignoring these plans not only risks significant fines but also leaves doors open for cybercriminals. Demonstrating that you meet these standards signals to clients and partners that you are a trustworthy steward of their data, which is a powerful advantage in a competitive market.
If your business in Alberta handles any kind of personal information, understanding your obligations is the first step.
While many regulations exist, two stand out for their impact on businesses in our region. Each has its own rules, but both share the goal of ensuring personal information is handled with care and protected from unauthorized access. A partner providing cybersecurity services in Edmonton can translate these legal requirements into concrete technical controls for your business.
Here are the main regulations to keep on your radar:
Achieving compliance is not a one-time task; it requires a methodical approach. It means identifying where all your sensitive data resides, implementing the right safeguards to protect it, and creating clear policies for your team to follow. This is where a deep understanding of effective data security management becomes essential for long-term success.
The demand for professionals who can navigate these regulations is surging. Canada's cybersecurity job market is projected to grow at 8.20% annually through 2029, outpacing other sectors by nearly three times due to a shortage of skilled experts. Employers are placing a premium on compliance skills (27%) and cloud expertise, which is why partnering with local experts who integrate these skills into their services is critical for staying resilient.
Compliance isn't just about avoiding penalties; it's about building a security-first culture. When you prove that you can protect data according to rigorous standards, you build undeniable trust and open doors to new business opportunities.
This proactive approach also means securing data throughout its entire lifecycle. To meet regulatory requirements in Alberta, businesses must also consider processes like understanding data sanitization to ensure that information is permanently destroyed when no longer needed. By embedding compliance into your daily operations, you turn a legal requirement into a powerful tool for building a more secure and reputable business.
Selecting a cybersecurity provider in Edmonton is one of the most important decisions you will make for your business. This is not just about hiring a tech vendor; it’s about finding a strategic partner who understands the daily realities of your operation and is committed to protecting its future. The right choice can be the difference between business as usual and a catastrophic breach.
You must look beyond technical specifications. While expertise is essential, true value comes from a partnership built on trust, open communication, and a shared vision for your business goals. A reactive IT provider fixes things when they break. A true security partner works tirelessly to ensure they never break in the first place.
To find a partner who will genuinely strengthen your security, you need to ask the right questions. This is not about getting lost in technical jargon but about understanding their capabilities, processes, and investment in your success. A great partner will provide clear, straightforward answers that make business sense.
