
February 8, 2026
A Strategic Guide to Outsourced IT in Edmonton for SMBsDiscover the real benefits of outsourced IT Edmonton. This guide helps local SMBs choose the right services, understand costs, and find a reliable partner.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
February 9, 2026

For any business leader in Edmonton, tackling cybersecurity means looking beyond generic headlines. It’s about understanding the specific digital threats aimed squarely at our local economy. While global cyber risks are important, the key is recognizing how those threats are tailored to target Edmonton's core industries—from energy and logistics to healthcare and manufacturing.
Edmonton's business community is diverse. The security needs of a ground-floor clinic are entirely different from those of a large manufacturing plant. A one-size-fits-all security plan simply doesn’t work here.
The reality is that cybercriminals are strategic. They customize their attacks to exploit the unique vulnerabilities and high-value data of specific sectors. This targeted approach makes it essential for Edmonton businesses to build a proactive, industry-aware security posture.
The threats impacting Edmonton are not abstract concepts; they are real dangers with serious consequences for our most vital industries. Understanding these specific risks is the first step toward building an effective defence.
In Alberta, and especially within Edmonton's vibrant business scene, cybersecurity threats have intensified. Ransomware attacks impacted a staggering 28% of Canadian organizations in 2024—a significant jump from 17% in 2021. This is not a distant problem; it is being felt sharply by small and medium-sized businesses right across our province.
These attacks rarely happen in isolation. They are often the final stage of a sophisticated phishing campaign. An employee receives an email that looks like a legitimate invoice, but one click is all it takes to compromise the entire network. While we focus on external threats, a clear understanding of insider threats is also critical, as not all risks originate from the outside.
The greatest vulnerability for many Edmonton businesses lies in the gap between knowing threats exist and understanding how they specifically target their operations. Closing this gap is the foundation of effective cybersecurity.
Moving from awareness to action is crucial. Once you recognize your industry is a target, you can implement focused security controls. For a broader perspective, our guide on the top cybersecurity threats for SMBs covers other common risks. It's about building a digital neighbourhood watch, where every business is alert, informed, and prepared to defend itself against the dangers at its doorstep.
For many business and IT leaders in Edmonton, "regulatory compliance" can seem like a dense legal maze. It’s easy to get lost in the jargon. But what if we thought about these rules differently?
Consider them less as obstacles and more as the building codes for your digital operations. Just as a physical structure must meet safety standards, your business must follow data protection laws to build a solid foundation of customer trust.
Ignoring these "digital building codes" is not just a legal gamble; it leaves vulnerabilities that cybercriminals are adept at finding. Compliance provides a clear blueprint for protecting sensitive information, which is fundamental to building a resilient business. This is about far more than just avoiding fines—it’s about demonstrating to your clients that you take their privacy seriously.
For businesses in Edmonton, a few key pieces of legislation form the backbone of data protection. Understanding what they are and what they require is the first step.
At the federal level, the primary law is the Personal Information Protection and Electronic Documents Act (PIPEDA). This act sets the ground rules for how private-sector organizations collect, use, and disclose personal information in the course of commercial activities.
However, Alberta has its own specific laws that often take precedence for local businesses.
Determining which laws apply to your specific business is critical. For a more detailed look, our guide on conducting a Privacy Impact Assessment in Alberta breaks down the local requirements further.
This is where legal requirements become practical business processes. It's about weaving data protection into the fabric of your daily operations.
For example, a local Edmonton law firm, to comply with PIPA and its professional obligations, must ensure every client email and case file is encrypted and stored securely. This means using secure email platforms, tightly controlling access to sensitive documents, and having a clear data retention policy.
Similarly, an Edmonton-based medical clinic must go beyond basic security to meet HIA standards. This involves training every staff member on patient confidentiality, implementing strict access controls on electronic health records, and having a documented, rehearsed plan for handling any potential data breach.
Compliance isn't a one-time project to be checked off a list. It's an ongoing commitment to protecting information. It fosters a culture of security that becomes a competitive advantage, signalling to clients and partners that you are a trustworthy custodian of their data.
Ultimately, navigating compliance for your cybersecurity in Edmonton is about building a fundamentally stronger, more reliable business. It ensures your data-handling practices are robust, defensible, and designed to protect your most valuable asset: your reputation.
For many Edmonton business leaders, the phrase "cybersecurity risk assessment" can sound intimidating. However, it’s not as complex as it seems.
Think of it like a safety inspection for your office. You wouldn't leave the back door unlocked or ignore a broken window. A risk assessment is the digital equivalent—checking your virtual locks, windows, and alarm systems to find weak spots before a breach occurs.
