
February 6, 2026
A Business Guide to IT Support EdmontonUnlock business growth with the right IT support Edmonton offers. Our guide covers services, costs, and choosing the best partner for your company's needs.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
December 23, 2025

Protecting the sensitive data flowing through your Alberta private career college isn't just an IT problem—it's a fundamental part of your promise to students. This is about safeguarding everything from Social Insurance Numbers and student loan details to academic transcripts and private health notes. Think of it less as a technical chore and more as a core pillar of your college's integrity and a non-negotiable legal duty.

For private career colleges in Alberta, managing student information has become a high-stakes responsibility. This goes far beyond simple administrative record-keeping. It's about upholding the digital trust students place in you the moment they apply. The information you collect—from their first inquiry to their post-graduation job search—is a valuable target for cybercriminals and a major focus for regulators.
It helps to see your college not just as a place of learning, but as a custodian of deeply personal life stories. Every student file contains a sensitive mix of academic ambitions, financial situations, and unique personal identifiers. Protecting this data is now as critical as delivering a first-rate education.
The challenge of protecting sensitive data in Alberta private career colleges is amplified by a unique set of pressures. Most institutions work with tight budgets and small IT teams, making it a struggle to keep up with a constantly evolving threat landscape. At the same time, the regulatory environment, led by Alberta's Personal Information Protection Act (PIPA), demands strict compliance with rules that can often feel abstract and overwhelming.
This guide cuts through the complexity to offer a practical roadmap for college administrators and IT leaders. We focus on the real-world challenges you face, zeroing in on:
Your approach to data protection should be treated as a core business function. It directly impacts your reputation, your ability to recruit students, and your standing with provincial regulators. A single data breach can erase years of hard-earned trust.
Our goal is to empower your leadership team with the clarity needed to build a data protection program that is not just compliant on paper, but genuinely resilient. The following sections provide the specific frameworks, checklists, and best practices to turn these principles into action.
Running a private career college in Alberta means you handle a mountain of sensitive student information every day. Understanding your legal obligations under the Personal Information Protection Act (PIPA) is not just about ticking a compliance box—it is about building and maintaining trust with your students.
Think of PIPA as the foundation of that trust. When a student enrolls, they are not just signing up for a course; they are entrusting you with personal details with the expectation that you will protect them. Your primary duty under PIPA is to honour that trust by safeguarding their data with the seriousness it deserves.
This is not an optional part of the job. For Alberta's private career colleges, meticulously managing sensitive student data is a core regulatory requirement. Government guidelines are specific, requiring you to maintain detailed files on everything from marks and transcripts to withdrawal forms and job placement records.
PIPA is not as complicated as it sounds. The entire law is built on a commonsense idea: reasonableness. This means your security measures must match the sensitivity of the data you are protecting. For instance, a student’s application for financial aid requires much stronger protection than a simple email address collected for a newsletter.
Let's break down the key ideas you need to know:
Under PIPA, accountability is non-negotiable. Even if you use a third-party cloud service to store student records, your college remains legally responsible for protecting that information. You cannot outsource your legal duty.
While PIPA is your local rulebook, you cannot ignore the federal Personal Information Protection and Electronic Documents Act (PIPEDA). PIPEDA usually applies whenever you transfer personal data across provincial or national borders for commercial reasons. So, if you enroll online students from B.C. or Ontario, you likely fall under PIPEDA's jurisdiction for their data.
The good news? PIPA is considered "substantially similar" to PIPEDA, so their main principles are very much aligned.
The most critical takeaway here is the non-negotiable need for Canadian data residency. Storing sensitive student information on servers outside of Canada opens your college to serious legal risks and privacy violations. You must have a contractual guarantee from any cloud provider or third-party vendor that all your student data will remain safely within Canada's borders. Getting these legal details right is a huge part of our specialized IT compliance services for Alberta private career colleges, where we help you navigate these complex requirements with confidence.