Begin your evaluation with these essential questions:
This infographic illustrates the fundamental process for meeting and maintaining compliance in Alberta—a journey your cybersecurity partner should be able to guide you through.
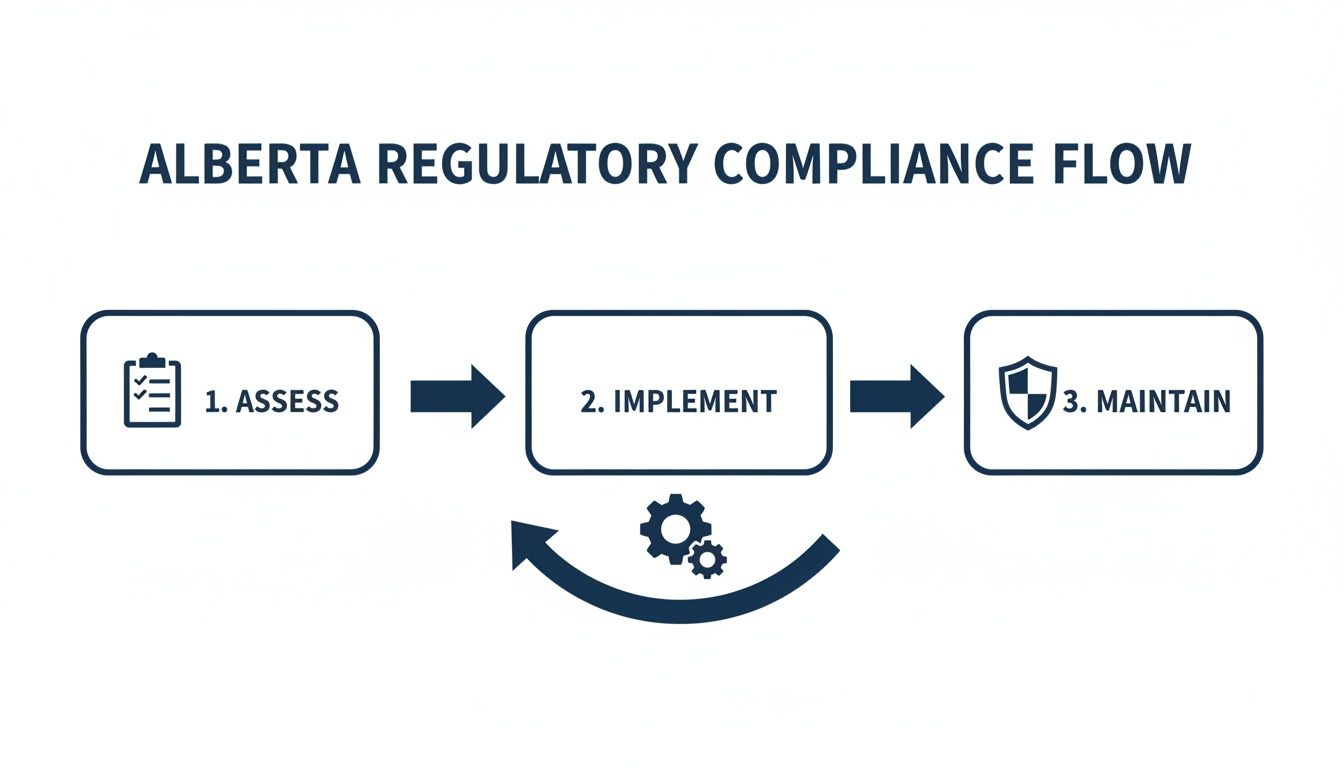
The key takeaway here is that compliance is not a one-time project. It’s a continuous cycle of assessing, implementing, and maintaining that demands ongoing expert management.
Consider your plumbing. A reactive plumber fixes an immediate leak but leaves the old, corroded pipes in place. A proactive one not only stops the leak but also inspects your entire system, identifies future risks, and suggests preventive maintenance to avoid a flood later. The same principle applies to cybersecurity.
Many businesses are stuck in the traditional "break-fix" IT model—calling for help only when something goes wrong. In today's threat landscape, that approach is dangerously outdated. A proactive partner uses round-the-clock monitoring and threat hunting to stop attacks before they cause damage, providing predictable IT spending and minimizing costly downtime.
A proactive security partner doesn't just sell you tools; they integrate into your business as a strategic advisor. Their goal is to align your technology with your business objectives, ensuring security enables growth instead of hindering it.
This shift in mindset is crucial as Edmonton's small and mid-sized businesses increasingly migrate to the cloud. This trend is driving +1.9% medium-term growth in the region as companies adopt Security-as-a-Service to fill expertise gaps. With SMEs representing a massive 12.88% CAGR growth vector through 2030, leveraging cloud-based security—which already holds a 62.2% market share—is essential for staying modern and resilient. To delve deeper into this, you can discover more insights about the Canadian cybersecurity market.
Any professional cybersecurity provider should have a clear, documented process for onboarding new clients to ensure a smooth transition with minimal disruption to your operations. For example, at CloudOrbis, we use a proven 10-step engagement model that covers everything from the initial assessment and strategic planning to implementation, employee training, and ongoing optimization. This methodical approach ensures no part of your IT environment is overlooked.
Finding a partner who can handle both high-level security strategy and day-to-day support is ideal. For more on this, check out our guide on the benefits of strategic IT consulting in Edmonton. By choosing a partner with a transparent process and a proactive mindset, you’re not just buying a service; you’re investing in a secure foundation that supports long-term growth and peace of mind.
World-class cybersecurity should not be a roadblock; it should be the engine that empowers your business to move forward with confidence. We have covered significant ground, from the specific threats targeting Edmonton businesses to the essential services that form a strong defence. The core idea is simple: proactive cybersecurity is not just an expense; it’s a strategic investment that fuels growth, protects your hard-earned reputation, and builds genuine trust with your customers.
