February 15, 2026
Managed IT Services Calgary: A Guide for Growing BusinessesExplore managed it services calgary to boost security, streamline operations, and grow with predictable costs for SMBs.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
January 1, 2026

A cybersecurity services company is a team of specialized experts with the technology and knowledge to protect your business's digital assets from cyber threats. Think of them as a dedicated crew of digital bodyguards, security architects, and emergency responders for your company's data and systems.

Protecting your business today is like securing a fortress with countless digital doors and windows. Every employee device, cloud application, and network connection is a potential entry point for attackers. The threats are no longer simple viruses; they are sophisticated, constant attacks designed to steal data, disrupt your operations, and hold your business for ransom.
For Canadian businesses—especially in sensitive sectors like healthcare, manufacturing, and law—relying on off-the-shelf antivirus software is not enough. That’s like putting a standard padlock on a bank vault. You need a much more robust, active defence strategy to protect what truly matters.
A cybersecurity services company delivers that dedicated, expert defence. They are the architects who design your fortress walls, the guards who monitor for intruders 24/7, and the elite team that responds the moment a breach occurs. This partnership shifts your security from a passive checklist item to a dynamic, always-on defence posture.
This shift is crucial because modern cyber threats are relentless and automated, probing for weaknesses day and night. The question is no longer if an attack will happen, but when.
Partnering with a specialized firm isn't just an IT expense; it's a foundational business strategy for survival, compliance, and growth. It allows you to focus on your core operations with confidence, knowing your digital assets are professionally managed and protected.
The demand for these specialized services is skyrocketing across Canada. This trend is fuelled by more aggressive cyber threats and the widespread adoption of new technologies that expand a company’s attack surface. As businesses embrace the cloud and remote work, the need for expert security oversight has never been greater.
In fact, the Canadian cybersecurity solutions market is projected to nearly triple to USD 10.3 billion by 2034, a clear sign of its importance. This growth is particularly strong in Ontario, where a high concentration of financial, tech, and government organizations face heightened risks, making proactive security essential for their very survival. You can explore more on this market expansion from IMARC Group's detailed report.
For most medium-sized businesses, building an in-house security team with the same level of expertise is often financially impractical. A specialized cybersecurity services company gives you access to enterprise-grade tools and a team of seasoned professionals for a predictable, manageable cost.
This approach delivers several key benefits:
By understanding the top cybersecurity threats facing SMBs, you can better appreciate the value an expert partner brings to the table. They provide the peace of mind needed to operate securely in an increasingly connected world.
So, what does a modern cybersecurity services company actually do? In short, they provide the people, processes, and technology needed to build a proactive defence for your business. This is a world away from the old "set it and forget it" mindset of just installing antivirus software and hoping for the best.
A true cybersecurity partner brings a toolkit of interconnected services to the table. Each plays a specific role, but they all work together to create layers of security that can adapt to new threats. Let's break down the core services you should expect.
Think of this as your company’s digital watchtower, staffed by expert guards who never sleep. Managed Detection and Response (MDR) services use sophisticated tools to monitor your network activity around the clock, actively hunting for anything that looks out of place.
When a potential threat appears—like a login attempt from an unusual location in the middle of the night—the security team investigates it immediately. If it’s a real threat, they move quickly to contain and shut it down before it can cause real damage. This constant vigilance is critical, especially since many attacks happen outside regular business hours.
A vulnerability assessment is like hiring a professional inspector to check your building's security. They systematically scan your entire IT environment—servers, laptops, software, and network gear—to find known security flaws that an attacker could use to get inside.
The goal is to find these weaknesses before a cybercriminal does. Once a vulnerability is identified, your cybersecurity partner will help you prioritize the fix, essentially locking the doors that attackers were hoping to use. Performing these checks regularly ensures your defences stay strong as your systems change and new threats emerge.
A proactive security posture isn't about reaching a single moment of perfect security. It’s about consistently finding and fixing risks to stay one step ahead of the attackers.
Every device connected to your network—whether it’s a laptop, server, or smartphone—is an "endpoint." And each one is a potential doorway for an attack. Advanced Endpoint Protection goes far beyond traditional antivirus, using modern techniques to stop complex threats like malware and ransomware in their tracks.