This process shifts your security posture from reactive to proactive. Instead of scrambling after an incident, you get ahead of the problem by identifying what needs protecting, what could realistically go wrong, and how to mitigate it. It is the most important first step you can take, providing a clear, prioritized action plan.
The goal isn't to find every single flaw at once. It's about building a solid understanding of your unique risks. That knowledge enables you to make informed decisions and allocate your security budget where it will make the most difference.
You cannot protect what you don’t know you have. The first stage is to take stock of your most valuable digital assets. Ask yourself: if this information were stolen, leaked, or destroyed, what would cause the most damage to my business?
Before you begin, it’s a good practice to establish strong IT asset management best practices to ensure you have a complete inventory of what you need to protect.
Start by listing your critical assets, which typically include:
Once you know what you’re protecting, the next step is to identify who or what might target those assets. Threats can be intentional or accidental, and they can originate from both inside and outside your organization. Consider what could realistically happen at your Edmonton company.
A common mistake is to only worry about sophisticated hackers in distant countries. The reality is that an untrained employee accidentally clicking a malicious link can cause just as much damage as a targeted ransomware attack. Both are serious threats that require a plan.
After listing potential threats, it's time to find the vulnerabilities—the weak spots that a threat could exploit.
Now it’s time to connect the dots. For each threat, determine the likelihood of it occurring and the potential impact it would cause. For example, the likelihood of an employee falling for a phishing email is probably high, and the impact of a resulting ransomware infection could be catastrophic.
This evaluation helps you prioritize. You cannot fix everything at once, nor should you try. Focus on the high-risk, high-impact problems first. An assessment provides an actionable roadmap, turning the vague goal of improving cybersecurity in Edmonton into a series of clear, manageable steps.
To help you get started, we've created a simple table to guide you through these initial questions.
Using this checklist as a starting point will help you begin thinking like an attacker, spotting the vulnerabilities they would target first. It is the first step toward building a truly resilient defence.
For many business leaders in Edmonton, the world of cybersecurity is a maze of acronyms and technical jargon. Terms like ‘MDR’ or ‘vCIO’ are common, but it’s not always clear what they actually do for your company or why they matter.
Let's cut through the noise. Managed security services are not about just buying software and hoping for the best. It's about partnering with an expert team that delivers specific, ongoing security outcomes for your business. Think of it as having a dedicated crew protecting your digital assets 24/7, so you can focus on running your business.
This partnership is more critical than ever. The official Canadian Centre for Cyber Security site highlights that ransomware remains a dominant threat, with organized groups constantly evolving their tactics. The 2025 ransomware attack that crippled services for the Town of Devon is a stark reminder that Alberta organizations are prime targets, making a proactive defence non-negotiable.
Imagine a dedicated security team monitoring every digital entry point to your business, 24 hours a day, 7 days a week. That’s Managed Detection and Response (MDR). It is an active service that hunts for threats within your network rather than just waiting for an alarm.
An MDR team uses advanced tools and human expertise to spot suspicious activity that standard antivirus software would likely miss. When they find a potential threat, they don’t just send an alert; they investigate immediately, assess the risk, and move to contain it before significant damage is done.
For an Edmonton-based logistics company, this means an expert is always watching for signs of compromise, even at 3 a.m. This constant vigilance is what stops attacks in their tracks.
Every device connected to your network—laptops, desktops, servers, and mobile phones—is an "endpoint." Each one is a potential entry point for a cybercriminal. Endpoint Protection is like posting a dedicated security guard at every one of those entry points.
This is far more advanced than traditional antivirus software, which primarily checks for known threats. Modern endpoint protection uses sophisticated techniques to identify and block new malware, prevent unauthorized access, and stop ransomware before it can encrypt your files.
It ensures that whether an employee is working from your Edmonton office, from home, or on the road, their device is a fortress, not an open door for intruders. This layer of defence is fundamental to securing a modern, flexible workforce.
What would happen if a fire, hardware failure, or ransomware attack wiped out your critical business data? A solid Backup and Disaster Recovery (BDR) plan is the insurance policy that ensures your business can survive such a catastrophe.
This involves more than just periodic manual backups. A proper BDR solution is a complete system that includes:
This means that if your Edmonton clinic’s patient records are encrypted by ransomware, you do not have to consider paying the ransom. You can confidently restore your systems from a clean, recent backup, minimizing downtime and reputational damage. Our guide to MSSP security services explains how BDR fits into a complete security strategy.
As a business grows, it requires high-level IT leadership, but the salary of a full-time Chief Information Officer (CIO) is often out of reach for medium-sized organizations. A virtual CIO (vCIO) service provides access to that strategic expertise on a fractional basis, tailored to your needs and budget.
