
February 4, 2026
Your Guide to Ransomware Protection in Edmonton: Protect Data & Ensure UptimeLearn how ransomware protection edmonton keeps your data secure with practical steps for local Edmonton businesses.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
December 21, 2025

Specialized cybersecurity services for the Alberta oil & gas industry are no longer just a good idea—they are essential for safeguarding the province's economic engine. This isn't about standard IT security anymore. It’s about merging information technology (IT) defence with operational technology (OT) safety to protect everything from corporate networks to remote well sites, keeping operations running and assets secure.
Alberta's oil and gas sector is the backbone of the Canadian economy, but its growing reliance on interconnected digital systems creates serious vulnerabilities. Every component, from a remote sensor on a pipeline to the accounting software in a downtown Calgary office, is a potential doorway for a cyberattack. A single breach can set off a chain reaction with consequences that extend far beyond data loss.
Imagine a ransomware attack that doesn’t just encrypt your files but physically shuts down production at a processing plant. This isn’t a far-fetched scenario; it's a real and growing risk. Such an incident can lead to massive financial losses, environmental hazards, and devastating reputational damage. The stakes are incredibly high, involving not just business continuity but also worker safety and the security of our province's energy supply.
The regulatory landscape is also tightening. With the new Security Management for Critical Infrastructure Regulation, the Alberta Energy Regulator (AER) now requires designated critical facilities to comply with the CSA Z246.1 standard. This rule mandates a formal security management program that covers both physical and digital threats.
This new reality places significant responsibility on business and IT leaders. Under this standard, organizations are now expected to manage key requirements like:
For many organizations, meeting these standards represents a fundamental shift. A basic firewall and antivirus software are no longer enough. A proactive, multi-layered defence is now a regulatory necessity.
This guide cuts through the technical jargon to provide a clear roadmap for building that defence. We will walk through the specific threats targeting your operations and break down the essential cybersecurity services for the Alberta oil & gas industry needed to build a resilient and compliant security posture.
For a closer look at our industry-specific solutions, you can explore CloudOrbis’s dedicated services for the oil and gas sector.
To build an effective defence, you must first understand what you're up against. For Alberta's oil and gas sector, the threat isn't a single, easily identifiable enemy. It’s a complex and shifting landscape of interconnected risks that touch every stage of your operations.
Think of your entire operation—from upstream extraction to downstream refining—as a massive, interconnected system. A single weak point, representing one digital vulnerability, can threaten the integrity of the entire system. This isn't just about protecting data; it's about safeguarding physical processes, worker safety, and operational uptime.
The biggest challenge today is the convergence of Information Technology (IT) and Operational Technology (OT). Your IT systems—email servers, corporate networks, and financial software—are now directly linked to your OT systems, which include the industrial control systems (ICS) and SCADA networks that manage pumps, valves, and drills.
This connection drives huge efficiencies but also creates a dangerous new pathway for attackers. A seemingly harmless phishing email that tricks an employee in the head office could become the launchpad for an attack that pivots into the OT network, giving a threat actor direct control over physical machinery.
For instance, an attacker could manipulate sensors to provide false readings, disable critical safety alarms, or even shut down a pipeline. The consequences go beyond financial loss, creating the potential for environmental disasters and serious safety incidents. This is where the need for specialized cybersecurity services for the Alberta oil & gas industry becomes crystal clear.
The upstream sector, with its remote and often unmanned well sites, is a particularly tempting target. As a CyberAlberta report highlights, these sites in Alberta's sprawling energy landscape are highly susceptible to both physical and digital intrusions. Weaker network connections and unsecured systems in the field allow attackers to infiltrate critical OT from a distance. The problem is compounded by legacy systems that are difficult to patch, creating easy pathways for attacks to jump from IT to OT. You can see more of the findings from CyberAlberta in their full report.
These isolated assets often rely on less secure communication channels, making them easier to compromise. An attack here could disrupt extraction, manipulate production data, or serve as a quiet entry point to the wider corporate network. For a deeper look at different attack types, check out our guide on what constitutes a cybersecurity threat.
As we move to midstream (transportation and storage) and downstream (refining and distribution), the threats evolve but remain just as critical. The systems managing pipelines, storage facilities, and refineries are highly automated and deeply interconnected.