It offers real-time protection and can even automatically isolate an infected device from the rest of the network, stopping a threat from spreading. In today's world of remote work and bring-your-own-device policies, securing every endpoint is a non-negotiable part of any solid security strategy. This is a core pillar of effective security managed services.
For any business in a regulated industry like healthcare (PHIPA), finance, or law, compliance isn't just a good idea—it's the law. Failing to meet these standards can lead to massive fines and a serious blow to your reputation.
A good cybersecurity partner knows these complex rules inside and out. They help you put the right security controls in place, generate the reports you need for audits, and ensure your data handling practices meet standards like PIPEDA. This expertise is crucial for achieving complete cybersecurity framework compliance and can turn a major headache into a competitive advantage.
To make sense of how these services fit together, here’s a quick breakdown of what they do and why they matter for your business.
Ultimately, these services work in concert to create a robust security posture that protects your operations, data, and reputation from the ground up.
For a medium-sized business, partnering with a cybersecurity services company is a game-changing strategic move that goes well beyond just IT. It’s a decision that directly supports your bottom line, streamlines your operations, and clears the path for growth. Too many organizations are stuck in a constant state of reactive "firefighting," a model that is as expensive as it is disruptive.
When you engage an expert partner, you fundamentally flip that script. Instead of scrambling to contain the damage after a breach, you shift to a proactive defence where threats are identified and neutralized before they can cause chaos. It’s the difference between dealing with a flood and fixing a leaky pipe.
One of the biggest benefits for any medium-sized business is gaining access to expertise and technology that would otherwise be out of reach. Consider what it would take to build an in-house security team with 24/7 coverage and specialists in threat hunting, compliance, and incident response. It’s a massive undertaking.
The cost of salaries alone, not to mention advanced security software and constant training, can easily run into hundreds of thousands of dollars a year. A partnership with a cybersecurity services company bundles all of that into a predictable, manageable monthly fee, giving you a much better return on your investment.
When you outsource your security, you're not just buying a service. You're bringing on a seasoned team of specialists whose entire job is to protect businesses just like yours from threats that never sleep.
This model is a great equalizer. It allows medium-sized companies to deploy the same calibre of defences that were once only available to large enterprises.
Navigating the tangled web of regulatory compliance is a major challenge, especially if you operate in healthcare (PHIPA), finance, or law (PIPEDA). These aren’t just suggestions; they carry the full force of law, with steep penalties for non-compliance. One misstep can lead to crippling fines and completely shatter your clients' trust.
A good cybersecurity partner acts as your compliance guide. They already know the specific rules for your industry and can implement the right technical controls and processes to ensure you meet all requirements.
They’ll help you with things like:
This expertise turns a serious business risk into a powerful selling point. It shows your clients you take protecting their data seriously, which can set you miles apart from the competition.
Every hour your leadership team spends putting out IT fires is an hour they’re not spending on growing the business. A security breach can derail your strategic plans for months, pulling everyone’s focus away from innovation, customer service, and finding new markets. Handing that responsibility over to a dedicated cybersecurity services company lifts that entire burden.
This partnership gives you the peace of mind that comes from knowing your digital operations are secure, allowing you to get back to what you do best. It creates a solid foundation where you can confidently adopt new technology and pursue growth opportunities without constantly looking over your shoulder.
The Canadian cybersecurity industry is well-equipped to meet this need. A remarkable 89% of cybersecurity companies in Canada are small-to-medium enterprises (SMEs) themselves. This means you have a vibrant market full of specialized partners who genuinely understand the challenges you face because they are in the same position. To get a better feel for this unique market, you can explore the full Canadian cybersecurity industry report.
Choosing a partner to handle your cybersecurity is one of the most important decisions you’ll make for your business. This isn't just about buying software or hardware; you're trusting a company with your data, your operations, and your reputation. The goal is to find a provider who acts like a true extension of your team, not just another expense.
The right partner understands your business, knows the specific threats in your industry, and is completely transparent. The wrong one can leave you exposed with a false sense of security, surprise costs, and gaps in your defences. To get it right, you need to ask the right questions and know exactly what to look for.