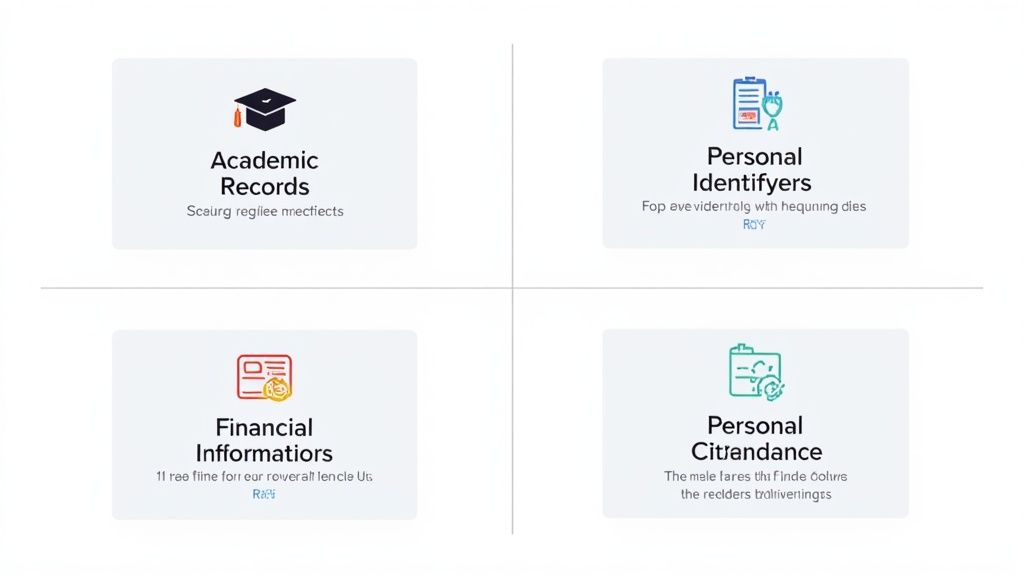
Strong data protection boils down to a simple truth: you cannot protect what you do not understand. For private career colleges in Alberta, this means getting specific about the "student information" you handle. Think of it like a library—you would not just dump all the books in one giant pile. You organize them by genre. The same logic applies to your data; it needs to be categorized based on its sensitivity.
This structured approach is the bedrock of any real security program. When you properly classify the sensitive data in Alberta private career colleges, you can match the right level of protection to the right information. It stops being a guessing game and becomes a clear, methodical strategy.
A great place to start is by sorting your student data into four main, risk-based buckets. This simple framework helps your team grasp not just what they are protecting, but why it is a major issue if that specific information is compromised.
Here are the core categories:
Think of your data inventory as a blueprint for your entire security strategy. Without knowing exactly where your most sensitive information lives, you are essentially trying to build a fortress in the dark.
This is not a one-time task. Classifying data needs to be part of your daily operations. Every new application form, system, or process you introduce should be viewed through this lens, so new data is categorized and protected from day one.
Once your data is sorted into categories, the next step is to link specific safeguards to each one. It's a simple equation: the more sensitive the data, the tougher the protection needs to be. This risk-based approach ensures you are using your time and budget where it counts the most.
For example, while all your data deserves basic protection, the security around Personal Identifiers must be far more stringent than for general academic records. That might mean using stronger encryption or enforcing stricter access controls for your most critical assets. Building a full strategy for your data's entire lifecycle is a complex but vital job. For a closer look at these concepts, our guide on effective data security management offers a deeper dive.
To make this easier for your team, the table below provides a clear, at-a-glance guide connecting data types to their risks and the safeguards needed.
This table breaks down the common types of student information, highlighting the risks involved and the kinds of security measures you should have in place.
Adopting this framework gives your college a repeatable, logical way to handle student data. You shift from being reactive to proactive, building a security posture that not only meets Alberta PIPA requirements but is genuinely resilient against today's threats.
Once you have mapped out the sensitive student data you are responsible for, the next step is to build a fortress around it. Strong data defence is not about buying a single piece of software or creating one rigid policy. It is about creating multiple layers of security.
Think of it like securing a physical building. You have locks on the doors, cameras in the hallways, and a reinforced room for your most valuable assets. Each layer works together, making it progressively harder for someone to break in.
This multi-layered approach is the heart of protecting sensitive data in Alberta private career colleges. It is a practical strategy that delivers serious protection without needing a massive, dedicated IT department. Let's break it down into three essential pillars: administrative, technical, and physical safeguards.
Your first and most critical layer of defence has nothing to do with technology. Administrative safeguards are the policies, procedures, and training that shape how your team interacts with data every day. They are all about creating a culture of security awareness.
Think of these safeguards as your human firewall. They turn your staff from a potential weak link into your strongest security asset.
A data handling policy is not just a document that sits on a shelf; it is a living guide that actively reduces the risk of human error—the leading cause of data breaches.
With your human firewall in place, it is time for the next layer: the technology you use to actively guard your systems and data. These are the digital locks and keys that enforce your security policies automatically. For colleges with limited IT staff, focusing on a few high-impact technical controls offers the best value.
Many small and mid-sized colleges discover that partnering with a specialized provider is the smartest way to implement and manage these tools. As we detail in our guide, expert IT support for private career colleges in Alberta ensures these systems are configured correctly for maximum protection.
Here are the technical must-haves:
Finally, do not forget about the physical world. Your digital data still lives on physical hardware, and those paper records can be a huge risk if they are not properly secured. Physical safeguards are often commonsense, but they are a vital piece of your overall defence.