Common attack vectors in these areas include:
The same interconnectivity that drives modern efficiency is also the industry's greatest vulnerability. An attack on one part of the value chain can create a cascading failure that impacts every other stage of your operation.
To truly get a handle on this unique threat landscape, organizations can benefit from a comprehensive risk management framework like ISO 31000. This structured approach helps you systematically identify, assess, and treat risks, creating a solid foundation for a security posture that works. Acknowledging these specific threats allows business and IT leaders to move beyond generic security tools and invest in targeted strategies that protect their most critical assets.
Knowing the unique threats facing Alberta’s oil and gas sector is one thing; building a defence against them is another. Now, we shift from the problem to the solution: strategically selecting the right cybersecurity services to guard the critical intersection of your IT and OT environments. A generic, one-size-fits-all approach is a recipe for disaster when operational continuity and physical safety are on the line.
Instead, you need a multi-layered defence. Think of it like securing a critical production facility. You wouldn't rely on just a strong front gate. You’d have perimeter fences, 24/7 surveillance, strict access controls, and a rapid response team. In the digital realm, each of these roles is handled by a specific cybersecurity service, all working together to create a truly resilient security posture.
The services below are the foundational building blocks for protecting your operations. They each play a distinct, yet complementary, role in building a formidable defence against the threats targeting Alberta's energy producers.
Let's break down how each of these services contributes to your overall defence.
One of the most powerful tools in your arsenal is Managed Detection and Response (MDR). Imagine having a dedicated team of elite security analysts watching over your network 24/7/365, actively hunting for threats that automated tools might miss. That’s what MDR delivers.
This service goes beyond simply sending alerts. MDR teams use advanced threat intelligence and sophisticated analytics to spot suspicious behaviour, investigate potential incidents, and then provide a clear, guided response to contain and shut down threats before they cause real damage. For an industry where downtime is measured in millions of dollars per day, that proactive vigilance is non-negotiable.
While MDR is your 24/7 security patrol, Vulnerability Management is your proactive maintenance crew. It’s the disciplined process of systematically identifying, evaluating, and fixing weaknesses in your software, hardware, and network configurations. An unpatched server or a misconfigured firewall is like an unlocked window—an open invitation for an attacker.
A continuous vulnerability management program isn't a one-time project. It's an ongoing cycle:
This disciplined process hardens your defences from the inside out and dramatically shrinks your attack surface.
Protecting your corporate IT network is one challenge, but securing your operational technology (OT) is a completely different ball game. Specialized OT/ICS Security Monitoring is designed to understand the unique protocols and behaviours of industrial environments. These systems can spot unusual activity that could signal an attempt to manipulate a physical process—something a standard IT security tool would almost certainly miss.
By monitoring the specific language of your industrial equipment, you can identify threats that aim to disrupt production, compromise safety systems, or cause physical damage. This is a critical layer of defence for any modern energy operation.
The reality is, cybercrime is a severe threat to Calgary businesses, especially those in Alberta's extensive oil and gas supply chain. National data paints a grim picture: a recent survey found only 47% of Canadian SMEs feel ready for a cyberattack, while 53% had already been hit. With so much exposure through third-party vendors in Calgary, any weak link can trigger a major disruption. You can discover more insights on the state of cybercrime in Calgary to better understand the local risk landscape.
As you add more security tools, the volume of data and alerts they produce can become overwhelming. A Security Information and Event Management (SIEM) solution acts as the central nervous system for your entire security operation. It pulls in, aggregates, and analyzes log data from across your IT and OT infrastructure—from firewalls and servers to specialized ICS sensors.
This single, centralized view allows security analysts to connect the dots between events from different sources, identify patterns that indicate a sophisticated attack, and streamline incident investigations. A well-managed SIEM turns a chaotic flood of raw data into actionable intelligence, empowering faster and more effective threat response. If you're looking to understand the broader landscape of security tools, our guide on a wide range of cybersecurity services offers additional context.
Finally, every device connected to your network—from an engineer's laptop in the field to a server running a critical SCADA application—is an endpoint. And every endpoint is a potential entry point for an attack. Endpoint Detection and Response (EDR) provides advanced, next-generation protection for these devices.
Unlike traditional antivirus software that only looks for known malware signatures, EDR monitors endpoint behaviour in real-time. It can spot and block advanced threats like fileless malware and zero-day exploits, giving you deep visibility into how an attack is unfolding and the tools to immediately isolate a compromised device to stop an attacker in their tracks. Each of these cybersecurity services for the Alberta oil & gas industry plays a distinct but essential role in building a defence that’s up to the challenge.