Before you consider signing a contract, you need to do a deep dive into a provider's processes, their team's expertise, and their commitments. Vague answers are a major red flag. A truly capable cybersecurity services company will welcome detailed questions and have direct, confident answers.
Start with their technical capabilities. Ask about the specific certifications their technicians hold, like CompTIA Security+, CISSP, or others relevant to the tools they use. This verifies you're getting actual experts, not just general IT support. It’s also critical they understand industry-specific regulations, like those detailed in a HIPAA compliance checklist for healthcare.
Next, talk about what happens when things go wrong. Because eventually, they will. The middle of a ransomware attack is the absolute worst time to figure out your partner's incident response plan.
Your questions should be pointed and specific:
The Service Level Agreement (SLA) is the most important part of your contract. This document legally defines the provider’s promises on service availability, response times, and performance. Don’t just skim it. A solid SLA is your protection if they don't deliver.
You are looking for specific, measurable commitments. For example, an SLA should clearly promise 99.9% uptime for managed firewalls or a guaranteed one-hour response time for high-priority security tickets. If the language is vague, demand clarity before you sign.
A provider's willingness to commit to a detailed and transparent SLA is a strong indicator of their confidence in their own services. Avoid any company that is hesitant to put its promises in writing.
Pricing models for a cybersecurity services company can also vary. Here are the most common structures you'll see:
The goal is to find a model that gives you complete protection without making you pay for services you’ll never use. A good partner will help you find that sweet spot for your budget and risk level. For more detail, our guide on MSSP security services breaks this down even further.
When you’re talking to multiple vendors, it’s easy for the details to blur together. Use a consistent checklist to compare them and ensure you don't miss anything important. Any provider worth considering will appreciate your diligence.
Here’s a simple framework to guide your conversations and help you find the best partner for your business.
Cybersecurity Partner Evaluation Checklist
Using a structured approach like this moves the conversation beyond a sales pitch and helps you find a partner truly invested in your security.
Theory and checklists are important, but seeing how cybersecurity works in the real world makes it all click. To really understand what a cybersecurity services company does, let’s look at a few practical examples from key Canadian industries. Each sector has its own unique threats and regulatory challenges, meaning a one-size-fits-all approach is not effective.
These mini-case studies show how the right security services solve specific business problems, ensuring everything from patient privacy to production lines stays safe. The results are tangible: operations run smoothly, compliance is solid, and client trust remains intact.
A medium-sized healthcare clinic in Ontario was juggling two major risks. They stored a mountain of sensitive electronic health records, making them a prime target for ransomware gangs. At the same time, they had to stay compliant with Ontario's Personal Health Information Protection Act (PHIPA), where a single mistake could mean crippling fines and a shattered reputation.
Their main challenge was securing all that data without slowing down the fast-paced workflow that doctors and nurses depended on every minute.
The solution was a multi-layered security strategy that covered all the bases:
The outcome was a secure and fully compliant environment. The clinic could finally assure patients their data was protected, meet all its PHIPA obligations, and get back to focusing on patient care without the constant fear of a cyberattack.
For organizations handling sensitive data, proactive defence is non-negotiable. It transforms cybersecurity from a source of anxiety into a pillar of operational strength and patient confidence.
For a manufacturing plant in Alberta, the biggest worry wasn’t just data theft—it was a full-blown operational shutdown. Their entire facility ran on a network of interconnected operational technology (OT) systems that managed the production line. An attack on those systems could halt production for days, leading to huge financial losses and supply chain chaos.
Their unique problem was protecting both their standard IT network and the specialized OT equipment on the factory floor, which often cannot be secured with off-the-shelf tools.
A specialized cybersecurity services company implemented a strategy focused on network segmentation and industrial control system (ICS) security. They essentially built a digital wall between the corporate IT network and the sensitive OT network. This meant that even if the IT side was compromised, the infection could not jump over to the critical machinery. This approach is fundamental to the robust cybersecurity services Edmonton businesses in industrial sectors require.
The result was a much more resilient operation. The plant could continue to modernize and connect more equipment to the network for better efficiency, all while knowing its core production processes were shielded from cyber threats.
A busy law firm in Toronto handles some of the most confidential information imaginable—case strategies, client financial records, and privileged communications. For them, a data breach would be catastrophic, not just financially, but for their reputation. Client confidentiality is the absolute bedrock of their business.