Key physical security measures include:
By weaving these administrative, technical, and physical safeguards together, you create a tough, multi-layered security posture that effectively protects your students' trust and your college's reputation.
Your college runs on a web of third-party services. From cloud-based Student Information Systems to online payment processors, these partnerships are essential for modern operations. But they also create a significant blind spot. Every time student data leaves your direct control, your accountability under Alberta's PIPA does not.
You are always legally responsible for protecting that information, no matter whose servers it resides on. This simple fact makes vendor risk management a non-negotiable part of your data protection strategy. You can outsource a service, but you can never outsource your responsibility.
The most important moment in managing vendor risk is not when a problem occurs—it is before you ever sign a contract. Vetting a potential partner’s security and privacy practices is your first and most effective line of defence. A slick sales pitch is no substitute for hard evidence of strong security.
Before you commit, your due diligence checklist needs to cover the basics:
This vetting process ensures you only partner with organizations that take data protection as seriously as you must.
Your vendor agreements are more than just a formality; they are your primary tool for enforcing your security standards. Vague promises of "best practices" are not sufficient. Your contracts must contain explicit, legally binding clauses that hold vendors accountable for protecting your data.
A vendor contract should be a security document first and a commercial agreement second. It must clearly define the rules of engagement for how your sensitive student data will be handled, protected, and returned.
Here are the key clauses you must demand:
These contractual safeguards give your partners a legal and financial incentive to meet your security standards. This is especially critical for core systems, which is why our professional LMS support for Alberta private career colleges always places a heavy focus on vendor security from the outset. Building secure partnerships is the only way to expand your college’s capabilities without exposing it to unacceptable risk.
Realistically, even with the best security in place, a data breach is always a possibility. When an incident occurs, having a calm, methodical response plan is the difference between a managed crisis and a full-blown catastrophe. For private career colleges, this means having a clear, step-by-step playbook ready to go before you ever need it.
An effective breach response plan is not about assigning blame; it is about speed, control, and clear communication. Think of it as a roadmap that helps you protect your students, meet your legal duties under Alberta’s PIPA, and salvage the trust you have worked so hard to build.
This type of critical planning is more important than ever. Alberta's private career college sector has seen a massive surge, with enrolments jumping over 30% in the past five years. Amid this growth, Advanced Education has issued compliance orders to 15 institutions since June 2024, many related to inadequate record-keeping. This highlights the very real reputational and operational risks of mismanaging data.
A strong plan breaks down the chaos of a breach into four manageable stages. It is a sequence of actions designed to stop the immediate threat, assess the damage, notify the right people, and learn from the experience to become stronger.
Often, data incidents involve third-party vendors. Managing those relationships is a critical part of preventing breaches in the first place.
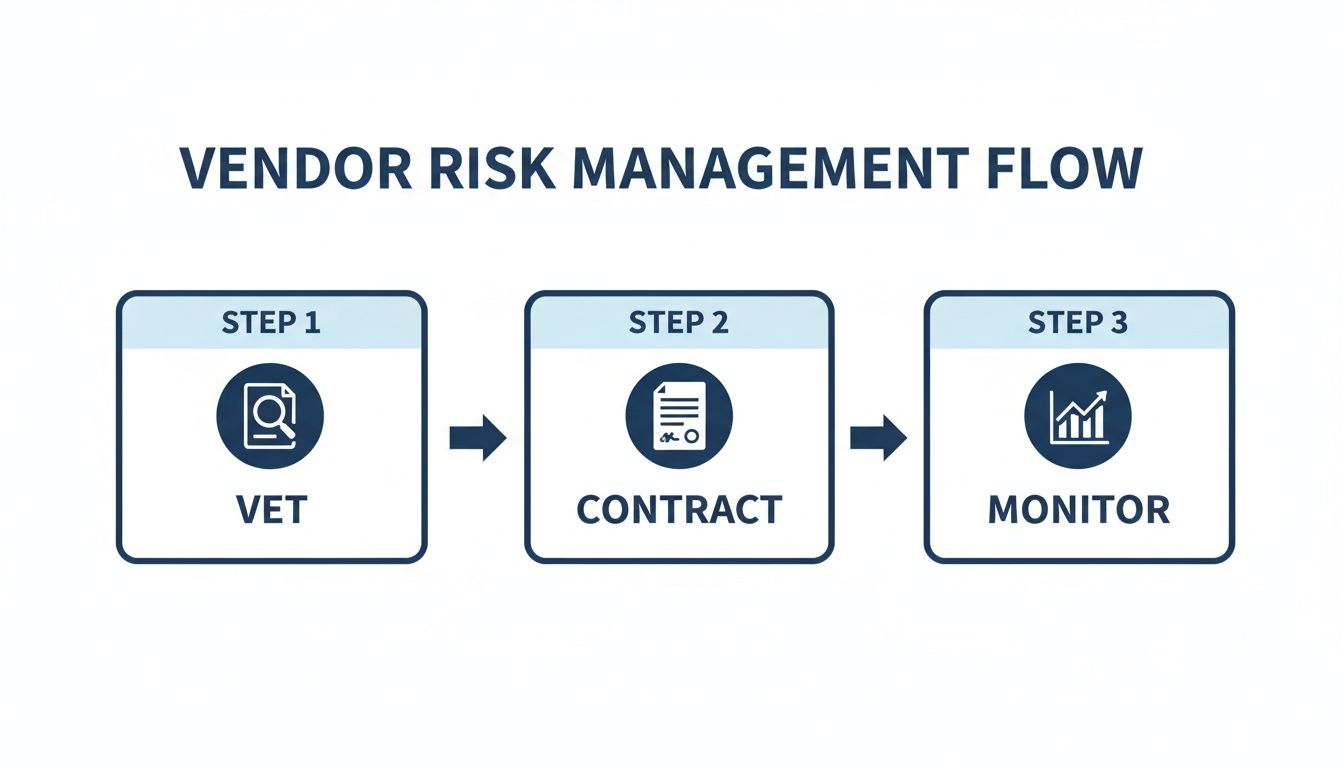
This simple workflow—vetting security, locking in terms, and ongoing monitoring—is your first line of defence against a breach originating from one of your partners.