Selecting a cybersecurity partner is like choosing the right drilling technology. It's not just about buying a new tool; it’s about finding a service model that fits your company's needs, budget, and existing team. Getting this decision wrong can lead to wasted money, security gaps, and a false sense of security.
To simplify, think of it like a major construction project. Are you hiring a general contractor to run the whole show, or will you work alongside specialized subcontractors? Maybe you just need an architect to provide the blueprints. Each approach can work, but only one is the right fit for your operation.
Making this call is the first step in implementing effective cybersecurity services for the Alberta oil & gas industry. This decision path can help you start thinking about where you land.
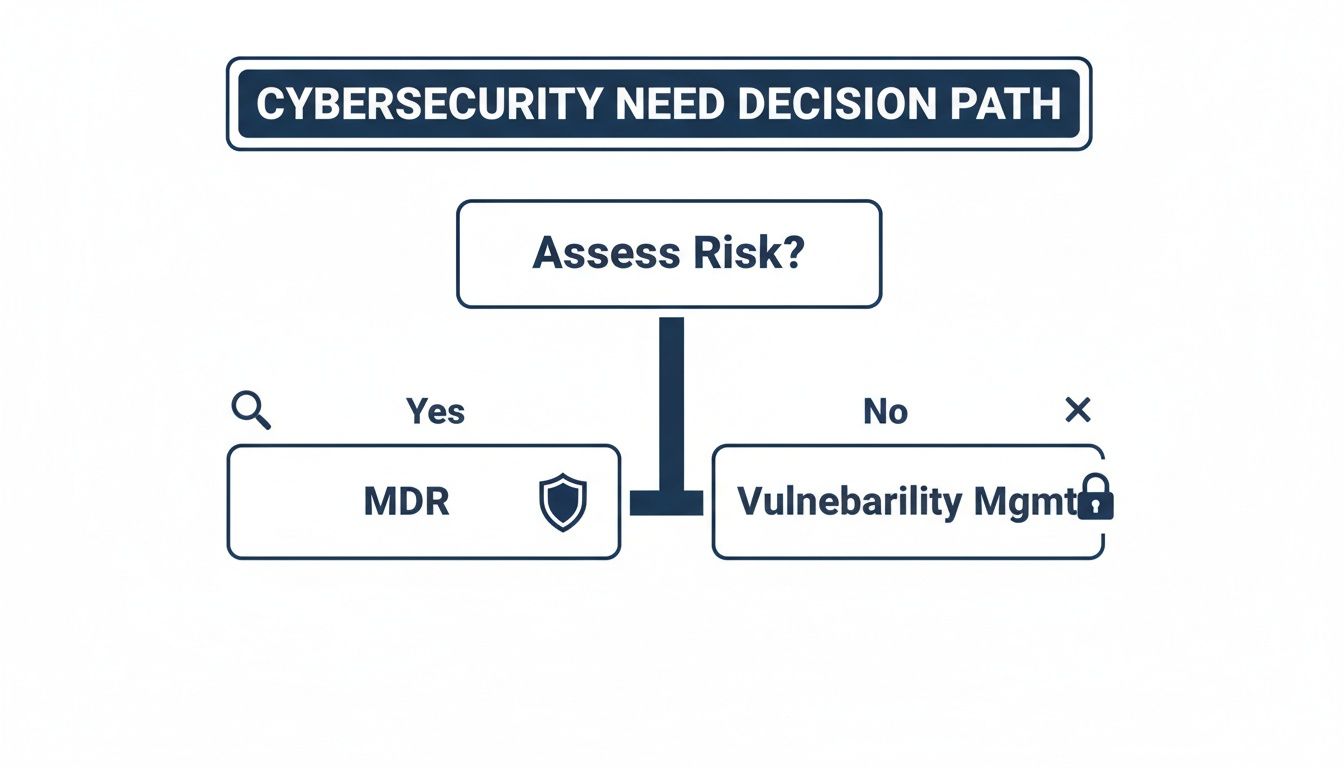
As you can see, everything starts with a clear assessment of your risk. That single step points you toward the right services, whether that's advanced threat detection or simply getting a handle on your vulnerabilities.