The challenge was securing data spread across laptops, cloud storage, and mobile devices, all while allowing lawyers to work efficiently from anywhere, at any time.
The solution focused on tight access controls, data encryption, and ongoing employee security training. A zero-trust security model was put in place, which means every single request to access data was verified, no matter where it came from. All sensitive files were encrypted both at rest (on a server) and in transit (sent over email), making them unreadable to anyone without authorization.
This fortified defence ensured that client data remained confidential and secure. The firm could confidently uphold its duty to its clients, protect its hard-earned reputation, and use technology to collaborate without opening the door to unnecessary risk.
Choosing the right partner is about more than just services; it’s about finding a cybersecurity services company that feels like a true extension of your team. While many providers might offer similar tools, the CloudOrbis difference comes down to our hands-on approach, clear processes, and unwavering commitment to Canadian businesses.
We firmly believe that world-class security support should be local. That’s why our 100% Canada-based, 24/7 helpdesk is a cornerstone of our service. This setup ensures your sensitive data stays within Canada—satisfying data sovereignty requirements—while giving you direct access to local experts who understand the specific challenges your business faces.
A successful partnership thrives on clarity and transparency. We remove the guesswork with our proven 10-step engagement process. Think of it as a detailed roadmap that guides you from the initial assessment and strategy development all the way through to implementation, employee training, and ongoing fine-tuning. You’ll always know exactly where you stand and what’s coming next.
A partnership should empower your business, not complicate it. Our process is designed to deliver a stronger security posture with minimal disruption, allowing you to focus on your core objectives with confidence.
For the thousands of Canadian businesses built on Microsoft technologies, deep expertise isn't just a nice-to-have—it’s essential. Our team specializes in the Microsoft ecosystem, helping you secure your environment and get the most out of your investment in tools like Microsoft 365 and Azure. This specific focus ensures seamless integration and security controls that are optimized to work together perfectly.
We apply this expertise across diverse industries, as you can see in the process flow below.
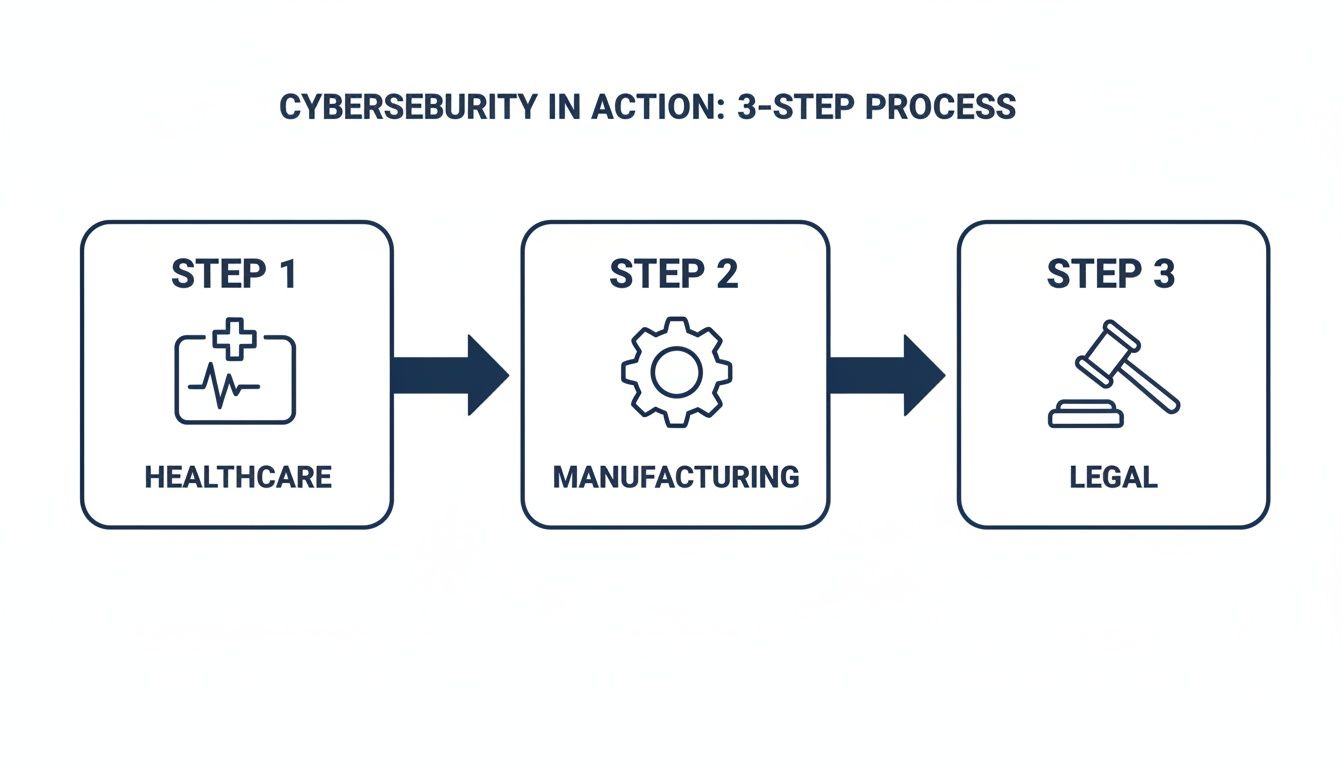
This visual highlights how a tailored security strategy is adapted to meet the unique compliance and operational needs of different sectors. Ultimately, our approach combines a local presence, a clear methodology, and specialized knowledge to deliver a security partnership you can genuinely trust. By taking a proactive stance, we help you build a resilient foundation for growth. For more on how we build this foundation, explore our approach to comprehensive cybersecurity risk management.