Your vCIO works with you to ensure your technology supports your business goals, not hinders them. They help you:
For a local manufacturing firm, a vCIO can help map out a scalable IT infrastructure to support a new production line, ensuring technology enables growth. They provide the strategic guidance needed to make smart, forward-thinking decisions that strengthen your cybersecurity in Edmonton and fuel your success.
Knowing your risks is one thing; turning that knowledge into a concrete defence plan is what truly protects your business. Many Edmonton business leaders get stuck at this stage, feeling overwhelmed by the sheer number of security tasks.
The key is to stop thinking of "getting secure" as one massive project. Instead, view it as a series of achievable, high-impact steps.
A strategic roadmap transforms cybersecurity from a vague concept into a tangible plan with clear milestones. It helps you prioritize, tackling your biggest vulnerabilities first to achieve the most significant security improvements with your available resources. This phased approach makes consistent improvement manageable.
Think of it as a continuous cycle: always working to detect new threats, protect your critical assets, and have a plan to recover quickly if an incident occurs.
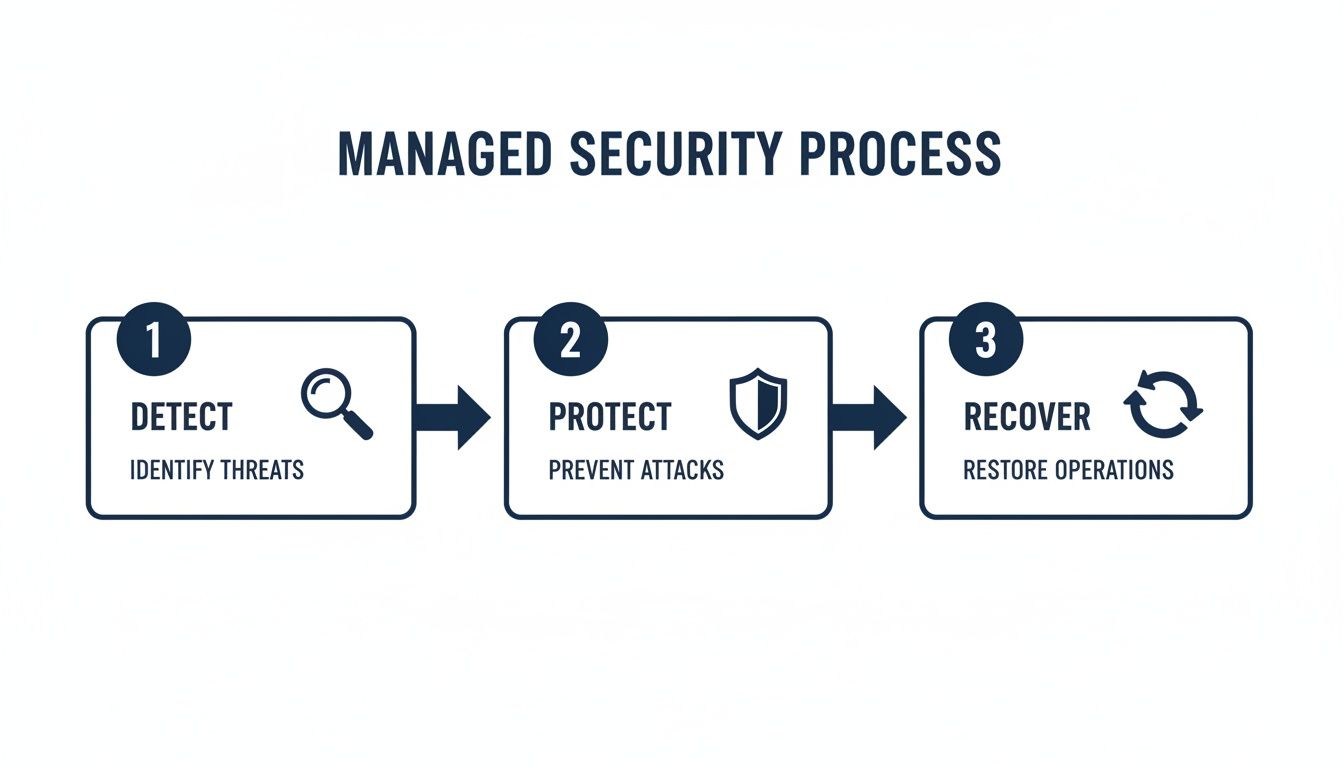
This model shows that real security isn't a "set it and forget it" task. It is a living strategy that must adapt as new challenges emerge.
This first phase is about locking the digital doors and windows most commonly left open. These foundational steps provide a significant boost to your security posture with relatively little effort.
Your immediate priorities should be:
With the basics covered, the next step is to layer on more advanced, proactive tools that actively hunt for and block threats before they can cause damage. This is where you move from basic security hygiene to building a truly robust defence.