When you have a dedicated team in your corner, you can finally stop firefighting IT issues. Your time and resources can shift back to what you do best—running your business. This is about more than just defence; it’s about giving your organization the freedom to operate without constantly looking over its shoulder.
For many medium-sized businesses, the cost and complexity of enterprise-grade security can feel out of reach. However, a managed services model changes the game. It brings the advanced tools and expert oversight of a large corporate security team to your doorstep for a predictable, SMB-friendly cost.
This approach is particularly critical in our local market. A partner who understands the unique Edmonton business landscape—from the specific compliance challenges in the oil and gas sector to the strict data protection rules in healthcare—provides support that fits your daily reality. That localized expertise ensures the cybersecurity services Edmonton businesses like yours receive are relevant, practical, and effective.
With a proactive security partner, you gain more than just technology; you gain peace of mind. You can pursue new opportunities, adopt new technologies, and scale your operations, knowing your digital foundation is solid.
The journey to a stronger security posture begins with a single, concrete action. The most successful businesses do not wait for a threat to materialize. They take a proactive stance, seeking to understand their weaknesses before an attacker has a chance to find them. That first step is often the most important one you can take.
A comprehensive security assessment is the ideal starting point. It provides a clear, unbiased view of your current security gaps and delivers a practical roadmap for improvement. This is not just a technical scan; it's a business-focused evaluation designed to align your security strategy with your growth goals.
Ready to stop worrying about the "what-ifs" and start building a more secure future? The team at CloudOrbis is here to help. We offer a no-obligation security assessment to help you understand your risks and map out a clear path forward.
Contact CloudOrbis today to schedule your complimentary security assessment and take the first step toward true peace of mind.
When exploring professional cybersecurity, Edmonton business leaders often ask the same practical questions. Getting clear, straightforward answers is the first step toward making a confident decision to protect your organization. Here are the most common queries we hear.
The answer to this common question lies in shifting away from the outdated, reactive "break-fix" model. With break-fix, costs are unpredictable and often escalate during an emergency. You end up paying a premium for last-minute fixes after something has already gone wrong.
In contrast, a managed services model provides a predictable, monthly operational expense. This approach bundles proactive monitoring, ongoing maintenance, and expert support into a flat fee. You gain enterprise-grade security and budget stability—a far more strategic investment than waiting for a costly disaster.
This is a dangerous misconception. Today's cybercriminals do not manually select targets; they use automated tools that constantly scan the internet for any vulnerability. These bots do not care if you have five employees or five thousand. They only care about finding an unpatched system, a weak password, or an employee who might click a malicious link.
Cyberattacks are often a numbers game. Attackers cast a wide net, and small businesses that believe they are "too small to matter" are frequently the easiest and most profitable targets because they lack robust defences.
In reality, your size does not offer protection—it can make you a more attractive target. For attackers, Edmonton SMBs often hold valuable data without the extensive security teams of larger corporations, making them ideal low-hanging fruit.
A common concern is that overhauling security will bring business operations to a halt. A professional provider of cybersecurity services in Edmonton will follow a structured onboarding process designed to minimize downtime and ensure a smooth transition.
A proven engagement process should be clear and transparent. For example, our own 10-step model guides you through every phase:
This methodical approach ensures your business is protected quickly and efficiently, without the operational headaches you might fear. The goal is to get your new defences up and running so you can return your focus to your business.
Ready to build a more secure and resilient future for your organization? CloudOrbis Inc. provides the proactive expertise and 24/7 Canada-based support your business needs to thrive.
Schedule your complimentary security assessment today and discover how we can help you achieve true peace of mind.

February 14, 2026
Protect Your Business with Network Security Edmonton: A Practical GuideDiscover network security Edmonton strategies to protect your business from cyber threats. Practical tips, expert insights, and proven defenses.
Read Full Post
February 13, 2026
Azure Migration Edmonton: An Expert Guide to a Seamless Cloud TransitionAzure migration Edmonton: Plan, secure, and optimize your cloud move with practical steps, cost control, and security best practices.
Read Full Post
February 12, 2026
SharePoint Migration in Edmonton: A Guide to a Seamless Cloud MoveDiscover SharePoint migration Edmonton best practices: plan, execute, and optimize your cloud transition for faster ROI and minimal disruption.
Read Full Post