It’s smart to have questions when you’re looking for a partner to protect your business. Getting straight answers is the first step toward feeling confident in your decision. Here are a few of the most common questions business leaders ask when they're evaluating a cybersecurity services company.
Think of it this way: a Managed Services Provider (MSP) is like the general contractor for your entire IT infrastructure. They handle the plumbing, electricity, and general upkeep—everything from network maintenance to software updates—to keep things running smoothly day-to-day.
A dedicated cybersecurity services company, on the other hand, is the specialized security firm you hire to install alarm systems, patrol the premises, and respond to threats. While some MSPs, like CloudOrbis, have deep security expertise, a pure-play security firm focuses exclusively on threat hunting, incident response, and building advanced defensive walls.
The real difference comes down to depth. An MSP keeps the lights on; a security specialist keeps the intruders out.
There’s no single, one-size-fits-all number here, but a good rule of thumb is to set aside 10-15% of your total IT budget specifically for security. That figure can vary depending on your industry’s risk profile, any compliance regulations you must follow, and the amount of sensitive data you are protecting.
Instead of seeing it as another expense, think of it as an investment in business continuity. The cost of a proactive security partnership is almost always a small fraction of what it costs to clean up after a single major data breach.
Yes. Without a doubt. It’s a dangerous myth that small and medium-sized businesses are too small to attract a cybercriminal’s attention. In reality, attackers often see smaller companies as easier targets because they typically do not have the same heavy-duty defences as a large enterprise.
Cybercriminals don't pick their targets by hand. They use automated tools to constantly scan the internet for any weakness, and they don’t care if it belongs to a big corporation or a small shop. To them, your data is valuable, which makes every single business a potential target.
Protecting your business isn't just for large corporations anymore; it's a fundamental cost of doing business today.
Ready to build a stronger, more resilient security posture? The experts at CloudOrbis Inc. are here to help. Contact us today for a free consultation and discover how our proactive, Canada-based team can protect your business.

February 15, 2026
Managed IT Services Calgary: A Guide for Growing BusinessesExplore managed it services calgary to boost security, streamline operations, and grow with predictable costs for SMBs.
Read Full Post
February 14, 2026
Protect Your Business with Network Security Edmonton: A Practical GuideDiscover network security Edmonton strategies to protect your business from cyber threats. Practical tips, expert insights, and proven defenses.
Read Full Post
February 13, 2026
Azure Migration Edmonton: An Expert Guide to a Seamless Cloud TransitionAzure migration Edmonton: Plan, secure, and optimize your cloud move with practical steps, cost control, and security best practices.
Read Full Post