Here are the four core stages of your internal response:
The notification stage can feel the most daunting. PIPA's "real risk of significant harm" threshold is a judgment call, but it is always better to err on the side of caution.
When in doubt, it is best practice to assume a risk of significant harm exists and proceed with notification. Transparency is key to maintaining trust with your students and meeting regulatory expectations.
Your notifications must be timely and crystal clear. They need to explain what happened, what information was involved, and what steps individuals can take to protect themselves, such as monitoring their financial accounts.
Having pre-drafted notification templates as part of your response plan can save critical time when the pressure is on. This entire plan is a key piece of a larger business continuity strategy. For a complete guide to get you started, check out our comprehensive disaster recovery plan template.
When it comes to the day-to-day realities of managing sensitive student data, practical questions arise frequently. Let's tackle some of the most common ones we hear from administrators at Alberta’s private career colleges.
In Alberta, you cannot keep student records indefinitely, nor can you shred them the day a student leaves. Provincial regulations have specific rules on how long you need to retain them after a student graduates or withdraws.
While the exact timeline can vary depending on the record type, your college absolutely needs a solid data retention policy. This is not just a suggestion—it is critical for compliance. Your policy should clearly outline these timeframes, which often span several years. Just as importantly, it needs a plan for securely and permanently destroying that data once its legal or business life is over. This is how you minimize your long-term risk.
If you are looking for the one action that provides the most value, it is this: mandatory, recurring staff training. While technology is essential, human error is still the weakest link and the leading cause of data breaches.
Think of it this way: you can have the best locks in the world, but they are useless if someone leaves the door unlocked. By training your team to spot phishing emails, adhere to data handling rules, and use security tools properly, you create a powerful human firewall. It is a surprisingly cost-effective way to drastically reduce your vulnerability to the most common attacks targeting schools.
A well-trained team that understands the why behind protecting student data is your single greatest security asset. Technology provides the tools, but your people provide the vigilance.
This is a major question, and the short answer is: you must be extremely careful. To remain compliant with Alberta’s PIPA and general privacy best practices, sensitive personal information must be stored and processed on servers physically located within Canada.
Many major US cloud providers—like AWS, Azure, and Google Cloud—do have Canadian data regions, but you cannot just assume you are using them. You must specifically configure your services to keep everything in-country. Crucially, your contract with the vendor must legally guarantee that your data will not be transferred, mirrored, or backed up to servers outside of Canada for any reason. This is not a "nice-to-have"; it is a non-negotiable part of your due diligence.
At CloudOrbis Inc., we specialize in building secure, compliant IT environments for educational institutions. Our team ensures your data stays protected and your operations run smoothly, so you can focus on student success. Learn how our managed IT services can safeguard your college.

February 6, 2026
A Business Guide to IT Support EdmontonUnlock business growth with the right IT support Edmonton offers. Our guide covers services, costs, and choosing the best partner for your company's needs.
Read Full Post
February 5, 2026
A Guide to Managed IT Services in Edmonton for Your BusinessDiscover how managed IT services Edmonton can secure your SMB. This guide covers costs, benefits, and how to choose the right IT partner for growth.
Read Full Post
February 4, 2026
Your Guide to Ransomware Protection in Edmonton: Protect Data & Ensure UptimeLearn how ransomware protection edmonton keeps your data secure with practical steps for local Edmonton businesses.
Read Full Post