To help you decide, we've broken down the most common service delivery models.
This table offers a straightforward comparison of common service models. Use it to quickly gauge which approach best aligns with your company's operational needs, budget, and internal resources.
Choosing the right model is a strategic decision that will shape your company's resilience for years to come. Let's explore what each of these looks like in practice.
The fully Managed Security Services Provider (MSSP) model is your "general contractor." You essentially outsource your entire security operation to a dedicated third-party expert. This is the go-to solution for companies that lack a large internal security team or the specialized skills needed to defend a complex IT/OT environment.
An MSSP takes the reins, handling 24/7 monitoring, threat hunting, incident response, and compliance. They bring the people, processes, and technology, which frees up your internal IT team to focus on projects that drive the business forward instead of constantly putting out security fires. For many in the oil and gas sector, it’s the most direct route to a mature security posture.
What if you have a capable IT team that's stretched thin? Or perhaps they need backup to handle specific, time-consuming security tasks. This is where the co-managed model fits in. Think of this as bringing in specialized subcontractors to work alongside your crew. It’s a true partnership.
In a co-managed setup, your team might manage day-to-day IT support while the provider handles 24/7 threat monitoring and complex incident response. This approach offers the best of both worlds: you retain institutional knowledge and direct control while gaining access to top-tier expertise and security tools you could never justify purchasing yourself.
The co-managed model acts as a force multiplier for your existing team. It backs them with enterprise-grade tools and a dedicated team of security analysts, making it one of the most cost-effective ways to scale your security capabilities.
The Virtual Chief Information Security Officer (vCISO) model is like hiring the architect. This isn’t about day-to-day monitoring; it’s a high-level advisory service for organizations that need expert guidance on strategy, risk, and compliance but can’t afford—or don't need—a full-time, in-house CISO.
A vCISO partners with your leadership team to:
This model ensures your security initiatives are directly tied to business goals, guaranteeing every dollar you invest is strategic and defensible. To get a better sense of what a provider can offer, you can learn more about how MSSP security services build stronger defences. Settling on the right model is the foundation for a truly resilient security program.
Choosing a cybersecurity partner is one of the most important investments you can make. This isn’t about buying a piece of software; it’s about forming a strategic partnership to protect your most critical assets. A methodical, phased approach ensures you select a provider who not only has the right technical capabilities but also understands the unique operational realities of Alberta's energy sector.
Following this process helps you avoid costly missteps and guarantees your investment delivers real, measurable protection for both your IT and OT environments. By breaking the journey into clear phases—Assessment, Selection, Implementation, and Optimization—you can move forward with confidence.
Before you speak with vendors, you need to look inward. The first step is a thorough assessment of your own environment to determine what you need to protect and where your biggest weaknesses are. This is the foundation for everything that follows.
Think of it as surveying the land before building a fortress. You have to map the terrain, identify high-value assets, and pinpoint weak spots in your current perimeter.
This discovery process should answer a few key questions:
This self-assessment gives you the essential checklist you'll use to evaluate potential partners, ensuring you choose a provider whose capabilities align with your actual needs.
With a clear picture of your requirements, you can start the selection process. The goal is to find a provider offering more than just generic cybersecurity services for the Alberta oil & gas industry. You need a partner with proven, hands-on experience in industrial environments.
When evaluating potential partners, prioritize those with demonstrable expertise in both IT security and OT safety. A provider who only understands corporate networks will be dangerously out of their depth when it comes to protecting industrial control systems.
Key criteria to evaluate should include:
This vetting process ensures you end up with a team that speaks your language and truly understands the high stakes of your operations. Our guide to choosing the right cyber security service offers a more detailed list of questions to ask potential vendors.
Once you’ve selected your partner, the next step is a carefully planned and methodical implementation. A "big bang" approach, where everything is switched on at once, is a recipe for operational disruption. The rollout should be a phased process designed to minimize any impact on your day-to-day operations.
A typical implementation plan starts with your most critical systems first, then gradually expands coverage across your entire environment. This allows for a smoother transition and gives your team time to adapt to new processes and technologies. Clear, constant communication from your new partner is vital during this stage to keep everyone aligned.
Cybersecurity isn’t a "set it and forget it" project. The final phase is a continuous cycle of monitoring, reporting, and optimization. Your chosen partner should work with you to track key performance indicators (KPIs) and provide regular, easy-to-understand reports that demonstrate the value of their services.