Think of Phase 1 as installing strong locks on your doors. Phase 2 is like adding a monitored alarm system and security patrols. It elevates your defence from passive prevention to active protection.
Key actions in this stage include:
The final phase is about ensuring your business can withstand and recover from a major security incident. This is where you build true operational resilience, enabling you to bounce back quickly with minimal disruption.
Here, the focus shifts to strategic planning and testing:
Building this roadmap provides a clear path forward. It turns the complex challenge of improving your cybersecurity in Edmonton into a manageable, strategic initiative that protects your business for the long haul.
Selecting a managed services provider (MSP) is one of the most critical decisions you will make for your business. This isn't just about hiring someone to fix a slow computer; you are trusting a partner with the security, efficiency, and future of your entire operation. A great IT partner is a strategic extension of your team, helping you navigate challenges and seize opportunities.
The stakes for local businesses have never been higher. Edmonton's role in Alberta’s economy means we are on the front lines of national cyber trends. The Canadian cybersecurity market is projected to more than double to USD 46,453.3 million by 2033, with growth fuelled by escalating attacks on the sectors that anchor our city. As you can read more about these cybersecurity trends, it is clear that a proactive, expert partner isn't a luxury—it's essential.
When vetting potential providers for cybersecurity in Edmonton, your first filter should be their track record in your industry. A provider who understands the unique operational and compliance demands of local sectors—whether it's healthcare, manufacturing, or construction—will not require a crash course on your business.
Equally important is a firm commitment to data residency.
Insist on a partner with a 100% Canada-based helpdesk. For any business handling sensitive client or patient data, this is non-negotiable. It is the only way to ensure your information remains within Canadian borders, keeping you aligned with PIPEDA and other privacy laws.
A local helpdesk also means you receive support from people who understand the regional business climate, which translates to faster, more relevant solutions.
A slick sales pitch is one thing, but a capable, proactive security partner is another. You need to cut through the marketing and ask the right questions to gauge their expertise and strategic thinking.
Start with these essentials:
Finding the right MSP is a strategic investment in your company's resilience and growth. By focusing on local expertise, data sovereignty, and a proactive security mindset, you can find a partner who will not just protect your business today—they will help it thrive tomorrow. For more insights, check out our guide on choosing an MSP in Edmonton.
Navigating the world of cybersecurity can feel overwhelming, especially when trying to make smart, cost-effective decisions for your business. We receive many questions from local business and IT leaders, so we've compiled direct answers to some of the most common ones.
You will often hear benchmarks like 7-10% of the total IT budget, but this is an oversimplification. A much smarter approach is to begin with a proper risk assessment. This shifts the conversation from generic percentages to a plan that fits your specific business.
An expert partner can analyze your unique vulnerabilities and build a layered security strategy that prioritizes your most critical assets. This way, your budget is spent where it will have the biggest impact, providing a much stronger defence without waste.
Microsoft 365 includes powerful, built-in security features, but it is not a complete, set-it-and-forget-it solution. Think of it like a secure new building—the structure is solid, but you still need to lock the doors, install cameras, and monitor who has access.
Proper configuration is essential to close significant security gaps. Enforcing multi-factor authentication and, crucially, adding a dedicated third-party backup are not optional. A skilled IT partner can optimize these settings and layer on additional protections to ensure your data is truly safe.
Having a 100% Canada-based helpdesk is critical for two reasons that directly affect your Edmonton business.
First, it’s the only way to be absolutely certain your sensitive data remains within Canadian borders. This is non-negotiable for complying with privacy laws like PIPEDA and Alberta's PIPA. Keeping your data local helps you avoid the legal and reputational risks associated with international data transfers.
Second, a Canadian support team understands the local business context, which translates to faster, more effective help when you need it most. That local knowledge makes a tangible difference in the quality of support you receive.
At CloudOrbis Inc., we provide the strategic guidance and proactive support Edmonton businesses need to build a resilient and compliant security posture. Our 100% Canada-based team is ready to help you navigate your unique challenges. Secure your business with CloudOrbis today.

February 8, 2026
A Strategic Guide to Outsourced IT in Edmonton for SMBsDiscover the real benefits of outsourced IT Edmonton. This guide helps local SMBs choose the right services, understand costs, and find a reliable partner.
Read Full Post
February 7, 2026
MSP Edmonton: How to Choose the Right IT Partner for Your BusinessMSP Edmonton: Discover a proven framework to evaluate providers, decode SLAs, and secure a true IT partner for your business.
Read Full Post
February 6, 2026
A Business Guide to IT Support EdmontonUnlock business growth with the right IT support Edmonton offers. Our guide covers services, costs, and choosing the best partner for your company's needs.
Read Full Post