Alberta's cybersecurity market is growing fast, driven by the energy sector's urgent need to protect its critical infrastructure. The Canadian market for cybersecurity solutions recently hit US$4.0 billion and is projected to climb to US$10.3 billion by 2034. Alberta is at the forefront of this trend, with companies rightly investing heavily in OT security and supply chain protection. To read the full analysis of this market growth, you can explore recent industry findings.
This ongoing partnership ensures your defences evolve alongside the threat landscape, keeping your operations resilient for the long term.
Securing Alberta's oil and gas operations is no longer just an IT task—it's a core business strategy. The reality is that operational continuity, worker safety, and the economic stability of our province depend on it. Protecting deeply interconnected IT and OT systems from sophisticated threats is now a foundational requirement for any energy company looking to stay ahead.
Throughout this guide, we’ve walked through the distinct threats targeting the sector, laid out essential defences, and provided a clear roadmap for finding the right security partner.
The most critical step is to move from awareness to action. Investing in the right cybersecurity services for the Alberta oil & gas industry is a direct investment in resilience, ensuring your operations can withstand whatever comes next. The time to build a robust, proactive defence is now, long before a minor vulnerability spirals into a major operational crisis.
A strong security posture is more than a shield; it's a competitive advantage that protects your assets, reputation, and future growth. It demonstrates a commitment to operational excellence and stakeholder trust in an increasingly connected world.
Don't wait for an incident to force your hand. Take the next step by scheduling a no-obligation consultation with our team.
When it comes to cybersecurity in Alberta’s energy sector, we know business and IT leaders have a lot on their minds. Let’s address some of the most common questions we hear.
The connection point where your corporate IT network meets your operational technology (OT) network is the real danger zone. An attack that starts with a simple phishing email on a business laptop can quickly pivot to your OT side.
Once an attacker is in your OT network, they can disrupt physical processes, shut down production, or even manipulate safety systems. We’re seeing a rise in ransomware specifically built to target industrial control systems (ICS), which moves the threat from data theft to real-world damage.
Your internal IT team knows your business inside and out, which is invaluable. However, securing both IT and OT environments requires a very specific and rare skillset. The reality is, 24/7 threat monitoring is a massive undertaking that can easily burn out even the most dedicated internal team.
This is where a co-managed or fully managed service model makes sense. You get round-the-clock access to seasoned experts and advanced security tools without the massive overhead of building an in-house security operations centre. It frees up your team to focus on what they do best—driving the business forward.
This is a critical concern. Many breaches don’t come through the front door; they sneak in through a compromised vendor or partner who has access to your systems. Effective third-party risk management is non-negotiable.
Protecting your supply chain isn't just about trust. It demands a structured process of verification and continuous oversight.
To address this risk, you need to:
A solid cybersecurity service for the Alberta oil & gas industry will always include supply chain security assessments to find and address these dangerous backdoors.
No, not even close. Meeting regulatory standards like CSA Z246.1 is a critical foundation, but it’s the bare minimum. Think of it as the starting line, not the finish line. Regulations are always playing catch-up with the latest threats, so a compliance-only mindset will leave you exposed.
A truly resilient security posture goes far beyond checking boxes. It involves proactively hunting for threats, continuously monitoring your environment, and having a rapid response plan that’s tailored to the specific risks your operation faces every day.
Ready to build a cybersecurity strategy that moves beyond compliance to create true operational resilience? Contact CloudOrbis today for a no-obligation consultation to assess your unique security posture and develop a roadmap tailored to your needs. Learn more at https://cloudorbis.com.

February 4, 2026
Your Guide to Ransomware Protection in Edmonton: Protect Data & Ensure UptimeLearn how ransomware protection edmonton keeps your data secure with practical steps for local Edmonton businesses.
Read Full Post
February 3, 2026
Proactive IT Maintenance Calgary: Prevent Downtime and Secure Your BusinessUnlock uptime with proactive it maintenance calgary, delivering secure IT systems and practical strategies for Calgary businesses.
Read Full Post
February 2, 2026
A Guide to IT Compliance for the Alberta Oil & Gas IndustryMaster it compliance for alberta oil & gas industry with a practical, click-ready guide on AER/TIER, cybersecurity controls, and audit readiness.
Read Full Post